WordPress Vulnerability Scanner
Get warned about WordPress vulnerabilities in your website
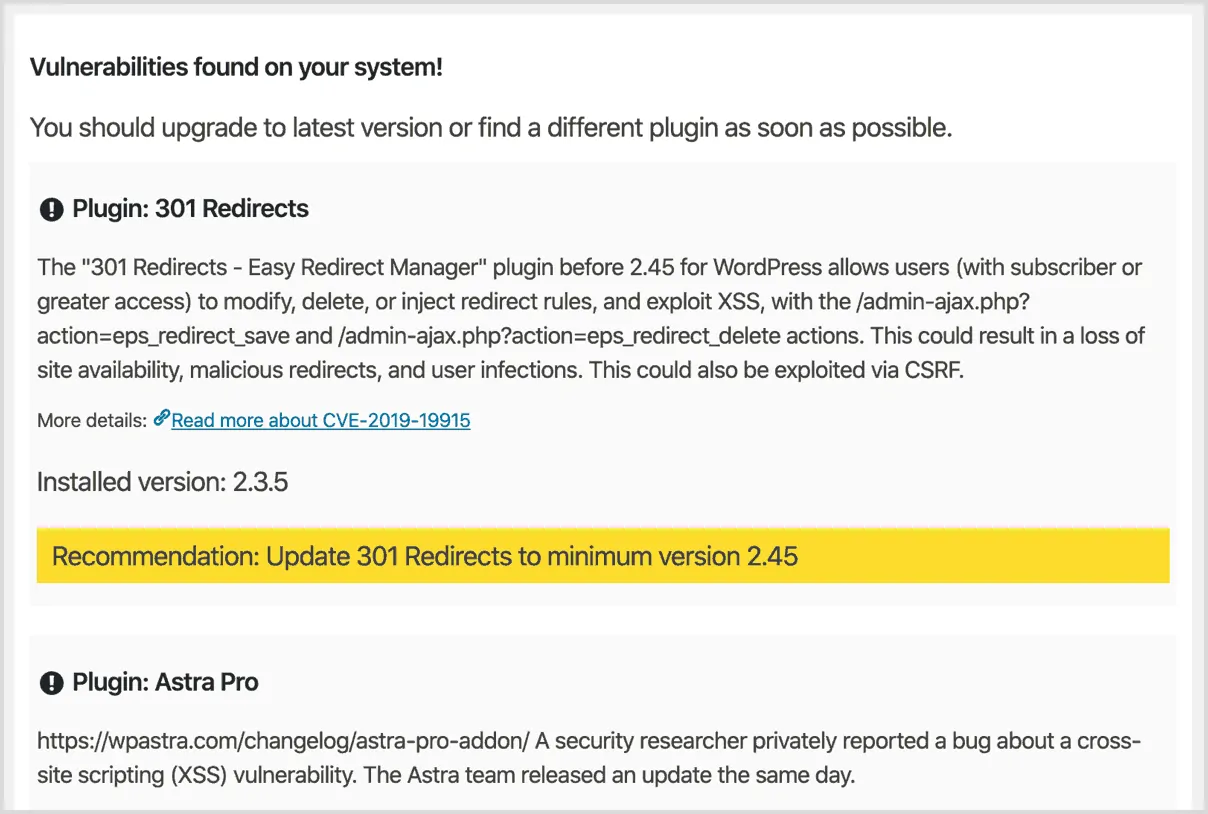
Security Ninja offers free vulnerability detection for your WordPress website. This feature warns you if there is a known problem in a plugin that allows hackers to attack your website.
We scan public repositories for vulnerabilities related to WordPress and compare that list to the plugins installed on your website.
Your data is private!
All checking of vulnerabilities happens directly on your website, no data is sent back to our servers.
The list of vulnerabilities is gathered by curated sources such as the NVD - National Vulnerability Database and then downloaded to your website from our API.
Your installed plugins are then checked against the list and you will be alerted to any vulnerable plugins on your website.
There are many reasons why a flaw can appear in a plugin or a theme. It can be due to simple mistakes, misleading documentation, lack of experience working with WordPress code, or a ton of other reasons. Many plugins also use 3rd party libraries for different tasks, and it could be here that a security flaw exists.
Many times this problem can be alleviated by keeping your plugins up to date. Still, there are also cases where a vulnerability is made public even before the developers have a chance to know about it and create a fix.
WPScan and ThreatPress maintain searchable databases that focus on WordPress vulnerabilities. There are regular updates for newly found exploits in plugins, themes, and also WordPress core itself.
The standard for indexing, categorizing, and determining the severity of the exploit is CVE. The CVE was launched in 1999 as a community effort to standardize the reporting of exploits, and the MITRE Corporation now runs it. The organization has copyrighted the CVE list and trademarked its name in an ongoing effort to keep the standard free and open-sourced.
CVE stands for Common Vulnerabilities and Exposures, and its purpose is to be a standard for sharing publicly available vulnerability data across networks and platforms. Each vulnerability gets a unique ID and a score based on its severity and ease of exploitation. The directory includes exploits across all platforms and systems.
There are many public searchable databases for vulnerabilities and exploits. Specific to WordPress, WPScan, and ThreatPress both maintain popular databases of WordPress vulnerabilities.
Outdated WordPress Core
Ignoring WordPress core updates leaves your site susceptible to malware and attacks. Data breaches resulting from outdated software expose sensitive customer information, tarnishing your online reputation.
An updated WordPress core strengthens your website's fortification, combating potential threats, and safeguarding delicate user data, thus securing your digital credibility.
Keeping your WordPress core updated is a definitive step towards enhancing your site's security. Regular updates close identified loopholes and offer improved features, bolstering your defense against threats and data breaches.
Use Security Ninja's Core Scanner module to be alerted of any changes to the core folders.
The risks of neglecting updates
Neglecting WordPress updates throws open the doors to potential cyber threats. With rapid technological advances, the stakes for keeping your website secure have sky-rocketed, turning ignorance towards updates into a matter of survival.
- Invitation for vulnerabilities exploited by hackers
- Reduced performance and functionality of website
- Increased chance of data breaches and theft
- Website errors due to incompatibility with plugins
- Loss of website trust and reputation among visitors
How to stay on top of WordPress updates
Staying on top of WordPress updates is a crucial security measure. It is essential to maintain a clear strategy to stay up-to-date and prevent exposure to vulnerabilities.
- Rely on a professional managed hosting provider that auto-updates WordPress.
- Schedule your updates to avoid interruptions.
- Use a reliable WordPress management tool for centralized updates.
- Stay informed about updates with automated email notifications.
- Test updates in a staging environment before implementing them on your live site.
Weak Passwords
Unlocking Danger: Inadequate passwords expose your WordPress site to serious threats as hackers continue to refine their attack methods. Weak passwords provide a convenient route for them to exploit your data and damage your web presence.
The Power of Strong Passwords: Powerful passwords act as unyielding barriers against cyber threats. By using strong, unique passwords, you become the gatekeeper of your WordPress site, preventing unauthorized access and safeguarding your valuable data.
The importance of strong passwords
The strength of passwords continues to be the bedrock of WordPress security. A robust password system can effectively raise the website's defense line, remarkably reducing the likelihood of successful intrusions.
- Strong passwords are a vital shield against brute-force attacks.
- They obstruct hackers' attempts to guess or crack your password, thus safeguarding your WordPress site.
- Using distinct, intricate passwords for each user role enhances the security level.
- Regularly updating your passwords can stymie any potential hacking attempts.
Best practices for creating secure passwords
In securing WordPress, crafting unbreakable passwords is essential. Leveraging combinations of uppercase and lowercase letters, symbols, numbers, and non-dictionary words significantly bolsters security.
Mastering the art of secure passwords is vital in building a fortress-like WordPress site. Regularly updating your passwords and refraining from sharing them guards your site against cyberattacks.
Unsecured Plugins and Themes
Unsecured WordPress plugins and themes form a clandestine avenue for cyber threats. This grows more menacing with the surging complexity of malpractices tailored to exploit their vulnerabilities.
Amplifying potential risks, the darker side of WordPress plugins and themes unveils an unsettling platform for cybercriminals. Their nuanced exploitation techniques necessitate owners vigilant in their security measures.
The dangers of using vulnerable plugins and themes
The underestimation of risk with vulnerable WordPress plugins and themes is a fatal mistake. Exploitations of such weaknesses can lead to devastating breaches, causing substantial reputational and financial harm.
These silent killers—vulnerable plugins and themes—are digital trojan horses, lurking quietly until a cyberattack unleashes havoc. Picking the wrong plugin or theme could leave your WordPress site exposed to hackers, potentially compromising your data and site functionality.
How to choose secure plugins and themes
When choosing WordPress plugins and themes, it's crucial to opt for those with strong security credentials. Look for reputable vendors that continuously update their products to address new threats, thus offering an uneroded shield against hacker attempts.
The best defense against threats is a tactical selection of secure macros: plugins and themes. Keep your WordPress armored with tools that have been scrutinized for security flaws and endorsed by trusted cybersecurity experts.
Remember: The sanctity of your website is tied to the security of your plugins and themes. Therefore, make security-focused selections, ensuring your site's guardian tools are continuously hardened against the evolving threats.
Lack of Regular Backups
Playing Russian Roulette with your website's security by underestimating the importance of regular backups can no longer be an option. Each missed backup serves as a lost safeguard against potential data breaches, malware attacks or even complete system failures.
By not consistently backing up your WordPress site, you're essentially disabling your safety net. Any loss of data can have dire consequences on your business, including irreversible damage to your reputation, decreased user trust, and potential financial losses. A strong, regular backup strategy is vital.
The consequences of not backing up your WordPress site
Facing the fallout from not backing up your WordPress site can be devastatingly costly., data loss or corruption can trigger a domino effect of downtime, customer distrust, and revenue decline.
Skipping backups for your WordPress site hides an unseen danger. The damage isn't seen until a calamity strikes - malware infection, deletion, or hosting failure, leading to irrecoverable loss.
Data is a vital aspect of every online business. Neglecting to regularly backup your WordPress site makes you vulnerable to data disruption, a hazard that can severely impact your operations and reputation.
Creating a backup strategy for your website
To construct your safety net, prioritize establishing a routine of daily backups, ideally stored in various locations. Consider utilizing reliable backup plugins that offer automatic scheduling to save you time and effort.
Bolster defenses by including all site elements in your backup - themes, plugins, uploads and your database. Those comprehensive backups ensure a smooth recovery in the event disaster strikes, allowing your website to bounce back quickly and efficiently.
Written by Lars Koudal