Updated on
In 2025, a WordPress site is attacked every 39 seconds. With over 810 million websites powered by WordPress, representing 43% of all websites globally, the platform has become the primary target for cybercriminals seeking to exploit vulnerabilities and steal sensitive data.
The financial impact of these attacks is staggering. According to IBM’s latest Cost of a Data Breach Report, the average cost of a data breach reached $4.88 million in 2024, with small businesses facing an average cost of $3.31 million. For WordPress site owners, these statistics represent more than numbers, they represent potential business destruction, reputation damage, and legal liability that could have been prevented with proper WordPress security best practices.
The WordPress security landscape has evolved dramatically in recent years. Traditional security approaches that focused solely on basic password protection and simple firewalls are no longer sufficient against sophisticated attack vectors. Modern threats include AI-generated malware, supply chain attacks targeting plugins and themes, zero-day exploits, and advanced persistent threats designed to remain undetected for extended periods.
However, implementing comprehensive WordPress security measures doesn’t require a cybersecurity degree or massive financial investment. With the right approach, proven strategies, and professional tools like Security Ninja, you can protect your WordPress website with enterprise-level security while maintaining optimal performance and user experience.
This comprehensive guide presents 25+ proven WordPress security best practices that have been tested and refined through years of real-world implementation. Whether you’re managing a personal blog, business website, or enterprise-level WordPress installation, these security hardening techniques will provide the protection you need against current and emerging threats.
Our approach balances technical depth with practical implementation, ensuring that both beginners and experienced developers can successfully secure their WordPress sites. We’ll cover everything from fundamental security principles to advanced hardening techniques, compliance requirements, and professional security monitoring, all while demonstrating how Security Ninja’s comprehensive security features can streamline your security implementation.
The cost of implementing proper WordPress security best practices is minimal compared to the potential cost of a security breach. By following this guide, you’ll not only protect your website and data but also ensure compliance with modern privacy regulations, maintain user trust, and safeguard your business reputation in an increasingly dangerous digital landscape.
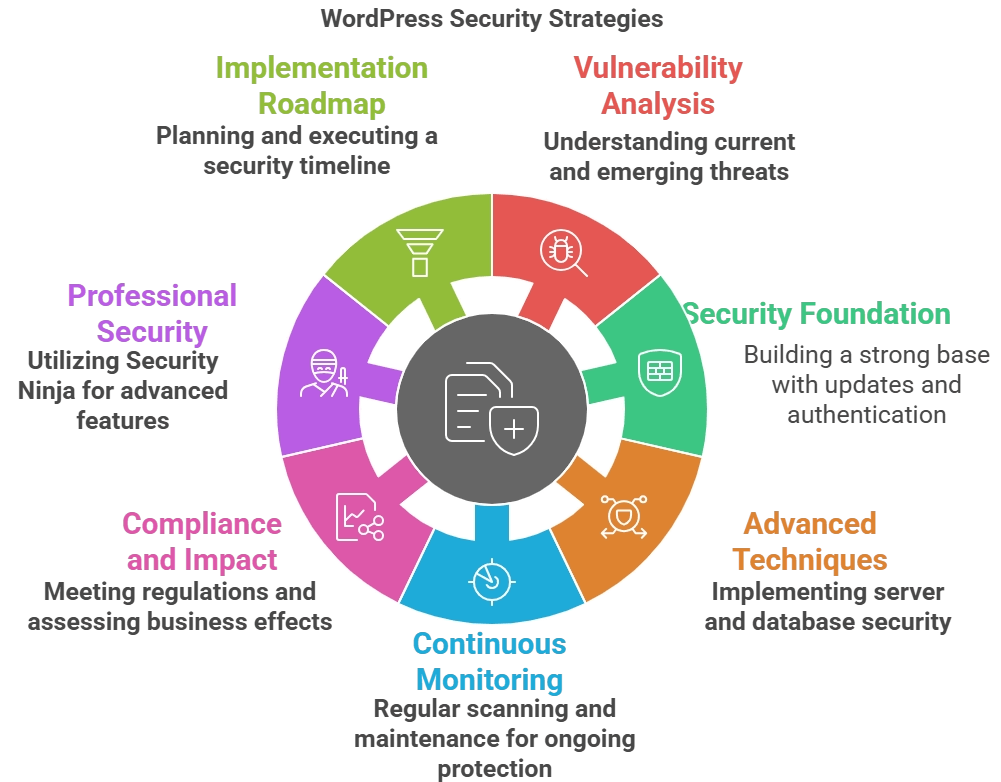
Contents
- 1 1 Understanding the 2025 WordPress Threat Landscape
- 2 2 Building Your WordPress Security Foundation
- 3 3 Advanced WordPress Security Hardening Techniques
- 4 4 Continuous Security Monitoring and Maintenance
- 5 5 WordPress Security Compliance and Business Impact
- 6 6 Implementing Professional Security with Security Ninja
- 7 7 Your WordPress Security Implementation Roadmap
- 8 8 Conclusion
- 9 Frequently Asked Questions
1 Understanding the 2025 WordPress Threat Landscape
The WordPress security environment in 2025 presents unprecedented challenges that require a fundamental shift in how we approach website protection. Understanding these evolving threats is essential for implementing effective WordPress security measures that address real-world attack vectors rather than outdated security assumptions.
1.1 Current WordPress Vulnerability Statistics
The numbers paint a sobering picture of the current threat landscape. In 2024, security researchers identified 7,966 new vulnerabilities in the WordPress ecosystem, representing a 34% increase over 2023. This dramatic rise reflects both the growing popularity of WordPress and the increasing sophistication of security research and threat detection.
More concerning is the speed at which these vulnerabilities are being exploited. The WordPress Security Team reports that 43% of newly discovered vulnerabilities are exploitable without authentication, meaning attackers can compromise websites without needing login credentials. This statistic underscores the critical importance of proactive WordPress security hardening rather than relying solely on access controls.
Theme vulnerabilities, while less common than plugin issues, have increased by 28% year-over-year. Many WordPress users underestimate theme security risks, focusing primarily on plugin management while neglecting theme updates and security assessments. This oversight creates opportunities for attackers to exploit theme-based vulnerabilities that may persist undetected for months.
1.2 WordPress Architecture Security Implications
WordPress’s architecture, while providing flexibility and ease of use, creates unique security considerations that must be addressed through comprehensive WordPress security best practices. The platform’s modular design, with core software, themes, and plugins working together, creates multiple potential entry points for attackers.
The WordPress core itself maintains an excellent security record, with the dedicated WordPress Security Team providing rapid response to discovered vulnerabilities. However, the core represents only one component of a complete WordPress installation. The real security challenges emerge from the complex interactions between core software, third-party plugins, custom themes, and server configurations.
Database security represents another critical architectural consideration. WordPress stores all content, user data, and configuration information in a MySQL database that becomes a high-value target for attackers. Default database configurations often lack proper security hardening, creating opportunities for SQL injection attacks, unauthorized data access, and complete database compromise.
File system security adds another layer of complexity. WordPress requires specific file permissions to function properly, but overly permissive settings can allow attackers to upload malicious files, modify existing code, or gain unauthorized access to sensitive configuration files. Balancing functionality with security requires careful attention to file permissions, directory structures, and access controls.
1.3 2025 Emerging Threats
The threat landscape continues to evolve rapidly, with new attack vectors emerging that specifically target WordPress installations. Understanding these emerging threats is crucial for implementing forward-thinking WordPress security measures that provide protection against both current and future attacks.
AI-generated malware represents one of the most significant emerging threats. Cybercriminals are increasingly using artificial intelligence to create sophisticated malware that can evade traditional detection methods, adapt to different environments, and remain persistent across security updates. These AI-powered attacks can analyze WordPress installations to identify specific vulnerabilities and customize their approach accordingly.
Supply chain attacks targeting the WordPress ecosystem have become increasingly sophisticated. Rather than attacking individual websites directly, cybercriminals are targeting plugin and theme developers, hosting providers, and other ecosystem participants to inject malicious code that gets distributed to thousands or millions of WordPress sites simultaneously. The 2024 compromise of several popular WordPress plugins demonstrated the devastating potential of supply chain attacks.
Zero-day exploits, while not new, are being discovered and weaponized more rapidly than ever before. The time between vulnerability discovery and active exploitation has decreased significantly, leaving website owners with smaller windows to implement protective measures. This trend emphasizes the importance of proactive security monitoring and rapid response capabilities.
Ransomware attacks specifically targeting WordPress sites have evolved beyond simple file encryption. Modern WordPress ransomware often includes data exfiltration, threatening to release sensitive customer information unless ransom demands are met. These attacks combine technical compromise with reputational damage and legal liability, creating multiple pressure points for victims.
Advanced persistent threats (APTs) are increasingly targeting WordPress installations as entry points into larger organizational networks. These sophisticated attacks establish long-term access to WordPress sites, using them as launching points for broader network compromise. APTs often remain undetected for months or years, making early detection and prevention critical.
The rise of automated attack tools has democratized cybercrime, allowing less skilled attackers to launch sophisticated attacks against WordPress sites. These tools can automatically scan for vulnerabilities, exploit discovered weaknesses, and establish persistent access without requiring deep technical knowledge from the attacker.
Understanding these evolving threats provides the foundation for implementing comprehensive WordPress security best practices that address both current and emerging risks. The following sections will detail specific security measures designed to protect against these threats while maintaining the functionality and performance that make WordPress the world’s most popular content management system.
2 Building Your WordPress Security Foundation
Establishing a robust security foundation is the cornerstone of effective WordPress security best practices. This foundation consists of fundamental security measures that must be implemented before advancing to more sophisticated protection strategies. Without these essential elements in place, even the most advanced security tools cannot provide adequate protection against modern threats.
2.1 WordPress Core, Plugin, and Theme Updates
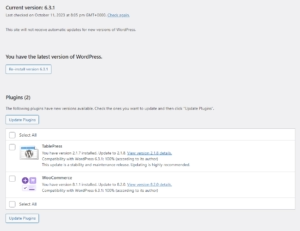
Maintaining current software versions represents the single most critical WordPress security measure you can implement. Security updates often patch critical vulnerabilities that attackers actively exploit, making timely updates essential for maintaining site security.
WordPress core updates are released regularly, with security updates receiving immediate priority. The WordPress development team follows responsible disclosure practices, coordinating with security researchers to ensure patches are available before vulnerability details become public. However, this coordination window is often measured in days rather than weeks, making rapid update deployment crucial.
Implementing automated updates for WordPress core security releases provides the fastest protection against newly discovered vulnerabilities. Configure your WordPress installation to automatically apply security updates while maintaining manual control over major version updates that might affect site functionality. This approach ensures critical security patches are applied immediately while preserving your ability to test major changes before implementation.
Plugin update management requires a more nuanced approach due to the varying quality and security practices among plugin developers. Establish a systematic process for evaluating and applying plugin updates, prioritizing security releases while testing functionality changes in a staging environment. Monitor plugin changelogs and security advisories to identify critical updates that require immediate attention.
Create a plugin inventory that tracks all installed plugins, their current versions, last update dates, and security histories. This inventory enables rapid identification of plugins that may be abandoned, outdated, or frequently affected by security issues. Remove or replace plugins that demonstrate poor security practices or lack regular maintenance.
Theme updates often receive less attention than plugin updates, but themes can contain serious security vulnerabilities that provide attackers with direct access to your website. Establish the same systematic approach for theme updates as you use for plugins, paying particular attention to custom themes that may not receive regular security updates.
2.2 Strong Authentication and User Management
Authentication security forms the foundation of access control for your WordPress site. Weak authentication practices create opportunities for unauthorized access that can compromise even the most sophisticated security measures implemented elsewhere in your system.
Password security extends beyond simple complexity requirements. Implement comprehensive password policies that require unique, strong passwords for all user accounts while providing tools and education to help users comply with these requirements. Consider implementing password strength meters and providing guidance on creating memorable yet secure passwords.
User role management requires careful attention to the principle of least privilege. Assign users the minimum permissions necessary to perform their required functions, regularly reviewing and adjusting permissions as roles change. Avoid creating unnecessary administrative accounts and implement processes for promptly removing access when users no longer require it.
Session management controls how long users remain authenticated and under what conditions their sessions expire. Configure session timeouts that balance security with user convenience, implementing shorter timeouts for administrative accounts and longer timeouts for regular users. Consider implementing automatic logout for idle sessions and requiring re-authentication for sensitive operations.
Login security measures should include protection against brute force attacks, which remain one of the most common attack vectors against WordPress sites. Implement login attempt limiting that temporarily blocks IP addresses after multiple failed login attempts. Configure these limits to balance security with legitimate user access, considering that users occasionally forget passwords or make typing errors.
Consider implementing additional login security measures such as CAPTCHA verification for login forms, security questions for password resets, and email notifications for successful logins from new devices or locations. These measures provide additional layers of protection while alerting users to potential unauthorized access attempts.
2.3 Secure Hosting Environment
Your hosting environment provides the foundation upon which all other security measures are built. A secure hosting provider implements server-level protections that complement your WordPress-specific security measures, while an insecure hosting environment can undermine even the most comprehensive security implementations.
Evaluate hosting providers based on their security practices, infrastructure protection, and incident response capabilities. Look for providers that implement regular security updates, network monitoring, intrusion detection, and DDoS protection at the infrastructure level. Avoid shared hosting environments where possible, as they create opportunities for cross-site contamination and limit your control over security configurations.
Choose hosting providers that offer regular automated backups with easy restoration capabilities. While backups don’t prevent security incidents, they provide essential recovery capabilities when incidents occur. Ensure backups are stored securely, preferably in geographically separate locations, and test restoration procedures regularly to verify backup integrity.
Server-level security configurations should include proper file permissions, secure PHP configurations, and disabled unnecessary services. Work with your hosting provider to ensure server configurations follow security best practices, including disabling dangerous PHP functions, implementing proper file upload restrictions, and configuring secure database access.
Consider managed WordPress hosting services that specialize in WordPress security and performance optimization. These services often provide additional security features such as malware scanning, automatic security updates, and specialized WordPress firewalls that complement your site-level security measures.
Database security requires attention to both access controls and configuration settings. Ensure your WordPress database uses strong authentication credentials, restricts access to necessary connections only, and implements regular security updates. Consider database encryption for sensitive data and implement regular database security audits.
Network security measures should include firewalls, intrusion detection systems, and network monitoring capabilities. While these measures are typically managed by your hosting provider, understand what protections are in place and how they complement your WordPress-specific security implementations.
For comprehensive guidance on selecting and configuring secure hosting environments, review our detailed analysis of secure WordPress hosting options and best practices for hosting security configuration.
The security foundation established through proper updates, authentication, and hosting provides the platform for implementing more advanced WordPress security hardening techniques. Without this foundation, advanced security measures cannot provide adequate protection against the sophisticated threats targeting WordPress sites in 2025. The next section will build upon this foundation with advanced hardening techniques that provide comprehensive protection against current and emerging threats.
3 Advanced WordPress Security Hardening Techniques
Advanced WordPress security hardening goes beyond basic security measures to implement comprehensive protection against sophisticated attack vectors. These techniques require deeper technical knowledge but provide essential protection against the advanced threats targeting WordPress sites in 2025.
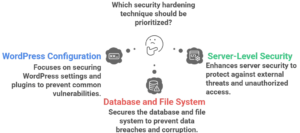
3.1WordPress Configuration Security
WordPress configuration security involves modifying core WordPress settings and files to eliminate common attack vectors and reduce the attack surface available to potential intruders. These modifications require careful implementation to maintain site functionality while maximizing security protection.
The wp-config.php file contains critical security settings that can significantly impact your site’s security posture. Implement security keys and salts that provide cryptographic protection for user sessions and cookies. WordPress provides a security key generator that creates unique keys for your installation. Regenerate these keys periodically to maintain their effectiveness.
Database security configuration should include changing the default database table prefix from “wp_” to a unique value that makes automated attacks more difficult. This change requires careful implementation during initial WordPress installation or through systematic database migration for existing sites. Additionally, implement database user accounts with minimal necessary privileges rather than using administrative database accounts for WordPress operations.
File editing restrictions prevent attackers who gain administrative access from modifying theme and plugin files directly through the WordPress admin interface. Add the following line to your wp-config.php file to disable file editing: define(‘DISALLOW_FILE_EDIT’, true);. This setting forces all file modifications to occur through secure file transfer methods rather than the potentially compromised web interface.
Debug mode should be disabled on production sites to prevent information disclosure that could assist attackers. Ensure WP_DEBUG is set to false in your wp-config.php file and implement proper error logging that doesn’t expose sensitive information to site visitors. Configure error logs to be stored outside the web-accessible directory structure.
3.2 Server-Level Security Measures
Server-level security provides the foundation for all WordPress security measures. These configurations protect against attacks that target the underlying server infrastructure rather than WordPress-specific vulnerabilities.
Web Application Firewall (WAF) implementation provides real-time protection against common attack patterns and malicious traffic. A properly configured WAF can block SQL injection attempts, cross-site scripting attacks, and other common web application attacks before they reach your WordPress installation. Choose WAF solutions that provide WordPress-specific rule sets and regular updates to address emerging threats.
Configure your WAF to implement rate limiting that prevents brute force attacks and other automated attack attempts. Set appropriate thresholds that block suspicious traffic patterns while allowing legitimate user access. Monitor WAF logs regularly to identify attack trends and adjust configurations as needed.
HTTP security headers provide additional protection against various attack vectors. Implement Content Security Policy (CSP) headers that restrict resource loading to trusted sources, preventing code injection attacks. Configure X-Frame-Options headers to prevent clickjacking attacks, and implement X-Content-Type-Options headers to prevent MIME type sniffing attacks.
Server software security requires maintaining current versions of all server components, including the web server, PHP, database server, and operating system. Implement automated security updates for critical components while maintaining testing procedures for updates that might affect functionality.
File upload restrictions prevent attackers from uploading malicious files that could compromise your server. Configure your web server to restrict file uploads to specific directories and file types, implementing virus scanning for uploaded files when possible. Ensure uploaded files cannot be executed as scripts by configuring appropriate file permissions and server settings.
3.3 Database and File System Security
Database security extends beyond basic access controls to include comprehensive protection against data theft, corruption, and unauthorized modification. These measures protect the valuable data stored in your WordPress database while maintaining the performance and functionality required for normal operation.
Database access controls should implement the principle of least privilege, creating database users with only the permissions necessary for WordPress operation. Avoid using administrative database accounts for WordPress connections, instead creating dedicated accounts with limited privileges. Regularly audit database permissions and remove unnecessary access.
Database encryption provides protection for sensitive data stored in your WordPress database. Implement encryption for personally identifiable information, payment data, and other sensitive content. Consider using WordPress plugins that provide transparent database encryption or implement database-level encryption through your hosting provider.
Regular database backups are essential for recovery from security incidents, but backup security is equally important. Ensure database backups are encrypted during storage and transmission, stored in secure locations with appropriate access controls, and tested regularly to verify integrity and restoration capabilities.
File system security requires careful attention to file permissions, directory structures, and access controls. WordPress requires specific file permissions to function properly, but overly permissive settings can create security vulnerabilities. Implement the minimum file permissions necessary for WordPress operation: 644 for files and 755 for directories in most cases.
Critical WordPress files require additional protection beyond standard file permissions. The wp-config.php file contains sensitive database credentials and security keys that must be protected from unauthorized access. Consider moving this file outside the web-accessible directory structure or implementing additional access controls through server configuration.
Directory browsing should be disabled to prevent attackers from viewing directory contents and identifying potential targets. Configure your web server to return 403 Forbidden errors for directory access attempts rather than displaying directory listings. This configuration prevents information disclosure that could assist attackers in identifying vulnerable files or directories.
File integrity monitoring provides early detection of unauthorized file modifications that could indicate a security compromise. Implement monitoring systems that track changes to critical WordPress files and alert you to unexpected modifications. This monitoring should include WordPress core files, theme files, plugin files, and configuration files.
Implement secure file upload handling that validates file types, scans for malware, and stores uploaded files in secure locations. Configure upload directories with appropriate permissions that prevent uploaded files from being executed as scripts. Consider implementing additional security measures such as file quarantine and manual review for certain file types.
These advanced hardening techniques provide comprehensive protection against sophisticated attack vectors while maintaining the functionality and performance that make WordPress an effective platform for your website. The implementation of these measures requires careful planning and testing, but the security benefits justify the investment in proper implementation and ongoing maintenance.
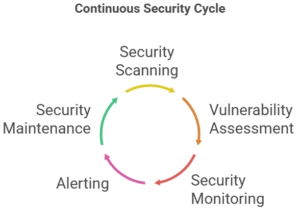
4 Continuous Security Monitoring and Maintenance
Effective WordPress security measures extend beyond initial implementation to include ongoing monitoring, maintenance, and response capabilities. Continuous security monitoring provides early detection of threats and vulnerabilities while systematic maintenance ensures your security measures remain effective against evolving attack vectors.
4.1Security Scanning and Vulnerability Assessment
Regular security scanning forms the backbone of proactive WordPress security best practices. Automated scanning tools can identify vulnerabilities, malware, and security misconfigurations that might otherwise go undetected until they’re exploited by attackers.
Implement comprehensive vulnerability scanning that examines your WordPress core, plugins, themes, and server configuration for known security issues. Choose scanning tools that maintain current vulnerability databases and provide detailed remediation guidance for identified issues. Schedule automated scans to run regularly while maintaining the ability to initiate immediate scans when new threats emerge.
Malware detection requires specialized scanning capabilities that can identify malicious code, backdoors, and other indicators of compromise. Modern malware often uses sophisticated obfuscation techniques to avoid detection, making advanced scanning algorithms essential for effective detection. Implement scanning solutions that use multiple detection methods, including signature-based detection, behavioral analysis, and heuristic scanning.
File integrity monitoring provides real-time detection of unauthorized changes to critical WordPress files. This monitoring should include WordPress core files, theme files, plugin files, and configuration files. Configure monitoring systems to alert you immediately when unexpected changes occur, enabling rapid response to potential security incidents.
Website blacklist monitoring ensures your site hasn’t been flagged by search engines or security vendors as containing malware or engaging in malicious activities. Being blacklisted can devastate your search engine rankings and user trust, making early detection and remediation critical. Implement monitoring services that check major blacklists regularly and provide immediate alerts when issues are detected.
Performance impact assessment should be included in your security scanning strategy. Security measures that significantly impact site performance may be disabled or bypassed, reducing their effectiveness. Monitor the performance impact of security tools and configurations, optimizing settings to maintain both security and performance.
4.2 Security Monitoring and Alerting
Real-time security monitoring provides immediate detection of active attacks and security incidents. This monitoring capability enables rapid response that can minimize damage and prevent successful compromises.
Log analysis forms the foundation of effective security monitoring. Configure comprehensive logging that captures security-relevant events including login attempts, file modifications, database queries, and administrative actions. Implement log analysis tools that can identify suspicious patterns and generate alerts for potential security incidents.
Intrusion detection systems (IDS) provide automated monitoring for attack patterns and suspicious activities. Configure IDS solutions to monitor network traffic, system activities, and application behaviors for indicators of compromise. Tune detection rules to minimize false positives while maintaining sensitivity to genuine threats.
Failed login monitoring provides early detection of brute force attacks and credential stuffing attempts. Configure monitoring systems to track failed login attempts, identify suspicious patterns, and implement automatic response measures such as IP blocking or account lockouts. Balance security with user convenience by implementing progressive response measures that escalate based on threat severity.
Administrative action monitoring tracks changes to critical WordPress settings, user accounts, and security configurations. This monitoring provides audit trails for security-relevant changes and can detect unauthorized modifications that might indicate a compromise. Configure alerts for high-risk administrative actions such as user creation, permission changes, and security setting modifications.
Traffic pattern analysis can identify various types of attacks including DDoS attempts, bot traffic, and automated scanning activities. Configure monitoring systems to establish baseline traffic patterns and alert you to significant deviations that might indicate attack activities. This monitoring should include both volume-based detection and pattern-based analysis.
4.3 Regular Security Maintenance
Systematic security maintenance ensures your WordPress security measures remain effective over time. This maintenance includes regular updates, configuration reviews, and security assessments that adapt to changing threat landscapes and site requirements.
Security audit schedules should include regular comprehensive reviews of your entire security posture. These audits should examine security configurations, access controls, monitoring systems, and incident response procedures. Schedule quarterly comprehensive audits with monthly focused reviews of critical security components.
Update management requires systematic processes for evaluating, testing, and implementing security updates. Develop procedures that prioritize security updates while maintaining site stability and functionality. This process should include staging environment testing, rollback procedures, and emergency update protocols for critical security issues.
Security configuration reviews examine your security settings and tools to ensure they remain properly configured and effective. Security tools may require periodic reconfiguration as threats evolve or site requirements change. Schedule regular reviews of firewall rules, monitoring configurations, and security plugin settings.
Backup verification ensures your backup systems remain functional and capable of supporting recovery from security incidents. Regularly test backup restoration procedures to verify backup integrity and restoration capabilities. This testing should include both full site restoration and selective file recovery scenarios.
Performance monitoring ensures security measures don’t negatively impact site functionality or user experience. Monitor site performance metrics regularly and investigate any degradation that might be related to security implementations. Optimize security configurations to maintain both protection and performance.
5 WordPress Security Compliance and Business Impact
Modern WordPress security best practices must address not only technical protection but also regulatory compliance and business impact considerations. Understanding these requirements is essential for organizations that handle sensitive data or operate in regulated industries.
5.1 Regulatory Compliance Requirements
Data protection regulations have fundamentally changed the security requirements for WordPress sites that collect, process, or store personal information. These regulations impose specific technical and administrative requirements that must be integrated into your overall security strategy.
GDPR compliance affects any WordPress site that processes personal data of EU residents, regardless of where the site is hosted or the organization is located. GDPR requires implementing appropriate technical and organizational measures to protect personal data, including encryption, access controls, and breach notification procedures. WordPress sites must implement privacy by design principles, data minimization practices, and user rights management capabilities.
Implement GDPR-compliant data handling procedures that include user consent management, data retention policies, and data subject rights fulfillment. Configure your WordPress site to provide users with access to their personal data, the ability to correct inaccuracies, and the right to data deletion. Document your data processing activities and implement procedures for responding to data subject requests within required timeframes.
PCI DSS compliance is mandatory for WordPress sites that process credit card payments. These requirements include network security, access controls, encryption, and regular security testing. Implement PCI DSS-compliant payment processing that uses secure payment gateways, encrypts cardholder data, and maintains secure network configurations.
Industry-specific regulations may impose additional security requirements depending on your business sector. Financial services, government contractors, and other regulated industries often have specific cybersecurity requirements that must be integrated into your WordPress security implementation.
5.2 Business Impact and ROI
Understanding the business impact of security investments helps justify the resources required for comprehensive WordPress security measures while demonstrating the value of proactive security management.
The cost of security breaches extends far beyond immediate technical remediation. Data breaches can result in regulatory fines, legal liability, customer notification costs, credit monitoring services, and business disruption. The average cost of a data breach in 2024 reached $4.88 million globally, with costs varying significantly based on industry, breach size, and response effectiveness.
Reputation damage from security incidents can have long-lasting business impact that extends beyond immediate financial costs. Customer trust, once lost, can be difficult and expensive to rebuild. Search engine penalties for compromised sites can devastate organic traffic and online visibility. Partner and vendor relationships may be affected by security incidents that raise questions about your organization’s security practices.
Security investment ROI should be calculated based on risk reduction rather than simple cost avoidance. Effective security measures reduce the probability and potential impact of security incidents, providing measurable value through risk mitigation. Calculate ROI by comparing security investment costs against the expected value of prevented losses, including direct costs, business disruption, and reputation damage.
Business continuity planning should integrate security incident response with broader business continuity procedures. Security incidents can disrupt business operations, making rapid recovery capabilities essential for minimizing business impact. Develop incident response procedures that prioritize business continuity while ensuring thorough security remediation.
5.3Legal and Liability Considerations
Legal liability for security incidents has increased significantly as data protection regulations impose specific obligations on organizations that handle personal data. Understanding these legal requirements is essential for implementing adequate protection and managing potential liability.
Data protection obligations vary by jurisdiction but generally include requirements for implementing appropriate security measures, notifying authorities and affected individuals of breaches, and maintaining records of data processing activities. Failure to meet these obligations can result in significant regulatory fines and legal liability.
Breach notification requirements typically mandate reporting security incidents to regulatory authorities within specific timeframes, often 72 hours for GDPR violations. Implement incident response procedures that enable rapid breach assessment and notification compliance. Maintain documentation of security measures and incident response activities to demonstrate compliance efforts.
Contractual obligations may impose additional security requirements through customer contracts, vendor agreements, or partnership arrangements. Review all contracts that involve data sharing or processing to understand specific security obligations and ensure your WordPress security implementation meets these requirements.
Liability limitations can be achieved through appropriate insurance coverage, contractual provisions, and compliance with applicable security standards. While comprehensive security measures cannot eliminate all liability, demonstrating reasonable security practices can significantly reduce legal exposure and potential damages.
Professional security services may be necessary for organizations with complex compliance requirements or limited internal security expertise. Consider engaging security professionals for regular assessments, compliance audits, and incident response support. Document these professional relationships to demonstrate commitment to maintaining appropriate security measures.
6 Implementing Professional Security with Security Ninja
Professional WordPress security measures require comprehensive tools that can implement, monitor, and maintain advanced security configurations without requiring extensive technical expertise. Security Ninja provides enterprise-level security capabilities specifically designed for WordPress environments, offering the comprehensive protection needed to address modern threat landscapes.
6.1 Security Ninja Feature Overview
Security Ninja represents a comprehensive approach to WordPress security best practices, combining automated security testing, real-time monitoring, and professional-grade protection in a single, integrated platform. The plugin addresses the full spectrum of WordPress security requirements, from basic hardening to advanced threat detection and response.
Comprehensive security testing capabilities examine over 50 different security aspects of your WordPress installation, including core security settings, plugin vulnerabilities, theme security issues, server configuration problems, and database security concerns. These tests go beyond simple vulnerability scanning to provide detailed analysis of your security posture with specific remediation guidance for identified issues.
Real-time monitoring provides continuous surveillance of your WordPress site for security threats, unauthorized changes, and suspicious activities. This monitoring includes file integrity checking, login monitoring, malware detection, and blacklist monitoring that provides immediate alerts when security issues are detected.
Professional reporting capabilities provide detailed security assessments that can be used for compliance documentation, security audits, and stakeholder communication. These reports include executive summaries, technical details, and remediation priorities that support both technical implementation and business decision-making.
Integration capabilities allow Security Ninja to work seamlessly with other security tools and services, providing a comprehensive security ecosystem rather than a standalone solution. This integration includes compatibility with popular backup plugins, CDN services, and hosting security features.
6.2 Implementation Best Practices
Successful Security Ninja implementation requires systematic planning and configuration that aligns with your specific security requirements and operational constraints. This implementation should integrate with your existing security measures while providing enhanced protection and monitoring capabilities.
Initial security assessment should be the first step in Security Ninja implementation. Run comprehensive security tests to establish a baseline understanding of your current security posture and identify priority areas for improvement. This assessment provides the foundation for developing a systematic security improvement plan.
Configuration optimization involves adjusting Security Ninja settings to match your specific security requirements and operational needs. This optimization should balance security protection with site performance and functionality, ensuring security measures don’t negatively impact user experience or business operations.
Monitoring configuration requires setting up appropriate alert thresholds and notification methods that provide timely security information without creating alert fatigue. Configure monitoring to provide immediate alerts for critical security issues while providing regular reports for less urgent security information.
Integration with existing security tools should be planned to avoid conflicts and ensure comprehensive coverage. Review your current security implementations to identify potential overlaps or gaps that Security Ninja can address. Configure Security Ninja to complement rather than duplicate existing security measures.
6.3 Advanced Security Features
Security Ninja’s advanced features provide enterprise-level protection capabilities that address sophisticated threats and complex security requirements. These features enable comprehensive security implementation that rivals dedicated security appliances and professional security services.
Custom security rules allow you to implement organization-specific security requirements that go beyond standard security best practices. These rules can address industry-specific compliance requirements, organizational security policies, and unique threat profiles that require customized protection measures.
Advanced threat detection uses multiple detection methods to identify sophisticated attacks that might evade traditional security measures. This detection includes behavioral analysis, pattern recognition, and anomaly detection that can identify zero-day attacks and advanced persistent threats.
Incident response automation provides immediate response to detected security threats, reducing the time between threat detection and remediation. This automation can include automatic IP blocking, file quarantine, user account suspension, and administrator notification that minimizes the impact of security incidents.
Compliance reporting features generate detailed reports that support regulatory compliance requirements and security audit processes. These reports can be customized to address specific compliance frameworks and provide the documentation required for regulatory submissions and audit responses.
Performance optimization ensures security measures don’t negatively impact site speed or functionality. Security Ninja implements intelligent caching, optimized scanning schedules, and resource management that maintains comprehensive protection while preserving site performance.
Security Ninja represents the culmination of years of WordPress security research and development, providing comprehensive protection that addresses the full spectrum of WordPress security requirements. The plugin’s combination of automated testing, real-time monitoring, and professional reporting makes it an essential tool for any organization serious about WordPress security.
7 Your WordPress Security Implementation Roadmap
Implementing comprehensive WordPress security best practices requires systematic planning and phased execution that balances security improvement with operational continuity. This roadmap provides a structured approach to implementing the security measures outlined in this guide while maintaining site functionality and performance.
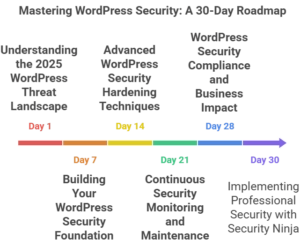
7.1 30-Day Security Implementation Timeline
The first 30 days of security implementation should focus on establishing fundamental security measures that provide immediate protection against the most common threats. This foundation enables more advanced security implementations while providing measurable security improvements.
Implement strong authentication measures including complex passwords for all user accounts and two-factor authentication for administrative accounts. Review and optimize user permissions to ensure all accounts have appropriate access levels without unnecessary privileges.
Configure automated WordPress core security updates to ensure critical security patches are applied immediately. Review and update all plugins and themes to current versions, removing any unused or outdated components that could present security risks.
Establish comprehensive backup procedures with automated daily backups stored in secure, geographically separate locations. Test backup restoration procedures to ensure recovery capabilities are functional and reliable.
Configure security monitoring and alerting systems that provide real-time notification of security threats and suspicious activities. Establish monitoring baselines and alert thresholds that balance security awareness with operational efficiency.
Establish security maintenance procedures including regular security audits, access control reviews, and security configuration updates. Document these procedures to ensure consistent implementation and enable delegation to appropriate team members.
Configure performance monitoring to ensure security measures don’t negatively impact site functionality or user experience. Optimize security configurations to maintain both protection and performance.
Document your security implementation including configurations, procedures, and contact information for security incident response. This documentation supports compliance requirements and enables effective incident response.
Conduct comprehensive security testing to verify all implemented measures are functioning correctly and providing expected protection. This testing should include vulnerability scanning, penetration testing, and security configuration validation.
7.2 -Based Action Items
Security implementation should prioritize measures based on risk reduction potential and implementation complexity. This prioritization ensures the most critical security improvements are implemented first while building toward comprehensive protection.
Critical Priority (Immediate Implementation)
-
WordPress core, plugin, and theme updates
-
Strong authentication and two-factor authentication
-
Automated security scanning and monitoring
-
Comprehensive backup implementation
-
Basic security hardening (wp-config.php, file permissions)
High Priority (Within 30 Days)
-
Advanced security hardening (server configuration, database security)
-
Security monitoring and alerting systems
-
Incident response procedures and documentation
-
Compliance requirement implementation
-
Security training for team members
Medium Priority (Within 90 Days)
-
Advanced threat detection and response automation
-
Comprehensive security auditing and reporting
-
Performance optimization of security measures
-
Integration with additional security tools and services
-
Regular security assessment and improvement procedures
Ongoing Maintenance (Continuous)
-
Regular security updates and patch management
-
Continuous security monitoring and threat detection
-
Periodic security audits and assessments
-
Security training updates and awareness programs
-
Incident response testing and procedure updates
Ongoing Security Maintenance Schedule
Sustainable WordPress security measures require systematic ongoing maintenance that adapts to changing threats and evolving site requirements. This maintenance schedule ensures your security implementation remains effective over time.
Daily Maintenance
-
Monitor security alerts and notifications
-
Review backup completion and integrity
-
Check for critical security updates
-
Monitor site performance and functionality
-
Review security logs for suspicious activities
Weekly Maintenance
-
Comprehensive security scanning
-
Review and apply non-critical security updates
-
Audit user access and permissions
-
Performance monitoring and optimization
-
Security configuration review and updates
Monthly Maintenance
-
Comprehensive security audit and assessment
-
Review and update security documentation
-
Test incident response procedures
-
Evaluate new security threats and countermeasures
-
Review compliance requirements and implementation
Quarterly Maintenance
-
Comprehensive penetration testing and vulnerability assessment
-
Review and update security policies and procedures
-
Evaluate security tool effectiveness and optimization
-
Conduct security training updates for team members
-
Review and update incident response plans
7.3 Professional Security Support
Complex WordPress security implementations may require professional expertise to ensure comprehensive protection and regulatory compliance. Consider engaging security professionals for specialized requirements or when internal expertise is limited.
Professional security assessments provide independent evaluation of your security implementation and identification of potential improvements. These assessments can validate your security measures, identify gaps, and provide recommendations for enhancement.
Incident response support ensures rapid, effective response to security incidents that minimizes damage and enables quick recovery. Professional incident response services provide expertise and resources that may not be available internally.
Compliance consulting helps navigate complex regulatory requirements and ensures your WordPress security implementation meets applicable standards. This consulting is particularly valuable for organizations in regulated industries or those handling sensitive data.
Ongoing security management services provide continuous monitoring, maintenance, and improvement of your WordPress security implementation. These services can supplement internal capabilities or provide complete security management for organizations without dedicated security resources.
8 Conclusion
Implementing comprehensive WordPress security best practices in 2025 requires a systematic approach that addresses both current threats and emerging risks. The security measures outlined in this guide provide the foundation for protecting your WordPress site against the sophisticated attacks targeting websites today.
The investment in proper WordPress security implementation is minimal compared to the potential cost of a security breach. By following these proven WordPress security measures, you protect not only your website and data but also your business reputation, customer trust, and regulatory compliance.
Security is not a one-time implementation but an ongoing process that requires continuous attention and adaptation. The threat landscape continues to evolve, making regular security updates, monitoring, and improvement essential for maintaining effective protection.
Security Ninja provides the comprehensive tools and capabilities needed to implement and maintain enterprise-level WordPress security. The plugin’s combination of automated testing, real-time monitoring, and professional reporting makes it an essential component of any serious WordPress security strategy.
Start implementing these WordPress security best practices today to protect your website against current and emerging threats. Your website’s security is too important to leave to chance, and the tools and knowledge needed for comprehensive protection are readily available.
The security of your WordPress site is ultimately your responsibility, but with the right approach, tools, and ongoing commitment, you can achieve the comprehensive protection needed to operate safely in today’s threat environment. Implement these security measures systematically, maintain them consistently, and adapt them as threats evolve to ensure your WordPress site remains secure and trustworthy for years to come.
Frequently Asked Questions
Q: How often should I update my WordPress security measures? A: WordPress core security updates should be applied immediately, while plugin and theme updates should be applied weekly after testing. Comprehensive security reviews should be conducted monthly with major assessments quarterly.
Q: What is the most important WordPress security measure? A: Keeping WordPress core, plugins, and themes updated is the single most critical security measure, as it addresses the majority of known vulnerabilities that attackers actively exploit.
Q: How do I know if my WordPress site has been compromised? A: Signs of compromise include unexpected file changes, new user accounts, unusual traffic patterns, blacklist warnings, and performance degradation. Regular security scanning can detect many compromise indicators.
Q: Is free WordPress security sufficient for business websites? A: While free security tools provide basic protection, business websites typically require professional security solutions that offer comprehensive monitoring, advanced threat detection, and compliance support.
Q: How much should I budget for WordPress security? A: Security costs vary based on site complexity and requirements, but typically range from $200-2000 annually for comprehensive protection. This investment is minimal compared to the potential cost of a security breach.
Related Articles:
- Complete WordPress Security Guide
- WordPress Vulnerabilities Database
- WordPress Malware Removal Guide
- WordPress Login Security Guide
- WordPress Security Audit Guide
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.