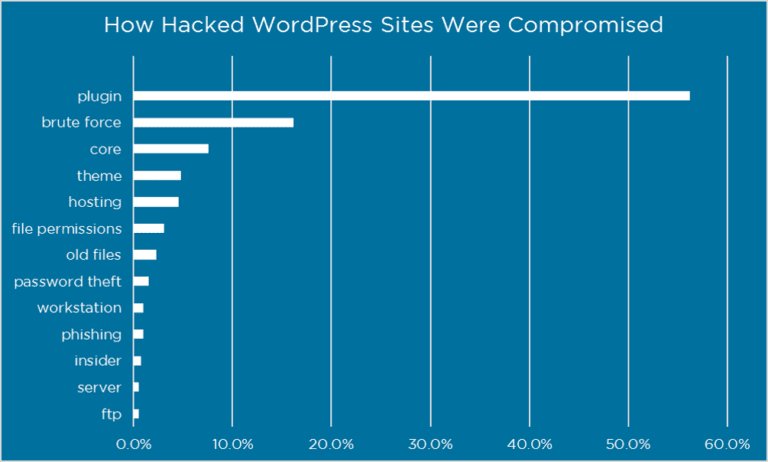
Once upon a time, brute force attacks were the primary way that hackers gained access to websites or to an individual’s personal and financial information stored online.
While those attacks still occur, phishing has come to be one of the most crucial threats we face today. As such, it is imperative that you protect your data and your WordPress website by ensuring your employees are able to spot phishing emails and not fall prey to these scams.

Contents
What Is Phishing?
Before we go too far, let’s define what phishing is. According to Phishing.org, it is “a cybercrime in which a target or targets are contacted by email, telephone, or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking, and credit card details and passwords.
The information is then used to access important accounts and can result in identity theft and financial loss.”
How to Spot Phishing Emails
While text messages and phone calls are sometimes used, email is the most common vehicle for a phishing attack. As such, it is important that your employees know how to spot these types of communications, in addition to having training in other areas of cybersecurity.
Inauthentic
When an email lands in the inbox, rather than going straight for the body text, it’s important to take a moment and look at the web and email addresses. These may be hidden, but hovering the mouse cursor over them should reveal the addresses.
If they look inauthentic, it’s a good sign that the message is an attempt to steal information. For instance, if the address looks like this: @mail@paypal.net rather than @paypal.com, it’s a sure sign that you need to delete the message unopened.
Body Text URLs

This will show you the actual URL you’ll be visiting. If it doesn’t match up with the text in the body of the email, do not click it. For instance, the link in the email might say chase.com/login but when you hover the mouse over it, it might read as something completely different – Chase might not even be part of it.
Misspellings and Incorrect Capitalization
While there will always be misspellings and incorrect capitalization in personal emails, businesses are held to a higher standard in their communications, and that’s actually a good thing.
If you notice obviously misspelled words or incorrect capitalization within the message, it is a very good sign that the message is part of a phishing attack.
The Email Address
We discussed the sending email address and the URL, but we need to discuss your email address for a moment. If you receive an email from a business at an email address that is not associated with that company, then you can be pretty confident that it’s a scam.
For instance, you receive an email from PayPal at your work address, but you’ve never used your work address in relation to your PayPal account, do not click any links within the message. It’s a phishing email.
The Presence of a URL

You would actually be hard-pressed to find any bigger business that still includes URLs within the body of the email with a request to click the link. Instead, they tell you to log into your account through a separate browser window.
So, any email that you receive that seems like it’s from a business, but contains a request to click an included URL, should be looked at with suspicion.
Attachments
If an employee receives an email they were not expecting that includes an attachment, that file should not be opened. The message should be deleted immediately, as it is almost certainly an attack and the file will actually deliver a payload of ransomware or other malicious software.
How to prevent Phishing Attacks
So, how do you avoid these attacks? What can you do to decrease the chances that your employees will accidentally click a link and put your business in danger?
Teach Suspicion
The first thing to do is ensure that your employees view pretty much all messages with suspicion.
The more alarming the message contents, the greater the suspicion should be. Phishing attacks often rely on fear to make otherwise knowledgeable people do things against their better judgment, so be prepared.
Use Common Sense
If the email seems too good to be true, or it says something that goes against common sense, like saying you’ve won a contest that you cannot remember entering, it’s most likely a scam and should be deleted.
Ask
There have been several instances where phishing attacks involved emails that seemingly originated from higher-ups within the company asking for passwords and usernames to company assets like databases and websites.
In these sorts of instances, the employee receiving the email should pick up the phone and call the sender, or, better yet, walk down to their office to ask in person if they truly sent such a request.
In 99% of cases, it’s a phishing attack. You should also institute a company-wide policy that states these types of requests are not to be made.
Spotting phishing emails can be challenging, but with the right cybersecurity training and a company-wide realization that these attacks can and do happen all the time, it becomes easier to safeguard your website and other company assets.
Dive even deeper into phishing attacks and how to prevent hackers getting access to your website via phishing attacks.
Written by Lars Koudal