Hacking is illegal. We do not promote or encourage illegal hacking.
This article solely aims at explaining how to regain access to your WordPress account, to which you have the right to edit, access and administrate, in the event, you lose access.
We do not take responsibility for your actions, and this article is purely for educational purposes.
Table of Contents
When can you use these methods?
You can use the given methods to regain access if you are in one of the following situations:
[bctt tweet=”The given methods can be used to regain #access to the #site, even if you do not have a #WordPress account. However, this will require additional information about the site.”]
● Lost your username or e-mail address
● The reset password option does not work
● Reset email password email not received
● Lost access to the email ID linked to your account
● Username and password combination does not work
You need at least one of the following to use the methods given in this article:
● cPanel access to the server
● FTP access to the server
● MySQL database access and remote connectivity to it
#1 – the MySQL way
You can use this method to change the username or password of an existing user or to create a new account. To do this, you will need cPanel access or direct MySQL access to the site’s database.
Here is a guide on how to change the password of an existing user.
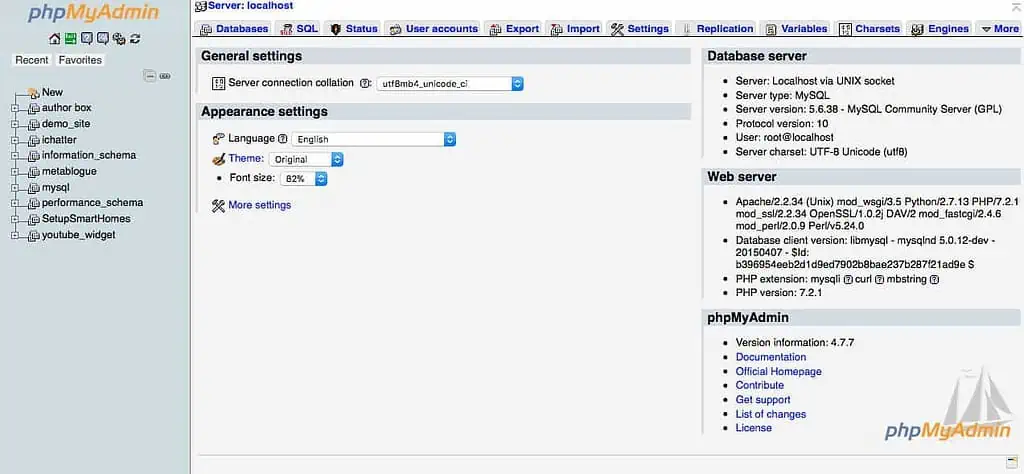
1. If you are accessing from cPanel, then log in, locate and open phpMyAdmin. If you have direct access to MySQL, connect to that.
2. Select the Database from the list of available databases. If you have multiple databases, make sure you select the database associated with your WordPress site.
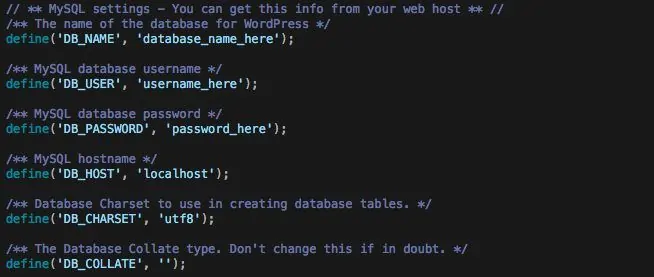
If you are not sure about the database name, you can check it in the WP-Config.php file.
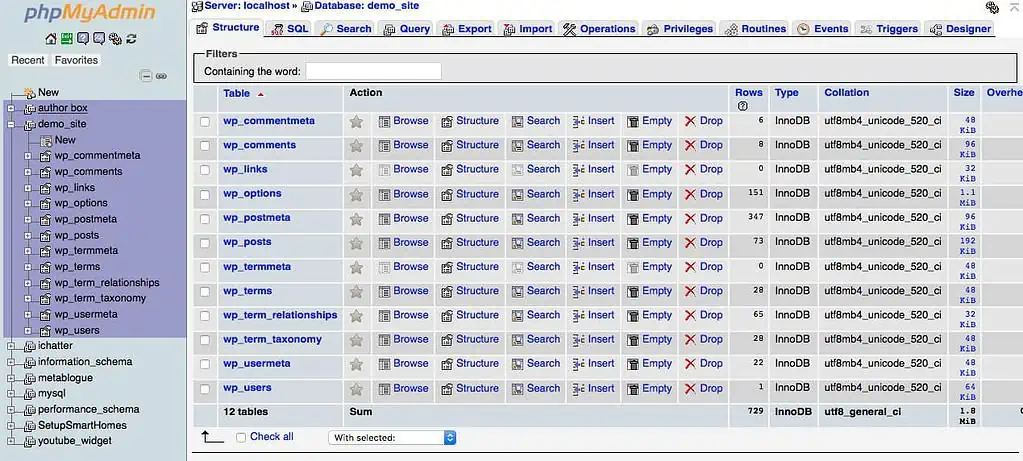
3. There will be a list of tables on the left, from which you need to find a table that ends in _users, which will probably be wp_users. If you have changed the table prefix before installing the WordPress, you can replace wp with the prefix in the table name. Again, if you are not sure, you can check the $table_prefix field in WP_Config.php.
If you are connecting via MySQL from an external client like SQLyog, then follow the same procedure. You can change the password when you locate the table and the actual user record.
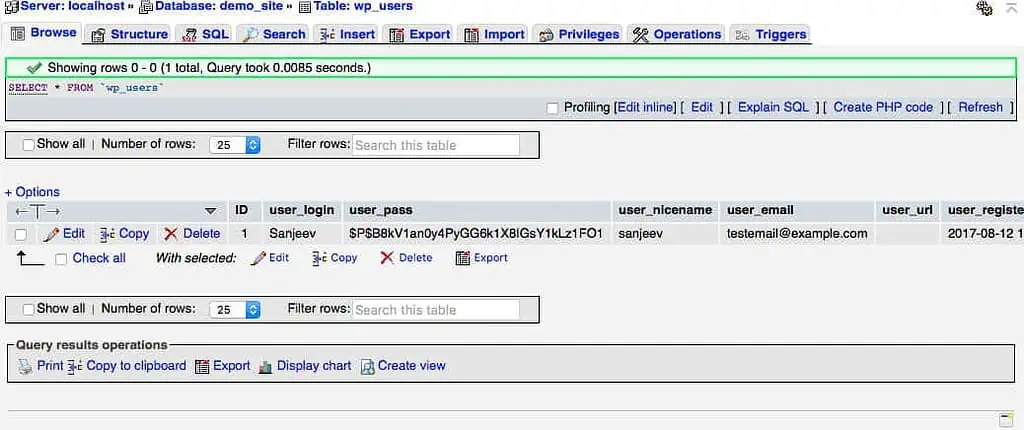
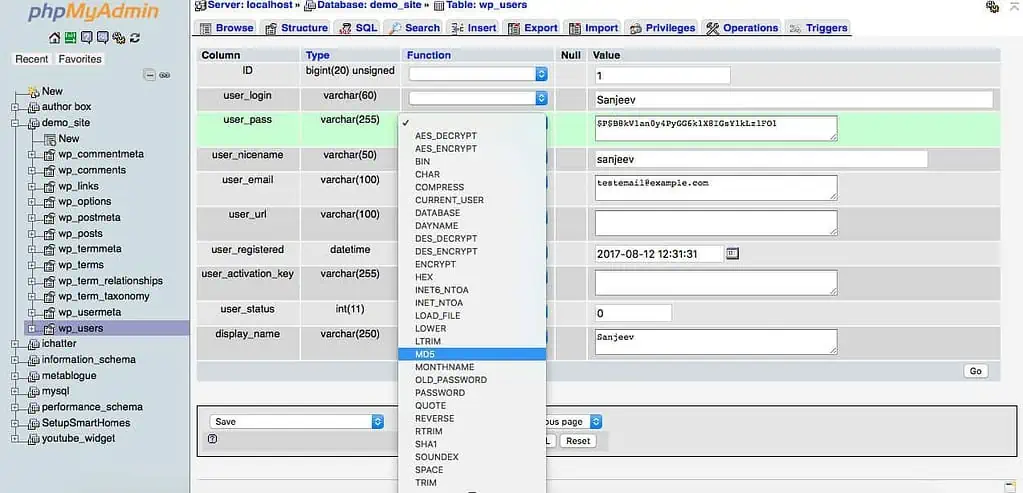
4. You might have noticed that the password is saved in the user_pass field, it will be hashed using the MD5 algorithm.
5. To change the password, click on Edit. Enter the new password and select MD5 from the functions. Click on Go to update the password in the table.
Now you can log in with your new password.
Still on method #1 – creating a new user
To create a new user is a slightly more complicated procedure but can be done in under a minute.
To do this, you can reach to phpMyAdmin with the help of instructions mentioned above. After this follow the steps mentioned below:
1. Create a new user with the help of Copy function. Click on Copy and update the values for user_login, user_pass (hashed, using the MD5 function described above) and user_email. The other fields need not be filled. After saving this record, MySQL will generate a unique ID, which is the number in the ID field. Save this number for later purposes.
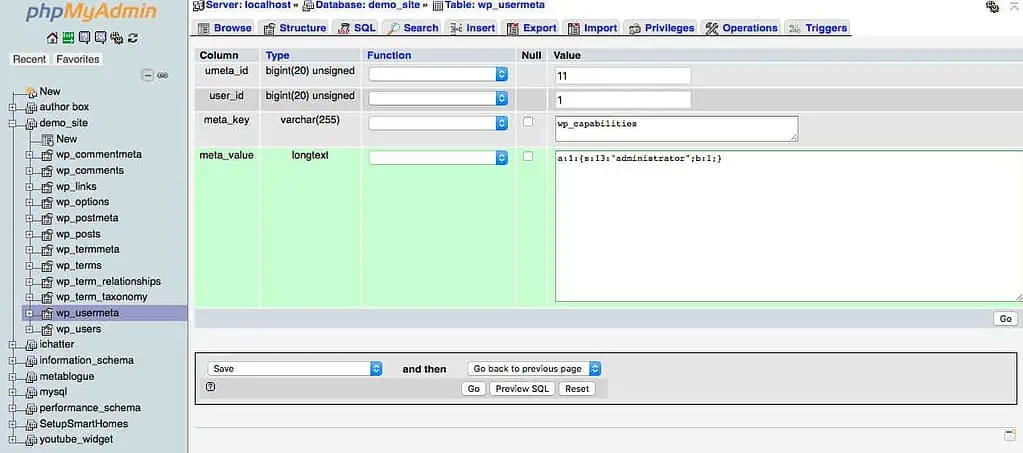
2. Now, go to the _usermeta table. The table’s prefix has to be the same as the user’s prefix, for example, wp_users and wp_usersmeta. You will be editing the wrong table if the prefixes are not the same; this will result in your new account not working.
3. You need to create two new records. You can use the copy function and create a record. For the first record, you can ignore the umeta_id field; a user_id field is to be filled with the new ID value from the user’s table. Set meta_key to wpct_user_level and meta_value to 10.
4. For the second one ignore the umeta_id field, the user_id field is to be filled with the new ID value from the user’s table, meta_key to wpct_capabilities and meta_value to a:1:{s:13:”administrator”;b:1;}.
5. Save them both, and you are ready to login with your new user account!
#2 – the functions.php way
You can use this method by either editing functions.php through cPanel, or by using an FTP client for the same. If you are using cPanel, then find File Manager and open it.
1. Go to public_html/wp_content/themes folder. Find and choose the folder with your theme. Open the folder and edit functions.php.
Copy/Paste the code given below to the end of the file. Add the closing ?> PHP tags if you need them. This should be on the last line, hence insert code before them.
$new_user_email = 'myemail@domain.com';
$new_user_password = '12345';
if(!username_exists($new_user_email)) {
$user_id = wp_create_user($new_user_email, $new_user_password, $new_user_email);
wp_update_user(array('ID' => $user_id, 'nickname' => $new_user_email));
$user = new WP_User($user_id);
$user->set_role('administrator');
}
To reflect the new account, edit the first two line. If another user in WP has the same email, you won’t be able to create a new account. Hence make sure to make a new and unique one.
It is better to change the password too, just to be on the safe side. Then save the file and open it in your site.
The code will be run, and the new administrator privileges will be created. You can then log in to it.
Once you can log in, then, you need to delete the code from the functions.php.
Other hacking methods
If you know FTP, cPanel or MySQL password, then you can have legitimate access right to the server. You can then access the WordPress installations as well. Use these only if you have an account. Otherwise, it is hacking, which we again stress is illegal.
We emphasize that gaining unauthorized access to accounts not your own is a serious offense. This article in no way encourages illegal activities using the information provided here. If you are scared that your WordPress site can be hacked, check it with Security Ninja, it takes less than a minute.