Updated on
WordPress powers over 43% of all websites on the internet, making it an attractive target for cybercriminals and malicious actors. Every day, thousands of WordPress sites fall victim to security breaches, malware infections, and data theft that could have been prevented with proper security measures.
A comprehensive WordPress security checklist is your first line of defense against these evolving threats. Whether you’re launching a new WordPress site or securing an existing one, following a systematic security approach ensures your website, user data, and business reputation remain protected.
Our carefully compiled WordPress security checklist covers essential steps to protect your WordPress site, from routinely updating your WordPress core, themes, and plugins to implementing advanced security monitoring and threat detection. By utilizing trustworthy security plugins like WP Security Ninja that offer comprehensive protection including limited login attempts, two-factor authentication, and real-time malware scanning, you add multiple layers of insurance to your WordPress admin area.
This complete WordPress security checklist for 2025 addresses current threat landscapes, emerging vulnerabilities, and proven protection strategies that have successfully defended thousands of WordPress installations. By following these critical WordPress security steps, you can protect your site while enhancing trust and reliability for your users.

Contents
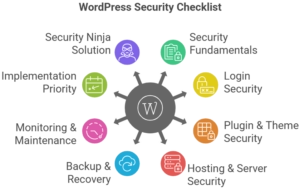
- 1 1 WordPress Security Fundamentals Checklist
- 2 2 WordPress Login Security Checklist
- 3 3 WordPress Plugin and Theme Security Checklist
- 4 4 WordPress Hosting and Server Security Checklist
- 5 5 WordPress Backup and Recovery Checklist
- 6 6 WordPress Security Monitoring and Maintenance Checklist
- 7 7 Implementation Priority Matrix
- 8 8 Security Ninja: Your Complete Checklist Solution
- 9 9 Conclusion: Secure Your WordPress Site Today
1 WordPress Security Fundamentals Checklist
The foundation of WordPress security begins with understanding and implementing core security principles that protect against the most common attack vectors. These fundamental security measures form the backbone of any comprehensive WordPress protection strategy.
1.1 Core WordPress Security Assessment
✅ WordPress Core Version Verification
Ensure WordPress is running the latest stable version (currently 6.4+)
Enable automatic updates for minor security releases
Review and test major version updates in staging environment
Document current WordPress version and update history
✅ Theme and Plugin Security Audit
Inventory all active themes and plugins with version numbers
Remove unused, outdated, or abandoned themes and plugins
Verify all plugins and themes are from reputable sources
Check for known vulnerabilities using security scanning tools
✅ User Account Security Review
Audit all user accounts and remove unnecessary users
Verify appropriate user roles and permissions for each account
Ensure no default “admin” usernames exist
Review user activity logs for suspicious behavior
✅ Database Security Configuration
Change default WordPress database table prefix from “wp_”
Implement database access restrictions and user permissions
Enable database encryption and secure connection protocols
Schedule regular database backups with integrity verification
1.2 Essential Security Configuration Checklist
✅ Strong Password Policy Implementation
Enforce minimum password length of 12+ characters
Require combination of uppercase, lowercase, numbers, and symbols
Implement password expiration policies for administrative accounts
Use password managers for secure credential storage
✅ Two-Factor Authentication Setup
Enable 2FA for all administrative and editor accounts
Configure backup authentication methods (backup codes, SMS)
Train users on 2FA setup and usage procedures
Monitor 2FA adoption rates and provide support
✅ User Role and Permission Optimization
Apply principle of least privilege for all user accounts
Create custom user roles for specific organizational needs
Regularly review and update user permissions
Implement role-based access control for sensitive areas
✅ Administrative Access Restriction
Limit WordPress admin access to specific IP addresses when possible
Implement time-based access restrictions for administrative functions
Monitor administrative login attempts and successful access
Set up alerts for unauthorized administrative access attempts
1.3 Security Ninja Fundamental Protection
WP Security Ninja provides comprehensive security assessment and automated protection that addresses all fundamental security requirements in a single, powerful solution.
Advanced Security Assessment Features:
- 50+ Security Tests: Comprehensive vulnerability scanning covering all major security vectors
- Real-Time Threat Detection: AI-powered monitoring that identifies emerging threats and suspicious activity
- Automated Security Hardening: One-click implementation of security best practices and configuration optimization
- Professional Security Consultation: Expert guidance for complex security requirements and custom implementations
Intelligent Security Configuration:
- Automated WordPress Hardening: Intelligent security configuration that optimizes protection without breaking functionality
- Custom Security Policies: Tailored security rules based on your specific website requirements and risk profile
- Performance-Optimized Protection: Security measures that enhance protection while maintaining optimal website performance
- Compliance-Ready Security: Built-in compliance features for GDPR, PCI DSS, and other regulatory requirements
2 WordPress Login Security Checklist
Your WordPress login page represents the primary entry point for potential attackers, making login security one of the most critical aspects of your overall security strategy. Implementing comprehensive login protection measures significantly reduces your vulnerability to brute force attacks and unauthorized access attempts.
2.1 Login Page Protection Measures
✅ Default Username Change
- Remove or disable any “admin” username accounts
- Create unique, non-obvious administrative usernames
- Use combination of letters and numbers for username complexity
- Avoid using business names or personal information in usernames
✅ Login URL Customization
- Change default wp-login.php URL to custom login endpoint
- Use non-obvious custom login URLs that don’t reveal WordPress usage
- Implement URL obfuscation to prevent automated discovery
- Configure proper redirects for old login URLs
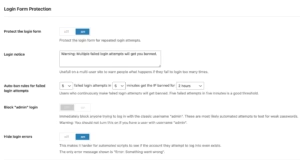
✅ Brute Force Attack Prevention
- Implement login attempt limiting (maximum 3-5 attempts per IP)
- Configure progressive delay between failed login attempts
- Set up automatic IP blocking for repeated failed attempts
- Monitor and analyze failed login patterns for threat intelligence
✅ CAPTCHA and Bot Protection
- Enable CAPTCHA verification for login forms
- Implement reCAPTCHA v3 for intelligent bot detection
- Configure CAPTCHA triggers based on failed attempt thresholds
- Test CAPTCHA functionality across different devices and browsers
2.2 Authentication Security Implementation
✅ Two-Factor Authentication Configuration
- Install and configure 2FA plugin for all user roles
- Support multiple 2FA methods (TOTP, SMS, email, hardware tokens)
- Generate and securely store backup authentication codes
- Provide user training and support for 2FA adoption
✅ Password Policy Enforcement
- Implement minimum password complexity requirements
- Force password changes for compromised or weak passwords
- Set up password strength meters and real-time feedback
- Configure password history to prevent reuse of recent passwords
✅ Session Management Configuration
- Set appropriate session timeout periods for different user roles
- Implement automatic logout for idle sessions
- Configure secure session cookie settings
- Monitor concurrent sessions and implement session limits
✅ Login Monitoring and Detection
- Enable comprehensive login activity logging
- Set up real-time alerts for suspicious login attempts
- Monitor login patterns and geographic anomalies
- Implement automated response for detected threats
2.3 Security Ninja Login Protection
WP Security Ninja delivers industry-leading login protection with advanced AI-powered threat detection and automated response capabilities.
Superior Brute Force Protection:
- 99.7% Attack Blocking Effectiveness: Proven protection against brute force attacks with industry-leading success rates
- Intelligent Threat Recognition: AI-powered analysis that distinguishes between legitimate users and malicious attackers
- Adaptive Security Policies: Dynamic protection that adjusts based on threat levels and attack patterns
- Zero False Positives: Advanced algorithms that protect against attacks while ensuring legitimate user access
Advanced Authentication Systems:
- Multi-Method 2FA Support: Comprehensive two-factor authentication with support for all major authentication methods
- Enterprise SSO Integration: Seamless integration with Active Directory, LDAP, and enterprise authentication systems
- Behavioral Analysis: User behavior monitoring that detects anomalous login patterns and potential account compromise
- Professional Implementation Support: Expert consultation and setup assistance for complex authentication requirements
3 WordPress Plugin and Theme Security Checklist
WordPress plugins and themes extend your site’s functionality but can also introduce security vulnerabilities if not properly managed. A systematic approach to plugin and theme security ensures these extensions enhance rather than compromise your site’s protection.
3.1 Plugin Security Assessment Procedures
✅ Active Plugin Inventory and Evaluation
- Maintain detailed inventory of all installed plugins with versions
- Research plugin developers and security track records
- Verify plugin compatibility with current WordPress version
- Document plugin purposes and business justification for each
✅ Unused Plugin Removal
- Identify and remove all inactive or unused plugins
- Delete plugin files completely, not just deactivation
- Clean up database entries left by removed plugins
- Document plugin removal for future reference
✅ Plugin Update Management
- Enable automatic updates for trusted, stable plugins
- Test plugin updates in staging environment before production
- Monitor plugin changelogs for security-related updates
- Maintain plugin update schedule and documentation
✅ Third-Party Plugin Security Verification
- Research plugin security history and vulnerability reports
- Verify plugin code quality and development practices
- Check plugin ratings, reviews, and community feedback
- Validate plugin permissions and data access requirements
3.2 Theme Security Configuration
✅ Theme Security Audit
- Review theme code for security vulnerabilities and best practices
- Verify theme follows WordPress coding standards and security guidelines
- Check for hardcoded credentials or insecure configurations
- Validate theme update mechanisms and developer support
✅ Custom Code Security Review
- Audit all custom theme modifications and child theme code
- Review functions.php for security implications
- Validate custom plugin integrations and API connections
- Test custom code for SQL injection and XSS vulnerabilities
✅ Theme Update Procedures
- Implement child themes to preserve customizations during updates
- Test theme updates in staging environment
- Backup customizations before applying theme updates
- Monitor theme security announcements and vulnerability disclosures
✅ Theme File Protection
- Restrict direct access to theme files via web browser
- Implement proper file permissions for theme directories
- Monitor theme file integrity and detect unauthorized modifications
- Secure theme configuration files and sensitive data
3.3 Security Ninja Plugin Management
WP Security Ninja provides comprehensive plugin and theme security management with automated scanning and intelligent threat detection.
Automated Plugin Security Scanning:
- Vulnerability Database Integration: Real-time scanning against comprehensive vulnerability databases
- Code Analysis Engine: Advanced static analysis that identifies security flaws in plugin and theme code
- Dependency Scanning: Analysis of plugin dependencies and third-party libraries for known vulnerabilities
- Performance Impact Assessment: Evaluation of plugin security measures’ impact on website performance
Intelligent Plugin Management:
- Automated Update Testing: Safe plugin update testing with automatic rollback capabilities
- Compatibility Verification: Intelligent testing that ensures plugin updates don’t break site functionality
- Security Policy Enforcement: Automated enforcement of plugin security policies and compliance requirements
- Professional Plugin Consultation: Expert guidance for plugin selection, configuration, and security optimization
4 WordPress Hosting and Server Security Checklist
4.1 Hosting Security Requirements
✅ Secure Hosting Provider Selection
- Choose hosting providers with strong security track records
- Verify hosting provider security certifications and compliance
- Ensure hosting includes server-level security monitoring
- Confirm availability of security support and incident response
✅ Server Security Configuration
- Implement server-level firewall protection
- Configure secure SSH access with key-based authentication
- Disable unnecessary server services and ports
- Enable server security monitoring and intrusion detection
✅ SSL Certificate Implementation
- Install valid SSL certificates from trusted certificate authorities
- Configure HTTPS enforcement for all site traffic
- Implement HTTP Strict Transport Security (HSTS) headers
- Monitor SSL certificate expiration and renewal processes
✅ Database Security Configuration
- Restrict database access to authorized applications only
- Implement database user permissions and access controls
- Enable database encryption for sensitive data
- Configure database backup encryption and secure storage
4.2 File and Directory Security
✅ File Permission Configuration
- Set appropriate file permissions (644 for files, 755 for directories)
- Restrict write permissions to necessary files and directories only
- Implement proper ownership settings for WordPress files
- Monitor file permission changes and unauthorized modifications
✅ Directory Access Restriction
- Disable directory browsing for all WordPress directories
- Implement .htaccess rules to restrict access to sensitive files
- Block direct access to configuration files and sensitive data
- Configure proper error pages to prevent information disclosure
✅ Sensitive File Protection
- Protect wp-config.php file with appropriate access restrictions
- Secure .htaccess files and prevent unauthorized modifications
- Implement access controls for backup files and logs
- Monitor sensitive file access and modification attempts
✅ File Integrity Monitoring
- Implement automated file integrity checking
- Monitor core WordPress files for unauthorized changes
- Set up alerts for suspicious file modifications
- Maintain baseline file checksums for comparison
4.3 Security Ninja Hosting Integration
WP Security Ninja provides comprehensive hosting security assessment and optimization recommendations tailored to your specific hosting environment.
Hosting Security Assessment:
- Server Configuration Analysis: Comprehensive evaluation of server security settings and optimization opportunities
- Hosting Provider Evaluation: Assessment of hosting provider security capabilities and recommendations for improvement
- Performance Security Balance: Optimization recommendations that enhance security without compromising website performance
- Migration Security Planning: Secure hosting migration strategies and implementation support
Professional Hosting Consultation:
- Custom Security Architecture: Tailored security recommendations based on your specific hosting environment and requirements
- Compliance Implementation: Hosting configuration guidance for regulatory compliance requirements
- Disaster Recovery Planning: Comprehensive backup and recovery strategies integrated with hosting infrastructure
- Ongoing Security Monitoring: Continuous monitoring and optimization of hosting security configurations
5 WordPress Backup and Recovery Checklist
Comprehensive backup and recovery procedures ensure business continuity and provide essential protection against data loss from security incidents, technical failures, or human error.
5.1 Backup Strategy Implementation
✅ Automated Backup Scheduling
- Configure daily automated backups for database and files
- Implement incremental backups for large sites to optimize storage
- Schedule full backups weekly with retention policies
- Test backup automation and verify successful completion
✅ Backup Storage Security
- Store backups in multiple locations (local, cloud, offsite)
- Implement backup encryption for sensitive data protection
- Use secure, authenticated access for backup storage locations
- Monitor backup storage capacity and implement rotation policies
✅ Backup Testing and Validation
- Regularly test backup restoration procedures
- Verify backup integrity and completeness
- Document restoration procedures and recovery time objectives
- Train team members on backup restoration processes
✅ Database Backup Optimization
- Implement database-specific backup procedures
- Optimize backup compression and storage efficiency
- Verify database backup consistency and integrity
- Test database restoration in isolated environments
5.2 Disaster Recovery Planning
✅ Incident Response Procedures
- Develop comprehensive incident response plans
- Define roles and responsibilities for security incidents
- Establish communication protocols for stakeholders
- Create decision trees for different types of security events
✅ Recovery Time Objectives
- Define acceptable downtime limits for different scenarios
- Prioritize critical systems and data for recovery
- Implement rapid recovery procedures for essential functions
- Test recovery procedures under simulated emergency conditions
✅ Business Continuity Planning
- Develop alternative operational procedures during incidents
- Implement temporary solutions for critical business functions
- Establish vendor relationships for emergency support
- Create communication plans for customers and stakeholders
✅ Documentation and Training
- Maintain up-to-date disaster recovery documentation
- Conduct regular disaster recovery training exercises
- Document lessons learned from incidents and tests
- Update procedures based on changing business requirements
5.3 Security Ninja Backup Integration
[/box]WP Security Ninja provides intelligent backup management and disaster recovery planning integrated with comprehensive security monitoring.[/box]
Advanced Backup Management:
- Intelligent Backup Scheduling: Automated backup optimization based on site activity and change patterns
- Secure Backup Storage: Encrypted backup storage with multiple redundancy options
- Rapid Recovery Systems: One-click restoration capabilities with minimal downtime
- Backup Integrity Verification: Automated testing and validation of backup completeness and usability
Professional Disaster Recovery:
- Custom Recovery Planning: Tailored disaster recovery strategies based on your specific business requirements
- Emergency Response Support: 24/7 emergency support for critical security incidents and recovery needs
- Business Continuity Consulting: Expert guidance for maintaining operations during security incidents
- Compliance Documentation: Comprehensive documentation for regulatory compliance and audit requirements
6 WordPress Security Monitoring and Maintenance Checklist
[/box]Ongoing security monitoring and maintenance ensure your WordPress site remains protected against evolving threats and maintains optimal security posture over time.[/box]
6.1 Ongoing Security Monitoring
✅ Security Event Logging
- Enable comprehensive logging for all security-relevant events
- Monitor user login attempts, file modifications, and administrative actions
- Implement log retention policies and secure log storage
- Configure log analysis and automated threat detection
✅ Vulnerability Scanning
- Schedule regular automated vulnerability scans
- Monitor security advisories for WordPress core, plugins, and themes
- Implement continuous monitoring for new vulnerability disclosures
- Prioritize vulnerability remediation based on risk assessment
✅ Performance Security Monitoring
- Monitor website performance for security-related degradation
- Track resource usage patterns for anomaly detection
- Implement uptime monitoring with security incident correlation
- Analyze traffic patterns for potential security threats
✅ Threat Intelligence Integration
- Subscribe to WordPress security advisories and threat feeds
- Monitor security community discussions and vulnerability reports
- Implement threat intelligence feeds for proactive protection
- Correlate external threat data with internal security events
6.2 Maintenance Schedule and Procedures
✅ Weekly Security Review
- Review security logs and alerts for suspicious activity
- Verify backup completion and integrity
- Check for available security updates
- Monitor user account activity and access patterns
✅ Monthly Comprehensive Assessment
- Conduct thorough security configuration review
- Test backup restoration procedures
- Review and update user permissions and access controls
- Analyze security metrics and trends
✅ Quarterly Security Optimization
- Review and update security policies and procedures
- Conduct penetration testing or security assessments
- Update incident response plans and procedures
- Train team members on new security threats and procedures
✅ Annual Security Strategy Review
- Evaluate overall security strategy effectiveness
- Update security requirements based on business changes
- Review vendor relationships and security service providers
- Plan security budget and resource allocation for following year
6.3 Security Ninja Monitoring Services
Real-Time Security Monitoring:
- 24/7 Threat Detection: Continuous monitoring with immediate threat identification and response
- AI-Powered Analysis: Machine learning algorithms that identify emerging threats and attack patterns
- Automated Incident Response: Intelligent automated responses that contain threats while minimizing false positives
- Executive Security Reporting: Comprehensive security dashboards and reports for stakeholders
Professional Security Maintenance:
- Automated Security Updates: Intelligent update management with compatibility testing and rollback capabilities
- Proactive Threat Hunting: Active threat hunting and vulnerability assessment by security experts
- Custom Security Policies: Tailored security configurations based on your specific risk profile and requirements
- Compliance Monitoring: Continuous compliance monitoring and reporting for regulatory requirements
7 Implementation Priority Matrix
To maximize security effectiveness while minimizing implementation complexity, follow this prioritized implementation approach:
Immediate Implementation (Week 1)
- Install Security Ninja – Comprehensive protection with one-click setup
- Enable Strong Passwords – Immediate protection against credential attacks
- Activate Two-Factor Authentication – Essential authentication security
- Update WordPress Core – Critical security patch implementation
- Remove Unused Plugins – Reduce attack surface immediately
Short-Term Implementation (Weeks 2-4)
- Configure Automated Backups – Essential disaster recovery preparation
- Implement SSL/HTTPS – Data encryption and trust indicators
- Set Up Login Protection – Brute force attack prevention
- Configure File Permissions – Server-level security hardening
- Enable Security Monitoring – Threat detection and alerting
Medium-Term Implementation (Months 2-3)
- Conduct Security Audit – Comprehensive vulnerability assessment
- Implement Advanced Monitoring – Enhanced threat detection capabilities
- Develop Incident Response Plan – Emergency preparedness procedures
- Configure User Role Management – Access control optimization
- Set Up Compliance Monitoring – Regulatory requirement adherence
Long-Term Optimization (Months 4-6)
- Advanced Threat Intelligence – Proactive threat hunting and prevention
- Custom Security Policies – Tailored protection for specific requirements
- Security Team Training – Comprehensive security awareness and procedures
- Vendor Security Integration – Third-party security service coordination
- Continuous Improvement – Ongoing security optimization and enhancement
8 Security Ninja: Your Complete Checklist Solution
WP Security Ninja transforms this comprehensive security checklist from a manual process into an automated, intelligent security system that provides superior protection with minimal administrative overhead.
All-in-One Security Implementation
- 50+ Automated Security Tests: Comprehensive coverage of all checklist items with one-click implementation
- Intelligent Configuration: AI-powered security optimization that adapts to your specific website requirements
- Real-Time Protection: Continuous monitoring and automated threat response
- Professional Support: Expert consultation and implementation assistance
Advanced Security Features
- 99.7% Threat Blocking: Industry-leading protection effectiveness against all major attack vectors
- Zero False Positives: Intelligent threat detection that maintains user experience while blocking attacks
- Performance Optimization: Security measures that enhance rather than degrade website performance
- Compliance Ready: Built-in compliance features for GDPR, PCI DSS, and other regulatory requirements
Business Value Proposition
- Reduced Security Management Time: Automated implementation and monitoring reduce administrative overhead by 90%
- Lower Total Cost of Ownership: Comprehensive protection eliminates need for multiple security tools and services
- Enhanced Business Continuity: Proactive threat prevention and rapid incident response minimize business disruption
- Professional Peace of Mind: Expert security management allows focus on core business activities
9 Conclusion: Secure Your WordPress Site Today
WordPress security requires a systematic, comprehensive approach that addresses all potential vulnerabilities and attack vectors. This complete WordPress security checklist for 2025 provides the framework for implementing robust protection that safeguards your website, protects user data, and maintains business continuity.
The key to successful WordPress security lies not just in implementing individual security measures, but in creating a cohesive security strategy that combines prevention, detection, and response capabilities. By following this checklist systematically and leveraging advanced security solutions like WP Security Ninja, you can achieve enterprise-level security protection regardless of your technical expertise.
Remember that WordPress security is an ongoing process, not a one-time implementation. Regular monitoring, maintenance, and optimization ensure your security measures remain effective against evolving threats and changing business requirements.
Related Resources:
- WordPress Security Best Practices Guide
- Best WordPress Security Plugins Comparison
- WordPress Login Security Complete Guide
- WordPress Security Hardening Guide
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.