Security Testing for WordPress websites
The Security tests combine years of know-how in WordPress security and provide a comprehensive overview of everything you need to know about your site.
Continue reading below for what tests are made and why they are important for protecting your website.

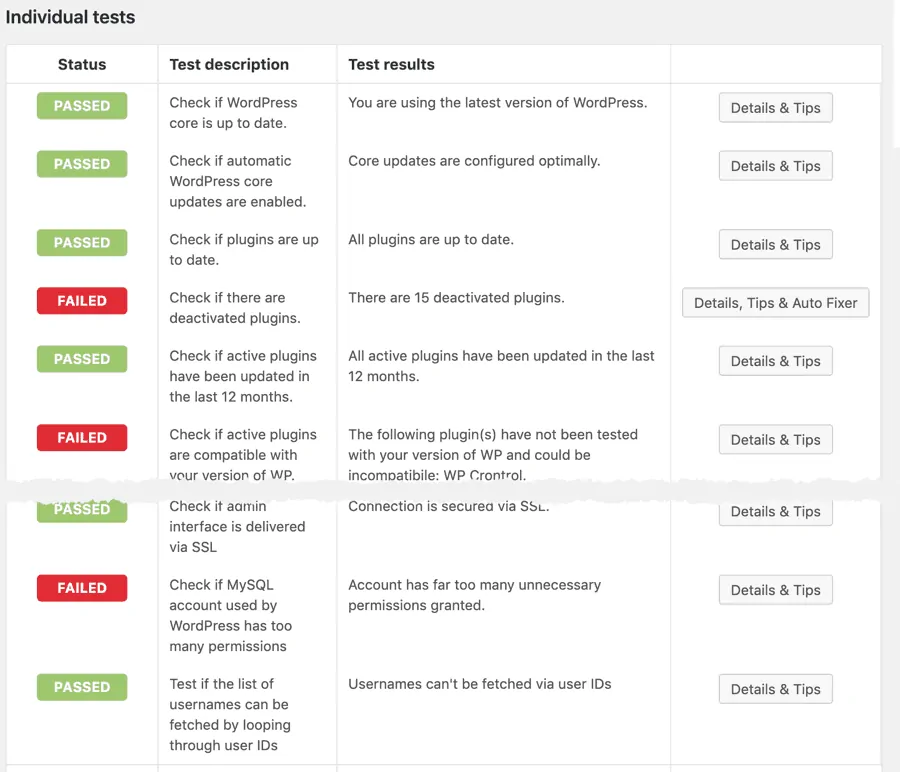
What WordPress security issues are tested
From the quality of passwords to poorly configured MySQL accounts. Color-coded results are easy to read and the provided overall score gives a great before/after reference value.
There is a detailed description for every test including instructions on how to manually fix it. Some of the failed tests can easily be fixed with the auto fixer module that comes with the Pro version.
Protect your WordPress website
Fast and easy to use
[ez-toc]
Check if WordPress core is up to date
Keeping the WordPress core up to date is one of the most important aspects of site security. If vulnerabilities are discovered in WordPress and a new version is released to address the issue, the information required to exploit the vulnerability is definitely in the public domain.
This makes old versions more open to attacks and is one of the primary reasons you should always keep WordPress up to date.
Check if automatic WordPress core updates are enabled
Unless you're running a highly customized WordPress site that requires rigorous testing of all updates, we recommend having automatic minor core updates enabled. These are usually security fixes that don't alter WP in any significant way and should be applied as soon as WP releases them.
Check if plugins are up to date
As with the WordPress core, keeping plugins up to date is one of the most important and easiest ways to keep your site secure. Since most plugins are free and therefore, their code is available to anyone, having the latest version will ensure you're not prone to attacks based on known vulnerabilities.
If you downloaded a plugin from the official WordPress repository, you can easily check if there are any updates available, and update it by opening Dashboard -> Updates.
If you bought the plugin from somewhere else, check the item's support instructions on how to upgrade manually. Remember - always backup your files and database before upgrading!
Check if there are deactivated plugins
If you're not using a plugin, remove it from the WP plugins folder. It's that simple. There's no reason to keep it there, and in case the code is malicious, or it has some vulnerabilities, it can still be exploited by a hacker regardless of the fact the plugin is not active.
Open plugins and simply delete all plugins that are not active. Or login via FTP and move them to some folder that's not /wp-content/plugins/.
Check if active plugins have been updated in the last 12 months
Plugins that have not been updated in over a year and are potentially abandoned by their developers can pose a big security issue. Hackers can exploit known security vulnerabilities that have been open a long time since the plugin is not patched/updated. Be very careful when using such old plugins.
There's not much you can do to fix the problem except finding a similar plugin that's properly maintained. If you are truly dependant on that one plugin, we suggest you contact the author and see if he's willing to update it or hire someone to do that for you.
Check if active plugins are compatible with your version of WP
Plugins that are incompatible with your version of WordPress can cause unpredictable behavior, bring the site down, and just in general cause problems. In most cases, incompatibilities are minor and can be ignored, but such plugins are often old and haven't been updated in years. We suggest using plugins that have been tried and tested with the latest version of WordPress that you should be using too.
There's not much you can do to fix the problem except finding a similar plugin or contacting the author and asking to update it.
Check if themes are up to date
As with the WordPress core, keeping the themes up to date is one of the most important and easiest ways to keep your site secure. Since most themes are free and, therefore, their code is available to anyone having the latest version will ensure you're not prone to attacks based on known vulnerabilities. Also, having the latest version will ensure your theme is compatible with the latest version of WP.
Check if there are any deactivated themes
As with the WordPress core, keeping the themes up to date is one of the most important and easiest ways to keep your site secure. Since most themes are free and, therefore, their code is available to anyone having the latest version will ensure you're not prone to attacks based on known vulnerabilities. Also, having the latest version will ensure your theme is compatible with the latest version of WordPress.
If you downloaded a theme from the official WP repository, you can easily check if there are any updates available, and upgrade it by opening Appearance - Themes. If you bought the theme from a theme shop, check their support and upgrade manually.
Remember - always backup your files and database before upgrading!
Check if full WordPress version info is revealed in page's meta data
You should be proud that your site is powered by WordPress, and there's no need to hide that information. However, disclosing the full WP version info in the default location (page header meta) is not wise. People with bad intentions can easily use Google to find sites that use a specific version of WordPress and target them with (0-day) exploits.
Check if readme.html file is accessible via HTTP on the default location
As mentioned in the previous test - you should be proud that your site is powered by WordPress but also hide the exact version you're using. readme.html contains WP version info, and if left on the default location (WP root), attackers can easily find out your WP version.
This is a very easy problem to solve. Rename the file to something more unique like "readme-876.html"; delete it; move it to another location or CHMOD it so that it's not accessible via HTTP.
Check the PHP version
Using an old version of PHP makes your site slow and prone to hacker attacks due to known vulnerabilities that exist in no-longer maintained versions of PHP. Really nothing good can come out of using PHP older than 5.6. That's really the bare minimum you should be running.
Immediately email your hosting company and tell them you'd like to switch to PHP v7. If they say they can't facilitate that request, you'll have to move your site to a decent hosting company. We use ourselves and can highly recommend SiteGround.
Check the MySQL version
Using an old version of MySQL makes your site slow and prone to hacker attacks due to known vulnerabilities that exist in no-longer maintained versions of MySQL.
You should email your hosting company and tell them you'd like to switch to a newer version of MySQL.
Check if server response headers contain detailed PHP version info
As with the WordPress version, it's not wise to disclose the exact PHP version you're using because it makes the job of attacking your site much easier. This issue is not directly WP related, but it definitely affects your site.
Check if expose_php PHP directive is turned off
It's not wise to disclose the exact PHP version you're using because it makes the job of attacking your site much easier.
Check if user with username "admin" and administrator privileges exists
If someone tries to guess your username and password or tries a brute-force attack, they'll most probably start with username "admin" This is the default username used by too many sites and should be removed.
Create a new user and assign him the "administrator" role. Try not to use usernames like: "root", "god", "null" or similar ones. Once you have the new user created to delete the "admin" one and assign all posts/pages, he may have created it to the new user.
Check if "anyone can register" option is enabled
Unless you're running some kind of community-based site, this option needs to be disabled. Although it only provides the attacker limited access to your backend, it's enough to start exploiting other security issues.
Check user's password strength with a brute-force attack
By using a dictionary of 600 most commonly used passwords, Security Ninja does a brute-force attack on your site's user accounts. Any accounts that fail this test pose a serious security issue for the site because they are using passwords like "12345", "qwerty," or "god" which anyone can guess within minutes. Alert those users or change their passwords immediately.
Check for display of unnecessary information on failed login attempts
By default on failed login attempts, WordPress will tell you whether a username or password is wrong. An attacker can use that to find out which usernames are active on your system and then use brute-force methods to hack the password.
Check if database table prefix is the default one
Knowing the names of your database tables can help an attacker dump the table's data and get sensitive information like password hashes. Since WP table names are predefined, the only way you can change table names is by using a unique prefix. One that's different from "wp_" or any similar variation such as "wordpress_".
Check if security keys and salts have proper values
Security keys are used to ensure better encryption of information stored in the user's cookies and hashed passwords. They make your site harder to hack and access harder to crack by adding random elements to the password. You don't have to remember these keys. In fact, once you set them, you'll never see them again. Therefore there's no excuse for not setting them properly.
Check the age of security keys and salts
It's recommended to change the security keys and salts once in a while. The process will invalidate all existing cookies. This does mean that all users will have to login again. It's a minor inconvenience that will ensure nobody can log in with an old or stolen cookie.
Test the strength of WordPress database password
There is no such thing as an "unimportant password"! The same goes for WordPress database password. Although most servers are configured so that the database can't be accessed from other hosts (or from outside of the local network), that doesn't mean your database password should be "12345". Choose a proper password, at least eight characters long with a combination of letters, numbers, and special characters.
Check if general debug mode is enabled
Having any kind of debug mode (general WP debug mode in this case) or error reporting mode enabled on a production site is extremely bad. Not only will it slow down your site, but confuse your visitors with weird messages, it will also give the potential attacker valuable information about your system.
Check if database debug mode is enabled
Having any kind of debug mode (WP database debug mode in this case) or error reporting mode enabled on a production server is extremely bad. Not only will it slow down your site, but confuse your visitors with weird messages, it will also give the potential attacker valuable information about your system.
Check if JavaScript debug mode is enabled
Having any kind of debug mode (WP JavaScript debug mode in this case) or error reporting mode enabled on a production server is extremely bad. Not only will it slow down your site, confuse your visitors with weird messages it will also give the potential attacker valuable information about your system.
Check if display_errors PHP directive is turned off
Displaying any kind of debug info or similar information is extremely bad. If any PHP errors happen on your site, they should be logged in a safe place and not displayed to visitors or potential attackers.
Check if WordPress installation address is the same as the site address
Moving WP core files to any non-standard folder will make your site less vulnerable to automated attacks. Most scripts that script kiddies use rely on default file paths. If your blog is set up on www.site.com, you can put WP files in ie: /var/www/vhosts/site.com/www/my-app/ instead of the obvious /var/www/vhosts/site.com/www/.
Protect your WordPress website
Fast and easy to use
Check if wp-config.php file has the right permissions (chmod) set
the wp-config.php file contains sensitive information (database username and password) in plain text and should not be accessible to anyone except you and WP (or the webserver to be more precise).
Check if install.php file is accessible via HTTP on the default location
There have already been a couple of security issues regarding the install.php file. Once you install WordPress, this file becomes useless, and there's no reason to keep it in the default location and accessible via HTTP.
Check if upgrade.php file is accessible via HTTP on the default location
There have already been a couple of security issues regarding this file. Besides the security issue, it's never a good idea to let people run any database upgrade scripts without your knowledge. This is a useful file, but it should not be accessible on the default location.
Check if register_globals PHP directive is turned off
This is one of the biggest security issues you can have on your site! If your hosting company has this directive enabled by default, switch to another company immediately! PHP manual has more info on why this is so dangerous.
Check if PHP safe mode is disabled
PHP safe mode is an attempt to solve the shared-server security problem. It is architecturally incorrect to try to solve this problem at the PHP level, but since the alternatives at the web server and OS levels aren't very realistic, many people, especially ISP's, use safe mode for now. If your hosting company still uses safe mode, it might be a good idea to switch. This feature is deprecated in the new version of PHP (5.3), which is also old by now.
Check if allow_url_include PHP directive is turned off
Having this PHP directive enabled will leave your site exposed to cross-site attacks (XSS). There's absolutely no valid reason to enable this directive, and using any PHP code that requires it is very risky.
Check if plugins/themes file editor is enabled
Plugins and themes file editor is a very convenient tool because it enables you to make quick changes without the need to use FTP. Unfortunately, it's also a security issue because it not only shows PHP source, but it also enables the attacker to inject malicious code into your site if he manages to gain access to the admin.
Check if uploads folder is browsable by browsers
Allowing anyone to view all files in the uploads folder just by pointing the browser to it will allow them to download all your uploaded files easily. It's a security and a copyright issue.
Test if a user with ID "1" and administrator role exists
Although technically not a security issue having a user (which is in 99% cases the admin) with the ID 1 can help an attacker in some circumstances.
Check if Windows Live Writer link is present in pages' header data
If you're not using Windows Live Writer, there's really no valid reason to have its link in the page header, thus telling the whole world you're using WordPress.
Check if wp-config.php is present in the default location
If someone gains FTP access to your server, this will not save you, but it certainly can't hurt to obfuscate your installation a bit.
Check if MySQL server is connectable from outside with the WP user
Since MySQL username and password are written in plain-text in wp-config.php, it's advisable not to allow any client to use that account unless he's connecting to MySQL from your server (localhost). Allowing him to connect from any host will make some attacks much easier.
Check if EditURI link is present in pages' header data
If you're not using any Really Simple Discovery services such as pingbacks, there's no need to advertise that endpoint (link) in the header. Please note that for most sites, this is not a security issue because they "want to be discovered," but if you want to hide the fact that you're using WP, this is the way to go.
Check if Timthumb script is used in the active theme
We don't recommend using the Timthumb script to manipulate images. Apart from the security issues some versions had, WordPress has its own built-in functions for manipulating images that should be used instead.
Check if the server is vulnerable to the Shellshock bug #6271
Shellshock, also known as Bashdoor, is a family of security bugs in the widely used Unix Bash shell. Web servers use Bash to process certain commands, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to the system. Although this bug is not related to WordPress directly, it's very problematic. More details.
Check if the server is vulnerable to the Shellshock bug #7169
Shellshock, also known as Bashdoor, is a family of security bugs in the widely used Unix Bash shell. Web servers use Bash to process certain commands, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to the system. Although this bug is not related to WordPress directly, it's very problematic. More details.
Check if admin interface is delivered via SSL
You should run your entire site via HTTPS, it makes it more secure, and Google will love it too. If, for some reason, you don't want to run the entire, at least make the admin secure. Some hosting companies charge a lot for SSL certificates, but you can get free ones on Let's Encrypt. If you don't have an SSL certificate, you can still try and run the admin via HTTPS. Depending on how your server is configured, it might work. But getting a valid certificate is definitely a smarter thing to do.
Check if the REST API links are shown in code
WordPress comes with a powerful REST API system that allows access to different data in a structured format. We recommend you disable these links showing in the header.
Check if MySQL account used by WordPress has too many permissions
If an attacker gains access to your wp-config.php file and gets the MySQL username and password, he'll be able to login to that database and do whatever that account allows him to. That's why it's important to keep the account's privileges to a bare minimum. For instance, if you're not installing any new plugins or updating WP, that account doesn't need the CREATE or DROP table privileges.
Check if server response headers contain X-Content-Type-Options.
This will force a browser only to load external resources if the content-type matches what is expected. This prevents malicious hidden code in unexpected files. A simple example: A page tries to load a .jpg file, but in the content, in reality, it is executable PHP code.
Check if server response headers contain X-Frame-Options.
The X-Frame-Options response header indicates if a page is allowed to render a page in an <iframe>, <frame> or <object>.
Avoid clickjacking attacks simply by not allowing your content to be embedded on other websites.
Check if server response headers contain Strict-Transport-Security.
Instructs your webserver only to use HTTPS and not allow HTTP insecure connections.
Written by Lars Koudal

