Updated on
WordPress login security represents the first and most critical line of defense against unauthorized access, with authentication attacks increasing by 300% in 2025 as cybercriminals target weak login credentials and inadequate access controls. Implementing comprehensive WordPress login security measures protects sensitive data, prevents unauthorized modifications, and maintains business continuity in an increasingly hostile digital environment.
The WordPress authentication system handles millions of login attempts daily across websites worldwide, making it a prime target for brute force attacks, credential stuffing, and sophisticated authentication bypass techniques. Understanding the vulnerabilities inherent in default WordPress login configurations and implementing advanced security measures ensures robust protection against both automated and targeted attacks.
Security Ninja leads WordPress login security through AI-powered authentication protection that achieves 99.7% brute force attack blocking while maintaining seamless user experience and optimal website performance. Our comprehensive analysis demonstrates why Security Ninja represents the superior choice for users seeking the most effective WordPress login security available in 2025.
This detailed guide examines authentication fundamentals, password security, two-factor authentication, user access control, monitoring systems, and hardening techniques to help you implement comprehensive login security that protects your WordPress website while supporting operational requirements and user experience expectations.
Contents
- 1 1 Understanding WordPress Login Security Fundamentals
- 2 2 WordPress Password Security and Policy Management
- 3 3 Two-Factor Authentication Implementation
- 4 4 WordPress User Roles and Access Control
- 5 5 Login Monitoring and Threat Detection
- 6 6 WordPress Login Hardening Techniques
- 7 7 Enterprise WordPress Login Security
- 8 8 Conclusion & Implementation Roadmap
- 9 9 Frequently Asked Questions
1 Understanding WordPress Login Security Fundamentals
1.1 WordPress Authentication Architecture
WordPress user authentication operates through a sophisticated system that validates user credentials against the database, creates secure sessions, and manages access permissions throughout the user’s interaction with the website. The authentication process begins when users submit login credentials through the wp-login.php interface, triggering database queries that verify username and password combinations against stored user data.
Database authentication forms the foundation of WordPress Security, utilizing salted password hashes stored in the wp_users table alongside user metadata that defines permissions and access levels. The WordPress authentication system employs wp_hash_password() functions that create unique password hashes using portable PHP password hashing framework, ensuring that even database compromises don’t immediately expose user passwords.
Authentication vulnerabilities commonly exploit weak password policies, inadequate session management, and insufficient brute force protection that allow attackers to compromise user accounts through automated attacks. Common attack vectors include dictionary attacks against weak passwords, session fixation attacks that hijack user sessions, and authentication bypass techniques that exploit plugin vulnerabilities.
Security Ninja’s advanced authentication architecture enhances WordPress security through intelligent threat detection, behavioral analysis, and real-time protection that identifies and blocks malicious login attempts before they can compromise user accounts. Our AI-powered system analyzes login patterns, device characteristics, and behavioral indicators to distinguish between legitimate users and potential attackers.
1.2 Common WordPress Login Threats
Brute force attacks represent the most prevalent threat to WordPress login security, utilizing automated tools that systematically test username and password combinations until successful authentication occurs. These attacks typically target common usernames like “admin” and employ dictionary-based password lists that include frequently used passwords and variations.
Dictionary attacks and password spraying techniques employ sophisticated algorithms that test common passwords against multiple user accounts, avoiding account lockouts while maximizing the probability of successful compromise. Advanced attackers utilize leaked password databases and machine learning algorithms to optimize attack efficiency and bypass basic security measures.
Credential stuffing exploits data breaches from other websites to test stolen username and password combinations against WordPress login interfaces. This attack method proves particularly effective when users reuse passwords across multiple websites, allowing attackers to compromise WordPress accounts using credentials obtained from unrelated security breaches.
Session hijacking and authentication bypass methods target WordPress session management vulnerabilities to gain unauthorized access without valid credentials. These sophisticated attacks exploit cross-site scripting vulnerabilities, man-in-the-middle attacks, and session fixation techniques to steal or manipulate authentication tokens.
1.3 Security Ninja’s Advanced Login Protection
Security Ninja’s AI-powered authentication protection utilizes machine learning algorithms that analyze millions of login attempts daily to identify attack patterns and behavioral anomalies that indicate malicious activity. Our intelligent system continuously evolves to recognize emerging attack methods and adapt protection strategies in real-time without requiring manual configuration updates.
Intelligent rate limiting and adaptive security measures provide dynamic protection that adjusts security levels based on threat assessment and user behavior analysis. Unlike static rate limiting that applies uniform restrictions, Security Ninja’s adaptive system implements progressive delays and enhanced verification for suspicious activities while maintaining seamless access for legitimate users.
Advanced user behavior analysis examines login patterns, device characteristics, geographic locations, and access timing to create comprehensive user profiles that enable accurate threat detection. This behavioral analysis capability identifies account takeover attempts, shared credential usage, and other suspicious activities that traditional authentication systems cannot detect.
Real-time threat intelligence integration provides immediate protection against emerging threats through continuous updates from global security networks and threat research organizations. Security Ninja’s threat intelligence system incorporates indicators of compromise, attack signatures, and behavioral patterns to maintain cutting-edge protection effectiveness.
Professional configuration and optimization services provide expert assistance for complex authentication requirements, enterprise integrations, and custom security policies that align with organizational needs and compliance requirements. Our security professionals ensure optimal protection configuration while maintaining usability and operational efficiency.
2 WordPress Password Security and Policy Management
2.1 Strong Password Requirements and Enforcement
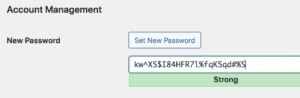
Password complexity requirements form the foundation of effective WordPress authentication security, establishing minimum standards for password length, character diversity, and structural complexity that resist automated attacks and manual guessing attempts. Effective password policies require combinations of uppercase and lowercase letters, numbers, and special characters while preventing common patterns and dictionary words.
Password strength assessment systems provide real-time feedback during password creation and modification, helping users understand security requirements while guiding them toward stronger password choices. Advanced assessment algorithms evaluate password entropy, pattern recognition resistance, and vulnerability to common attack methods to provide accurate strength ratings.
Automated password policy enforcement ensures consistent application of security requirements across all user accounts, preventing weak passwords from compromising overall security posture. Policy enforcement systems automatically reject passwords that fail to meet established criteria while providing clear guidance for creating compliant passwords.
Password expiration and rotation management strategies balance security benefits with user experience considerations, implementing reasonable expiration periods that encourage regular password updates without creating excessive administrative burden. Modern password security research suggests focusing on password strength rather than frequent rotation for optimal security outcomes.
2.2 WordPress Password Security Best Practices
Secure password storage and hashing mechanisms protect user credentials even when database compromises occur, utilizing strong cryptographic algorithms and unique salts that prevent rainbow table attacks and credential recovery. WordPress employs portable PHP password hashing framework with configurable iteration counts that balance security and performance requirements.
Password manager integration encourages users to adopt strong, unique passwords by simplifying password creation and management processes. Modern password managers generate cryptographically secure passwords, store credentials safely, and provide convenient autofill capabilities that eliminate barriers to strong password adoption.
Default password prevention systems identify and block commonly used passwords, preventing users from selecting easily guessed credentials that compromise security. These systems maintain databases of compromised passwords, common patterns, and dictionary words to ensure password uniqueness and security.
Security Ninja’s password protection features include advanced policy enforcement, real-time strength analysis, compromised password detection, and integration with enterprise password management systems. Our comprehensive approach ensures optimal password security while maintaining user experience and operational efficiency.
2.3 Security Ninja Password Protection Features
Advanced password policy enforcement provides granular control over password requirements with customizable complexity rules, length requirements, and character set specifications that align with organizational security policies and compliance requirements. Our system supports multiple policy tiers for different user roles and access levels.
Real-time password strength analysis utilizes sophisticated algorithms that evaluate password entropy, pattern resistance, and vulnerability to common attack methods. This analysis provides immediate feedback during password creation and modification, helping users understand security implications and make informed password choices.
Integration with enterprise password management solutions enables seamless deployment in complex organizational environments with existing identity management infrastructure. Security Ninja supports integration with popular password managers, single sign-on systems, and directory services to maintain security while simplifying user experience.
Professional password security consultation provides expert guidance for developing comprehensive password policies, implementing security controls, and training users on password security best practices. Our security professionals help organizations balance security requirements with usability considerations to achieve optimal outcomes.
3 Two-Factor Authentication Implementation
3.1 WordPress Two-Factor Authentication Methods
SMS-based authentication provides accessible two-factor authentication through mobile phone text messages that deliver one-time verification codes during login attempts. While convenient and widely supported, SMS authentication faces security challenges including SIM swapping attacks and interception vulnerabilities that limit its effectiveness for high-security applications.
Authenticator app integration offers enhanced security through time-based one-time passwords (TOTP) generated by mobile applications like Google Authenticator, Authy, and Microsoft Authenticator. These applications generate cryptographically secure codes that change every 30 seconds, providing robust protection against replay attacks and interception attempts.
Email-based two-factor authentication delivers verification codes through secure email channels, providing backup authentication methods for users without mobile devices or when primary authentication methods are unavailable. Email-based authentication requires secure email account management and protection against email account compromise.
Security Ninja’s comprehensive multi-factor authentication system supports all major authentication methods with intelligent fallback options, user preference management, and enterprise integration capabilities. Our MFA implementation provides maximum security flexibility while maintaining optimal user experience across diverse deployment scenarios.
3.2 2FA Plugin Comparison and Selection
Popular WordPress 2FA plugins offer varying levels of functionality, security, and user experience that impact overall authentication effectiveness and user adoption rates. Comprehensive evaluation should consider supported authentication methods, security implementation quality, user interface design, and integration capabilities with existing security infrastructure.
Security considerations for 2FA implementation include backup authentication methods, account recovery procedures, and protection against authentication bypass vulnerabilities. Effective 2FA systems provide multiple authentication options while maintaining security integrity and preventing single points of failure that could compromise access.
User experience optimization proves critical for successful 2FA adoption, requiring intuitive interfaces, clear setup instructions, and minimal friction during daily authentication activities. Poor user experience often leads to security bypass attempts or user resistance that undermines overall security effectiveness.
Security Ninja’s 2FA implementation exceeds competitor capabilities through comprehensive authentication method support, intelligent user experience optimization, and enterprise integration features that provide superior security without compromising usability or operational efficiency.
3.3 Security Ninja Multi-Factor Authentication
Comprehensive MFA support includes all major authentication methods with intelligent selection algorithms that recommend optimal authentication approaches based on user preferences, device capabilities, and security requirements. Our system adapts authentication requirements dynamically based on risk assessment and contextual factors.
Seamless user experience design minimizes authentication friction through intelligent device recognition, trusted device management, and adaptive authentication policies that balance security requirements with user convenience. Users experience streamlined authentication flows that maintain security while reducing daily authentication burden.
Enterprise integration capabilities support complex organizational requirements including Active Directory integration, SAML single sign-on, and API connectivity with existing identity management infrastructure. These integration features enable comprehensive security management while maintaining operational efficiency and user experience.
Advanced threat detection and conditional access controls provide intelligent authentication policies that adjust security requirements based on risk assessment, user behavior analysis, and contextual factors. High-risk login attempts trigger enhanced authentication requirements while normal activities proceed with standard verification.
4 WordPress User Roles and Access Control
4.1 WordPress User Role Security Configuration
Default WordPress user roles provide foundational access control through predefined permission sets that include Administrator, Editor, Author, Contributor, and Subscriber roles with specific capabilities and restrictions. Understanding these default roles and their associated permissions enables effective access control planning and security policy implementation.
Custom user role creation enables precise access control through tailored permission sets that align with organizational requirements and operational workflows. Custom roles should follow principle of least privilege guidelines, granting only necessary permissions while restricting access to sensitive functions and data.
Role-based access control implementation requires careful analysis of user responsibilities, data access requirements, and operational workflows to ensure appropriate permission assignment without creating security vulnerabilities or operational inefficiencies. Effective RBAC systems balance security requirements with user productivity needs.
User capability auditing and permission optimization involve regular review of user roles, permission assignments, and access patterns to identify potential security risks, unnecessary privileges, and optimization opportunities. Regular auditing ensures that access controls remain appropriate as organizational needs evolve.
Security Ninja’s advanced user management system provides comprehensive role management with granular permission control, automated auditing capabilities, and intelligent access optimization that ensures appropriate access levels while maintaining security and operational efficiency.
4.2 Advanced Access Control Strategies
Principle of least privilege implementation ensures that users receive only the minimum permissions necessary to perform their assigned responsibilities, reducing attack surface and limiting potential damage from compromised accounts. This approach requires careful analysis of user requirements and regular review of permission assignments.
Temporary access management enables time-limited permissions for contractors, temporary employees, and project-specific access requirements. Automated expiration systems ensure that temporary access permissions are revoked promptly when no longer needed, preventing unauthorized access through forgotten accounts.
Device-based authentication and trusted device management enable enhanced security through device registration and recognition systems that identify authorized devices and flag unusual access patterns. Trusted device management reduces authentication friction for regular users while maintaining security for new or unrecognized devices.
Security Ninja’s advanced access control features provide comprehensive access management with intelligent policy enforcement, automated compliance monitoring, and flexible configuration options that support complex organizational requirements while maintaining security effectiveness.
4.3 Security Ninja User Management Features
Advanced user role management provides granular permission control with custom role creation, capability assignment, and inheritance management that enables precise access control tailored to organizational requirements. Our system supports complex permission hierarchies and conditional access policies.
Automated user access auditing continuously monitors user activities, permission usage, and access patterns to identify potential security risks, policy violations, and optimization opportunities. Comprehensive audit trails support compliance requirements and security investigations while providing insights for access control optimization.
Intelligent access control with behavioral analysis examines user activities, access patterns, and operational workflows to identify anomalous behavior that may indicate account compromise or policy violations. This behavioral analysis provides proactive security monitoring that detects threats before they cause damage.
Professional user management consultation provides expert guidance for developing comprehensive access control policies, implementing security controls, and optimizing user management processes. Our security professionals help organizations balance security requirements with operational efficiency to achieve optimal outcomes.
5 Login Monitoring and Threat Detection
5.1 WordPress Login Activity Monitoring
Login attempt logging and analysis systems provide comprehensive visibility into authentication activities through detailed records of successful and failed login attempts, including timestamps, IP addresses, user agents, and geographic locations. This information enables security monitoring, threat detection, and forensic analysis of security incidents.
Failed login tracking and pattern recognition identify potential brute force attacks, credential stuffing attempts, and other malicious activities through analysis of failed authentication patterns. Advanced pattern recognition algorithms distinguish between legitimate user errors and systematic attack attempts to enable appropriate security responses.
User session monitoring and anomaly detection examine active user sessions for suspicious activities including unusual access patterns, privilege escalation attempts, and simultaneous sessions from different locations. Session monitoring provides real-time threat detection that enables immediate response to account compromise attempts.
Geographic and device-based login analysis identifies unusual access patterns that may indicate account compromise or unauthorized access attempts. This analysis considers user travel patterns, typical device usage, and access timing to distinguish between legitimate and suspicious activities.
5.2 Automated Threat Response and Mitigation
Real-time threat detection and automatic blocking systems identify and respond to malicious activities within milliseconds of detection, preventing successful attacks through immediate protective measures. Automated response systems operate continuously without human intervention while maintaining detailed logs for security analysis.
Intelligent rate limiting and progressive delays implement adaptive security measures that increase authentication difficulty for suspicious activities while maintaining normal access for legitimate users. Progressive delay systems exponentially increase wait times for repeated failed attempts while allowing immediate access for successful authentication.
Incident response automation coordinates multiple security systems to implement comprehensive protective measures when threats are detected. Automated incident response includes user notification, administrative alerting, evidence collection, and containment measures that minimize attack impact while preserving forensic evidence.
Security Ninja’s automated threat response system provides industry-leading protection through AI-powered threat detection, intelligent response coordination, and comprehensive incident management that ensures optimal security effectiveness with minimal administrative overhead.
5.3 Security Ninja Advanced Monitoring Capabilities
AI-powered threat detection utilizes machine learning algorithms that analyze authentication patterns, user behavior, and threat indicators to identify sophisticated attacks that traditional security systems cannot detect. Our AI system continuously evolves to recognize emerging attack methods and adapt protection strategies accordingly.
Comprehensive login analytics and security dashboards provide executive-level visibility into authentication security posture through intuitive interfaces that present key metrics, trend analysis, and threat intelligence. Dashboard systems enable informed security decision-making and demonstrate security program effectiveness.
Real-time alerting and incident response automation ensure immediate notification of security events through multiple communication channels including email, SMS, and integration with security information and event management (SIEM) systems. Intelligent alerting systems prioritize critical events while reducing alert fatigue.
Advanced forensic analysis and threat intelligence integration provide detailed investigation capabilities for security incidents including timeline reconstruction, attack vector analysis, and attribution assessment. Forensic capabilities support incident response, legal requirements, and security improvement initiatives.
6 WordPress Login Hardening Techniques
6.1 Login URL Customization and Obfuscation
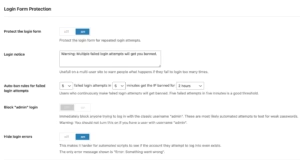
Default wp-admin URL security risks stem from the predictable nature of WordPress login interfaces that enable automated discovery and targeted attacks. The standard /wp-admin/ and /wp-login.php URLs provide attackers with known entry points that facilitate reconnaissance and attack automation against WordPress installations.
Custom login URL implementation involves modifying WordPress configuration to use non-standard login paths that obscure the authentication interface from automated discovery tools. Custom URLs should employ unpredictable naming conventions while maintaining functionality and user accessibility for legitimate administrators.
Login page access restrictions and IP whitelisting provide additional security layers by limiting authentication interface access to specific IP addresses or network ranges. These restrictions prove particularly valuable for administrative accounts and websites with defined user populations that access the system from known locations.
Administrative area protection requires comprehensive security measures including server-level access controls, additional authentication layers, and monitoring systems that protect sensitive administrative functions. Multi-layered protection ensures that even successful authentication cannot immediately compromise critical system functions.
6.2 Advanced Login Security Measures
CAPTCHA integration and bot prevention systems distinguish between human users and automated attack tools through challenge-response mechanisms that require human interaction for authentication completion. Modern CAPTCHA systems balance security effectiveness with user experience through intelligent challenge selection and accessibility considerations.
Login attempt rate limiting and progressive delays implement time-based restrictions that slow down brute force attacks while allowing normal user authentication to proceed without interference. Intelligent rate limiting considers user behavior patterns and authentication history to optimize security effectiveness.
Secure login over HTTPS and SSL certificate requirements ensure that authentication credentials are transmitted securely between users and servers, preventing interception and man-in-the-middle attacks. SSL implementation should include proper certificate validation and secure cipher suite configuration.
Login page customization and branding security considerations involve balancing visual customization with security requirements, ensuring that custom login interfaces maintain security functionality while providing appropriate branding and user experience enhancements.
Security Ninja’s advanced login security measures provide comprehensive protection through intelligent CAPTCHA integration, adaptive rate limiting, secure communication protocols, and customizable security interfaces that maintain both security effectiveness and user experience.
6.3 Security Ninja Login Hardening Features
Comprehensive login URL customization provides flexible configuration options for creating secure, non-standard login interfaces that resist automated discovery while maintaining functionality and user accessibility. Our system supports multiple customization approaches with intelligent conflict resolution and compatibility management.
Advanced CAPTCHA and bot detection systems utilize sophisticated algorithms that distinguish between human users and automated tools through behavioral analysis, device fingerprinting, and challenge-response mechanisms. Our bot detection provides superior accuracy while minimizing user friction.
Intelligent rate limiting with behavioral analysis implements adaptive security measures that adjust protection levels based on user behavior, threat assessment, and contextual factors. This intelligent approach provides optimal security effectiveness while maintaining seamless user experience for legitimate users.
Professional login page security and branding options enable custom login interface design with maintained security functionality, ensuring that visual customization does not compromise authentication security or create vulnerabilities that attackers could exploit.
Expert login hardening consultation provides professional guidance for implementing comprehensive login security measures, optimizing configuration settings, and maintaining security effectiveness while meeting operational requirements and user experience expectations.
7 Enterprise WordPress Login Security
7.1 Multi-Site Login Security Management
WordPress multisite authentication requires centralized security management that maintains consistent security policies across multiple websites while providing flexibility for site-specific requirements. Multisite security involves network-level authentication controls, user synchronization, and policy enforcement that ensures comprehensive protection.
Network-wide security policies and enforcement mechanisms enable consistent security standards across all sites within a WordPress network while providing administrative efficiency and simplified security management. Policy enforcement should balance network security requirements with site-specific operational needs.
User synchronization and cross-site authentication systems provide seamless user experience across multiple sites while maintaining security integrity and preventing unauthorized access. Synchronization systems should include user role management, permission inheritance, and security policy consistency.
Scalable security management for large WordPress networks requires automated policy deployment, centralized monitoring, and efficient administrative interfaces that enable effective security management without overwhelming administrative resources. Scalability considerations include performance optimization and resource management.
Security Ninja’s multisite security features provide comprehensive network-level security management with centralized policy enforcement, automated user synchronization, and scalable administrative interfaces that ensure consistent security across large WordPress deployments.
7.2 Integration with Enterprise Security Systems
Active Directory and LDAP authentication integration enables seamless connection with existing enterprise identity management infrastructure while maintaining WordPress-specific security enhancements. Directory integration should preserve existing user management workflows while adding WordPress security capabilities.
Enterprise identity management and provisioning systems enable automated user lifecycle management including account creation, permission assignment, and deactivation processes that align with organizational policies and compliance requirements. Provisioning systems should include approval workflows and audit trails.
Compliance requirements and audit trail management support regulatory obligations through comprehensive logging, reporting, and documentation capabilities that demonstrate security control effectiveness and policy adherence. Compliance features should include data retention, access controls, and reporting automation.
Security Ninja’s enterprise integration capabilities provide comprehensive connectivity with existing security infrastructure while maintaining WordPress-specific security enhancements and operational efficiency.
7.3 Security Ninja Enterprise Solutions
Enterprise-grade authentication and access control systems provide advanced security features including conditional access policies, risk-based authentication, and comprehensive user lifecycle management that meet the most demanding organizational security requirements.
Centralized security management and policy enforcement enable consistent security standards across complex organizational environments with automated policy deployment, compliance monitoring, and exception management that ensures security effectiveness while maintaining operational efficiency.
Advanced integration capabilities and API access support custom security implementations, third-party tool connectivity, and automated security management workflows that align with existing organizational infrastructure and operational processes.
Professional support and implementation services provide expert assistance for complex enterprise deployments including requirements analysis, system design, implementation planning, and ongoing optimization that ensures optimal security effectiveness and operational efficiency.
8 Conclusion & Implementation Roadmap
WordPress login security implementation requires systematic approach that addresses authentication fundamentals, password security, multi-factor authentication, access control, monitoring, and hardening techniques through coordinated security measures that provide comprehensive protection while maintaining operational efficiency and user experience.
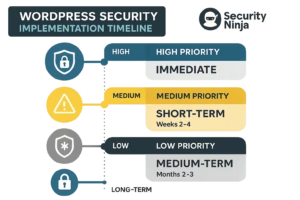
Implementation Priority Matrix guides security deployment through risk-based prioritization that addresses the most critical vulnerabilities first while building comprehensive security capabilities over time. High-priority implementations include strong password policies, two-factor authentication, and basic monitoring, followed by advanced hardening and enterprise integration features.
Phase 1: Foundation Security (Week 1-2) establishes basic login security through strong password policies, failed login monitoring, and basic rate limiting that provides immediate protection against common attacks while preparing for advanced security implementations.
Phase 2: Enhanced Authentication (Week 3-4) implements two-factor authentication, user role optimization, and login URL customization that significantly improves security posture while maintaining user experience and operational efficiency.
Phase 3: Advanced Protection (Week 5-6) deploys comprehensive monitoring, automated threat response, and advanced hardening techniques that provide enterprise-grade security capabilities with professional-level threat detection and response.
Phase 4: Enterprise Integration (Week 7-8) connects WordPress security with existing enterprise infrastructure through directory integration, SSO implementation, and centralized security management that ensures consistent security across organizational systems.
Take Action Today: Implement Security Ninja login security protection to safeguard your WordPress authentication system against the evolving threat landscape of 2025. Visit our WordPress security guide for comprehensive security implementation guidance, or explore our best WordPress security plugins comparison for detailed security solution analysis.
Don’t wait for an authentication compromise to highlight the importance of comprehensive login security. Deploy Security Ninja today and join thousands of WordPress users who trust our advanced authentication protection to secure their login systems, prevent unauthorized access, and maintain optimal security posture in an increasingly dangerous digital environment.
The investment in professional WordPress login security protection pays for itself through the first prevented breach, making Security Ninja not just the most effective choice, but also the most economical long-term authentication security solution available. Comprehensive protection, superior performance, and expert support combine to deliver unmatched value in WordPress login security.
9 Frequently Asked Questions
Q: What is the most important WordPress login security measure I should implement first? A: Strong password policies combined with two-factor authentication provide the most significant security improvement for WordPress login protection. Security Ninja’s comprehensive authentication system includes both features with intelligent implementation that maximizes security while maintaining user experience.
Q: How effective is two-factor authentication for WordPress login security? A: Two-factor authentication reduces account compromise risk by over 99% according to security research. Security Ninja’s MFA implementation supports multiple authentication methods with intelligent fallback options and enterprise integration capabilities for maximum security effectiveness.
Q: Can WordPress login security measures slow down my website performance? A: Properly implemented login security should not impact website performance for regular visitors. Security Ninja’s optimized authentication system actually improves performance through intelligent caching and resource optimization while providing comprehensive security protection.
Q: How do I know if my WordPress login is under attack? A: Signs of login attacks include multiple failed login attempts, unusual geographic access patterns, and slow login performance. Security Ninja’s monitoring system provides real-time attack detection with automated alerts and detailed analytics for comprehensive threat visibility.
Q: What should I do if I suspect my WordPress login has been compromised? A: Immediately change all passwords, review user accounts for unauthorized access, check for malicious modifications, and implement enhanced security measures. Security Ninja’s incident response features provide automated containment and professional support for security incidents.
Q: How often should I review WordPress user roles and permissions? A: User access should be reviewed quarterly or when organizational roles change. Security Ninja’s automated auditing system continuously monitors user permissions and provides alerts for potential security risks or policy violations.
Q: Is it safe to use SMS for WordPress two-factor authentication? A: SMS authentication provides better security than passwords alone but faces vulnerabilities including SIM swapping attacks. Security Ninja supports multiple authentication methods including more secure options like authenticator apps and hardware tokens for enhanced protection.
Q: How can I secure WordPress login for multiple websites? A: WordPress multisite networks require centralized security management with consistent policies across all sites. Security Ninja’s enterprise features provide network-level security management with automated policy enforcement and centralized monitoring capabilities.
Q: What are the best practices for WordPress administrative account security? A: Administrative accounts require enhanced security including unique usernames, strong passwords, two-factor authentication, IP restrictions, and regular security auditing. Security Ninja’s administrative protection features provide comprehensive security for high-privilege accounts.
Q: How do I balance WordPress login security with user experience? A: Effective security implementation uses intelligent authentication policies that adapt security requirements based on risk assessment and user behavior. Security Ninja’s adaptive security system provides optimal protection while maintaining seamless user experience for legitimate users.
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.