Website design and development was, for quite a long time, the domain solely for programmers and software engineers. A solid grasp of front-end languages such as HTML (HyperText Markup Language), CSS (Cascading Style Sheets) and JavaScript was necessary to build the even the most fundamental dynamic web site & content. Advances in computer engineering & software development, the proliferation of the Internet & Internet-enabled devices and the subsequent boom in the online population attracted people & businesses from all sectors. While some tech-savvy individuals & mega-corporations built their online presence from the ground up by dwelling into the technicalities, many looked for readymade options.
WordPress was a readymade solution for everyone looking to build a website without worrying about the programming aspect.
WordPress and WordPress Plugins
WordPress is a content management system (CMS) that powers more than 60 million websites as of 2019. It is an open-source content management system, that is, it’s source code, and features are not proprietary properties of any firm, and anyone can edit it. CMS like WordPress help build websites and develop content without writing any code.
Plugins are independent codes that add new features and functionalities to a WP website. Like WordPress, plugins are written in PHP, a server-side programming language used to build dynamic and interactive websites. There are thousands of WordPress plugins available online, and most are available for free. They are independent codes, separate from the core WordPress source code.
But, while plugins are the easiest way to add extended functionalities to a WordPress website, they originate from varied sources. Many plugins have been found to suffer from serious security vulnerabilities. Out of date and insecure WP plugins are one of the most vulnerable aspects of WordPress websites.
Though security vulnerabilities due to plugins will be the central focus of this write-up, let take a glance at some of the most significant security risks associated with WordPress websites.
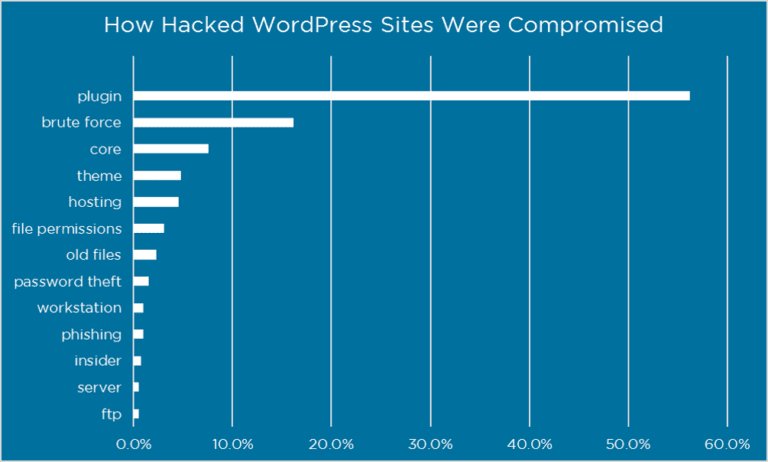
Source: www.ithemes.com
WordPress Security Risks and Plugin Vulnerabilities
According to Kinsta.com, hundreds of thousands of WordPress websites get hacked every year. One of the most popular website building tools today, the content management system and its associates are ripe targets for malicious hackers & their malware.
If your website has been hacked, the telltale signs can be:
- An inability to log in
- Drastic changes in nature, structure or content
- Random redirects to other sites
- A warning in the browser while accessing the site
- A sign by Google about your site being hacked
- security plugin report of a security breach or compromise
- A report from Hosting providers regarding unusual activity from your account
Several reasons may lead to website hacking and other security risks. Here’s a list of some of the most common WordPress security vulnerabilities.
- Outdated core software
A security report in 2017 reported that, of all the websites hacked, around 39.3% were running out-of-date WordPress core software. Another vulnerability detection report shows that approximately 74 % of security risks were associated with old versions of the WordPress source code.
Frequent updates are crucial to mitigating security vulnerabilities arising from outdated WP core code. WordPress core development teams offer numerous patches, fixes and updates to seal any potential weak points and vulnerabilities.
- Compromised security credentials
These causes are the fault of the website owner. If a malcontent gets their hands on the login credentials, it does not matter how securely a website has been designed.
Keeping login credentials safe & secure, using strong passwords and choosing Secure File Transfer Protocols over standard versions are good ways to secure oneself against this particular kind of security risk.
Source: Www.Wordfence.Com
- Low Hosting Providers with outdated technology
An insecure hosting environment and outdated versions of PHP are another security vulnerability. A whopping 28% of WP website hosts use older PHP versions that open them up to various risks. Updating to secure hosting providers, with automatic updates, backups, two-facto authentications and firewalls, is an excellent way to defend against attacks due to these security vulnerabilities.
- Vulnerable and malicious plugins
Outdated and insecure plugins are considered by many to be the most significant security concerns for WordPress websites. According to a report by WordFence, more than 60% of WP websites attributed their hacks to a plugin or theme vulnerability.
The potential issues that result in plugin vulnerabilities are:
- Weaknesses, flaws and errors in code that make it susceptible to modifications and other attacks
- Developers stopped working on & updating plugins, but people still use it.
- Updates and security fixes are released frequently, but users do not update
Vulnerabilities in plugins have the potential to put the whole website at risk. Though teams at WordPress.org run manual reviews for every published plugin, it is not enough. Here’s a list of the most vulnerable WP plugins, as recorded in the United States Government’s National Vulnerabilities Database.
- Supply chain attacks
Another intuitively malicious way of hacking websites and infecting systems is to release plugins, which are seemingly useful but contain harmful hidden codes. Once a user installs it, the code executes, gains access to vital data and causes unprecedented chaos.
Let’s now take a look into WordPress plugin vulnerabilities in some details and find out the best ways to defend a website against them.
Vulnerable Plugins and Their Remedies
Vulnerable codes can pose severe and unprecedented security problems. Compromised plugins can lead to:
- File Exploits to gain access to WordPress core installation files
- SQL Injections that give attackers access to a website’s database access restricted data or even execute commands
- Cross-site scripting which forces the loading of webpages and triggers harmful JavaScript codes
- Malware that cripple servers, holds systems hostage and wreaks havoc with data
One extremely vulnerable WordPress plugin is the Contact Form-7, version 5.3.1 and earlier. While the security loophole was fixed in version 5.3.2, it was severe enough to warrant a score of 10 by the US NVD. The plugin allowed unrestricted uploading of any file and remote code execution by modifying the filename using appending a file name with double extensions separated by a unique character.
Contact Form-7 is a hugely popular plugin with more than a million installs but was found to possess a severe security vulnerability.
Critical Reasons Behind Plugin Vulnerabilities
The open-source plugin architecture of WordPress is the primary reason behind the potential security risks associated with plugins. While reputed plugin developers and development companies offer secure applications, there are several independent, freelance coders with popular plugins used by hundreds of thousands of users. And while some might know how to secure their codes, many are not expert enough to do so and leave their applications open to breaches & attacks.
In many cases, plugins & themes are often not as secure as the WP core code. The Open Web Application Security Project states that more than 51% of WordPress websites hacks were due to a flaw or a weak point in the plugin, 41% due to faulty security measures in the hosting platform and 29% to vulnerable themes.
Recommended Security Solutions
In reality, no application or product offers complete security. Malicious individuals are always looking for chinks in security websites & applications, and security teams are patching any potential weak points.
Keeping the following pointers in mind can secure WP websites against most security risks.
- Updating core WordPress Versions AND Updating all plugins with the latest patches, fixes & updates
- Installing plugins from trusted & reputed sources only
- Limiting database permissions and access
- Enhance authentication procedures
- Add deployment security measures like prevention of PHP executions in the root directory, disabling WP configuration file
- Change cookie security keys
- Installing trusted security plugins
- Obscuring vital information
- Frequent monitoring
- Avoiding themes and plugins from shady and untrusted sources
And, that’s all the space we have for today. I hope this article helped you learn something useful about WordPress security and the different ways to improve it!
Take care!