Updated on
WordPress Security audits have become essential for maintaining robust website protection in today’s evolving threat landscape. With over 43% of websites powered by WordPress, cybercriminals increasingly target WordPress installations through sophisticated attack vectors that require comprehensive security assessment and evaluation.
A professional WordPress security audit provides systematic evaluation of your website’s security posture, identifying vulnerabilities before malicious actors can exploit them. Unlike basic security scans, comprehensive security audits examine every aspect of your WordPress installation, from core configuration and plugin security to hosting infrastructure and compliance requirements.
The WordPress security audit process involves detailed vulnerability assessment, risk analysis, and remediation planning that protects your digital assets while ensuring regulatory compliance. Professional security audits conducted by certified experts like those at WP Security Ninja provide actionable insights that strengthen your security posture and reduce business risk.
This complete WordPress security audit guide for 2025 covers advanced audit methodologies, professional assessment tools, and proven security evaluation techniques. Whether you’re conducting internal security assessments or engaging professional audit services, this comprehensive guide provides the framework for thorough WordPress security evaluation that protects your website, user data, and business reputation.
Contents
- 1 1 WordPress Security Audit Fundamentals
- 2 2 Pre-Audit Planning and Preparation
- 3 3 WordPress Core Security Audit
- 4 4 Plugin and Theme Security Audit
- 5 5 Infrastructure and Hosting Security Audit
- 6 6 Security Audit Tools and Automation
- 7 7 Audit Reporting and Remediation
- 8 8 Conclusion: Professional WordPress Security Audit Excellence
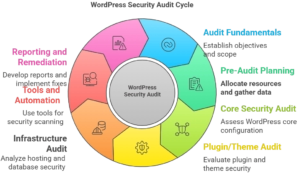
1 WordPress Security Audit Fundamentals
Understanding WordPress security audit fundamentals forms the foundation for effective security assessment and vulnerability evaluation. Professional security audits follow established methodologies that ensure comprehensive coverage of all potential attack vectors and security weaknesses.
1.1 Security Audit Objectives and Scope
Business Risk Assessment and Security Posture Evaluation
WordPress security audits begin with comprehensive business risk assessment that identifies critical assets, potential threats, and acceptable risk levels. Security posture evaluation examines current protection measures against industry standards and regulatory requirements, establishing baseline security metrics for improvement tracking.
Effective security audit objectives include vulnerability identification, compliance validation, risk prioritization, and remediation planning. Professional auditors assess business impact potential, data protection requirements, and operational continuity needs to develop targeted audit scope that addresses specific organizational requirements.
Compliance Requirements and Regulatory Considerations
Security audit scope definition includes compliance mapping, regulatory requirement assessment, and documentation standards that support audit trails and regulatory reporting. Professional audit services integrate compliance evaluation with security assessment to provide comprehensive protection that meets both security and regulatory objectives.
Audit Scope Definition and Boundary Establishment
Comprehensive WordPress security audit scope encompasses core WordPress installation, active plugins and themes, hosting infrastructure, user access controls, and data protection measures. Audit boundary establishment defines assessment limits, exclusions, and special considerations that guide audit execution.
1.2 Audit Methodology and Framework
Industry-Standard Audit Frameworks
Professional WordPress security audits follow established frameworks including NIST Cybersecurity Framework, ISO 27001 security standards, and OWASP security testing methodology. These frameworks provide structured approaches that ensure comprehensive coverage and consistent results.
Security audit methodology incorporates risk-based assessment, threat modeling, and vulnerability analysis that identifies security gaps and prioritizes remediation efforts. Professional auditors combine automated scanning with manual testing to provide thorough security evaluation that addresses both technical and operational security concerns.
Risk-Based Audit Approach and Prioritization
Effective WordPress security audits employ risk-based approaches that focus assessment efforts on highest-impact vulnerabilities and most critical assets. Risk prioritization considers threat likelihood, business impact potential, and remediation complexity to optimize security investment and protection effectiveness.
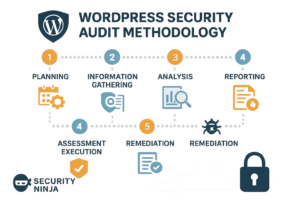
Audit Phases and Milestone Planning
Comprehensive WordPress security audits follow structured phases including planning, information gathering, assessment execution, analysis, reporting, and remediation support. Milestone planning ensures systematic progress and stakeholder communication throughout the audit process.
Professional audit phases include pre-audit preparation, automated scanning, manual testing, vulnerability validation, risk analysis, and detailed reporting with remediation guidance. Each phase includes specific deliverables and validation criteria that ensure audit quality and completeness.
1.3 Security Ninja Professional Audit Services
WP Security Ninja provides comprehensive WordPress security audit services that combine automated assessment tools with expert analysis and professional consultation. Our certified security professionals deliver thorough security evaluation that identifies vulnerabilities and provides actionable remediation guidance.
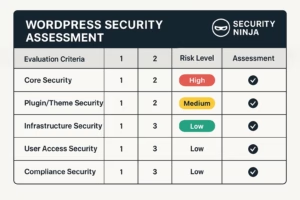
Comprehensive Security Assessment with 50+ Evaluation Criteria
Security Ninja’s professional audit services include comprehensive evaluation across 50+ security criteria covering WordPress core security, plugin and theme assessment, hosting infrastructure review, and compliance validation. Our systematic approach ensures complete coverage of all potential security vulnerabilities and configuration weaknesses.
Expert Security Consultants and Certified Professionals
Our professional audit team includes certified security professionals with extensive WordPress expertise and industry certifications including CISSP, CEH, and OSCP. Expert consultants provide specialized knowledge in WordPress security, web application testing, and compliance requirements.
Professional consultation includes security strategy development, remediation planning, and ongoing security guidance that supports long-term protection improvement. Our experts work closely with your team to ensure audit findings are properly understood and effectively implemented.
Customized Audit Methodology Based on Business Requirements
Security Ninja develops customized audit methodologies tailored to specific business requirements, industry regulations, and risk profiles. Our flexible approach ensures audit scope and depth align with organizational needs and resource constraints.
2 Pre-Audit Planning and Preparation
Effective WordPress security audit planning and preparation establish the foundation for successful security assessment and meaningful results. Professional audit preparation includes resource allocation, information gathering, and baseline establishment that guide audit execution and ensure comprehensive coverage.
2.1 Audit Planning and Resource Allocation
Audit Team Composition and Skill Requirements
Professional WordPress security audit teams include certified security professionals, WordPress specialists, and compliance experts with complementary skills and experience. Team composition varies based on audit scope, complexity, and specialized requirements such as compliance assessment or penetration testing.
Timeline Development and Milestone Scheduling
Comprehensive WordPress security audit timeline development includes planning phase, information gathering, assessment execution, analysis, reporting, and remediation support. Professional timeline scheduling considers audit scope, resource availability, and business constraints to optimize audit efficiency and minimize operational disruption.
Milestone scheduling includes specific deliverables, review points, and stakeholder communication that ensure audit progress and quality. Professional project management ensures timely completion while maintaining thorough assessment coverage and detailed documentation.
Resource Allocation and Budget Planning
WordPress security audit resource allocation includes personnel, tools, and infrastructure requirements that support comprehensive assessment and professional reporting. Budget planning considers audit scope, timeline, and specialized requirements such as compliance assessment or penetration testing.
2.2 Information Gathering and Asset Inventory
WordPress Installation Documentation and Configuration
Comprehensive WordPress security audit preparation includes detailed documentation of WordPress installation, configuration settings, and customization details. Asset inventory covers WordPress version, installed plugins and themes, user accounts, and hosting environment specifications.
Professional information gathering includes configuration baseline establishment, change management documentation, and security policy review that provide audit context and assessment scope. Detailed documentation ensures comprehensive coverage and accurate vulnerability assessment.
Plugin and Theme Inventory with Version Tracking
WordPress security audit preparation requires complete inventory of all installed plugins and themes with version numbers, update status, and security history. Plugin and theme documentation includes active status, configuration settings, and custom modifications that affect security posture.
User Account and Permission Documentation
Comprehensive user account documentation includes all WordPress users, assigned roles, permission levels, and access history. User permission audit covers administrative access, content management capabilities, and special privileges that affect security posture.
Professional user access review includes account lifecycle management, permission appropriateness, and access control effectiveness that ensures proper security governance. User account security assessment identifies potential privilege escalation risks and access control weaknesses.
2.3 Security Ninja Audit Preparation
WP Security Ninja provides comprehensive audit preparation services that streamline assessment execution and ensure thorough coverage. Our automated preparation tools and expert consultation optimize audit efficiency while maintaining professional quality standards.
Automated Asset Discovery and Inventory Management
Security Ninja’s automated asset discovery tools provide comprehensive inventory of WordPress installations, plugins, themes, and configuration settings. Automated inventory management ensures complete coverage and accurate documentation that supports thorough security assessment.
Professional asset discovery includes version tracking, vulnerability cross-reference, and security rating assessment that provides immediate risk visibility. Automated tools reduce preparation time while ensuring comprehensive coverage and accurate baseline establishment.
Configuration Baseline Establishment and Documentation
Professional configuration baseline establishment includes security settings documentation, hardening status assessment, and compliance configuration review. Baseline documentation provides audit reference point and change tracking capability that supports ongoing security management.
Pre-Audit Security Scanning and Vulnerability Identification
Comprehensive pre-audit scanning includes automated vulnerability assessment, configuration review, and security posture evaluation that identifies immediate security concerns. Pre-audit scanning provides audit focus areas and priority identification that optimizes assessment efficiency.
Professional pre-audit services include threat intelligence integration, vulnerability prioritization, and risk assessment that guide audit execution. Security Ninja’s scanning capabilities provide comprehensive coverage and expert analysis.
3 WordPress Core Security Audit
WordPress core security audit examines the fundamental security configuration and implementation of your WordPress installation. Professional core security assessment identifies vulnerabilities in WordPress core files, administrative configurations, and security implementations that protect against common attack vectors.
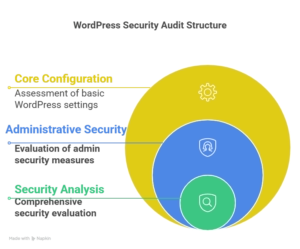
3.1 WordPress Core Configuration Assessment
WordPress Version Verification and Update Status
Comprehensive WordPress core audit begins with version verification and update status assessment. Professional auditors examine WordPress core version, available updates, and update management procedures to identify potential security vulnerabilities and maintenance gaps.
WordPress version assessment includes security patch analysis, vulnerability database cross-reference, and update timeline evaluation that identifies immediate security risks. Professional core assessment ensures current protection against known vulnerabilities and establishes update management best practices.
Core File Integrity Verification and Modification Detection
Professional WordPress core audit includes comprehensive file integrity verification that detects unauthorized modifications, malware injection, and configuration tampering. Core file integrity assessment compares current files against official WordPress checksums to identify potential security compromises.
File integrity monitoring includes hash verification, modification timestamp analysis, and permission assessment that ensures core file security. Professional integrity verification identifies both malicious modifications and unintentional changes that affect security posture.
WordPress core file protection requires regular integrity monitoring and immediate investigation of unauthorized changes. Professional file integrity assessment provides detailed analysis of modifications and recommendations for security restoration and ongoing protection.
Security Configuration Review and Hardening Assessment
Comprehensive WordPress core security configuration review examines security settings, hardening implementations, and protection mechanisms. Professional configuration assessment evaluates security headers, file permissions, directory protection, and access controls that defend against common attacks.
Security hardening assessment includes wp-config.php security review, database security configuration, and administrative access protection evaluation. Professional hardening review identifies configuration weaknesses and provides specific remediation guidance for security improvement.
3.2 Administrative Security Evaluation
User Account Security and Permission Analysis
Professional WordPress administrative security evaluation includes comprehensive user account assessment, permission analysis, and access control review. Administrative security audit examines user roles, privilege assignments, and account management procedures that protect against unauthorized access.
User account security assessment includes password policy evaluation, account lifecycle management, and access monitoring that ensures appropriate security governance. Professional permission analysis identifies privilege escalation risks and access control weaknesses that require remediation.
Administrative Access Control and Privilege Escalation Review
Comprehensive administrative access control review examines privilege assignments, escalation procedures, and administrative function protection. Professional access control assessment evaluates role-based permissions, administrative capabilities, and security boundaries that prevent unauthorized privilege escalation.
Privilege escalation review includes capability analysis, permission inheritance evaluation, and administrative function assessment that identifies potential security vulnerabilities. Professional access control audit ensures appropriate privilege separation and administrative security.
Administrative access protection requires systematic privilege management, regular access review, and strong authentication mechanisms. Professional administrative security assessment provides detailed evaluation and remediation guidance for access control optimization.
Session Management and Authentication Mechanism Assessment
Professional session management assessment examines authentication mechanisms, session security, and access token management. Session security audit includes timeout configuration, session fixation protection, and authentication bypass prevention that ensures secure user sessions.
Authentication mechanism evaluation includes password security, multi-factor authentication implementation, and authentication bypass protection. Professional session assessment identifies authentication vulnerabilities and provides security enhancement recommendations.
3.3 Security Ninja Core Security Analysis
WP Security Ninja provides comprehensive WordPress core security analysis that combines automated assessment with expert evaluation. Our professional core security services identify vulnerabilities and provide actionable remediation guidance for optimal protection.
Automated WordPress Core Security Assessment
Security Ninja’s automated core security assessment includes comprehensive evaluation of WordPress version, file integrity, configuration security, and administrative access controls. Automated assessment provides immediate vulnerability identification and risk prioritization that guides remediation efforts.
Professional automated assessment includes vulnerability database integration, security configuration analysis, and compliance evaluation that ensures comprehensive coverage. Automated tools provide detailed reporting and remediation guidance for efficient security improvement.
WordPress core security assessment requires systematic evaluation and expert analysis that identifies both obvious vulnerabilities and subtle security weaknesses. Security Ninja’s automated assessment provides professional-grade evaluation with actionable results.
Configuration Optimization Recommendations and Implementation
Professional configuration optimization includes security hardening recommendations, best practice implementation, and ongoing configuration management. Security Ninja provides specific configuration guidance tailored to your WordPress installation and business requirements.
Configuration optimization includes security header implementation, file permission optimization, and access control enhancement that strengthens core security posture. Professional optimization ensures maximum protection while maintaining operational functionality and performance.
Real-Time Security Monitoring and Threat Detection
Comprehensive real-time security monitoring includes continuous threat detection, anomaly analysis, and incident alerting that provides immediate security event notification. Professional monitoring services ensure rapid threat identification and response capability.
Security monitoring includes file integrity monitoring, access pattern analysis, and vulnerability detection that identifies security events as they occur. Real-time monitoring provides immediate threat visibility and automated response capability for optimal protection.
WordPress security monitoring requires professional-grade tools and expert analysis that distinguishes between legitimate activity and potential threats. Security Ninja’s monitoring services provide comprehensive coverage and expert incident response support.
4 Plugin and Theme Security Audit
WordPress plugin and theme security audit examines third-party components that extend WordPress functionality while potentially introducing security vulnerabilities. Professional plugin and theme assessment identifies security risks, evaluates code quality, and provides remediation guidance for comprehensive protection.
4.1 Plugin Security Assessment Procedures
Active Plugin Inventory and Security Evaluation
Comprehensive plugin security audit begins with complete inventory of active plugins including version numbers, update status, and security history. Professional plugin evaluation examines each plugin’s security track record, developer reputation, and vulnerability disclosure history.
Plugin security assessment includes functionality analysis, permission evaluation, and data access review that identifies potential security risks. Professional plugin audit examines code quality, security implementation, and update management that affects overall security posture.
Plugin Vulnerability Assessment and Risk Analysis
Professional plugin vulnerability assessment includes comprehensive security testing, code analysis, and vulnerability database cross-reference. Plugin risk analysis evaluates potential impact, exploitation likelihood, and remediation complexity for effective risk management.
Vulnerability assessment includes automated scanning, manual code review, and penetration testing that identifies security weaknesses in plugin implementations. Professional risk analysis provides prioritized remediation guidance based on business impact and threat severity.
Plugin vulnerability management requires continuous monitoring, rapid patch deployment, and alternative solution evaluation when security issues arise. Professional vulnerability assessment ensures comprehensive protection against plugin-based attacks.
Code Quality Review and Security Best Practices Validation
Comprehensive plugin code quality review examines security implementation, coding standards compliance, and best practice adherence. Professional code analysis identifies security vulnerabilities, performance issues, and maintenance concerns that affect long-term security.
Security best practices validation includes input validation assessment, output encoding evaluation, and authentication mechanism review. Professional code review ensures plugin implementations follow WordPress security guidelines and industry standards.
4.2 Theme Security Evaluation
Theme Security Audit and Vulnerability Assessment
Professional WordPress theme security audit includes comprehensive evaluation of theme code, security implementation, and vulnerability assessment. Theme security evaluation examines template files, function implementations, and security controls that protect against common attack vectors.
Theme vulnerability assessment includes automated scanning, manual code review, and security testing that identifies potential security weaknesses. Professional theme audit evaluates both active themes and installed alternatives that may contain security vulnerabilities.
WordPress theme security requires systematic evaluation and ongoing monitoring that ensures template security and protection against theme-based attacks. Theme security assessment provides comprehensive evaluation and remediation guidance.
Custom Code Review and Security Validation
Comprehensive custom code review examines theme modifications, custom functions, and security implementations that extend theme functionality. Professional code validation ensures custom modifications follow security best practices and don’t introduce vulnerabilities.
Custom code security assessment includes input validation review, output encoding evaluation, and authentication mechanism analysis. Professional validation identifies security weaknesses in custom implementations and provides improvement recommendations.
WordPress custom code security requires expert analysis and systematic validation that ensures modifications maintain security standards. Professional custom code review provides detailed security assessment and optimization guidance.
Template Security and Data Handling Evaluation
Professional template security evaluation examines data handling procedures, user input processing, and output generation that affects security posture. Template security assessment includes XSS prevention, SQL injection protection, and data validation implementation.
WordPress template security requires comprehensive evaluation and expert analysis that identifies potential vulnerabilities in data handling and user interaction. Professional template security assessment provides detailed evaluation and improvement guidance.
4.3 Security Ninja Plugin and Theme Analysis
WP Security Ninja provides comprehensive plugin and theme security analysis that combines automated scanning with expert code review. Our professional analysis services identify vulnerabilities and provide actionable remediation guidance for optimal protection.
Automated Plugin and Theme Vulnerability Scanning
Security Ninja’s automated vulnerability scanning includes comprehensive evaluation of all installed plugins and themes against current vulnerability databases. Automated scanning provides immediate risk identification and prioritization that guides remediation efforts.
Professional vulnerability scanning includes code analysis, configuration assessment, and security testing that identifies both known vulnerabilities and potential security weaknesses. Automated tools provide detailed reporting and remediation guidance for efficient security improvement.
Plugin and theme vulnerability scanning requires comprehensive coverage and expert analysis that identifies security risks across all third-party components. Security Ninja’s scanning capabilities provide professional-grade assessment with actionable results.
Code Analysis and Security Flaw Detection
Comprehensive code analysis includes static analysis, dynamic testing, and security flaw detection that identifies vulnerabilities in plugin and theme implementations. Professional code analysis examines security controls, input validation, and output encoding that affects security posture.
Security flaw detection includes automated analysis and manual review that identifies both obvious vulnerabilities and subtle security weaknesses. Professional code analysis provides detailed vulnerability assessment and remediation guidance.
Compatibility Assessment and Conflict Resolution
Professional compatibility assessment examines plugin and theme interactions, conflict identification, and resolution procedures. Compatibility evaluation ensures security implementations don’t interfere with functionality while maintaining protection effectiveness.
Conflict resolution includes compatibility testing, configuration optimization, and alternative solution evaluation that maintains both security and functionality. Professional compatibility assessment ensures optimal protection without operational disruption.
WordPress compatibility management requires systematic evaluation and expert guidance that balances security with functionality requirements. Security Ninja’s compatibility services provide professional assessment and optimization support.
5 Infrastructure and Hosting Security Audit
WordPress infrastructure and hosting security audit examines the underlying server environment, hosting configuration, and infrastructure security that supports your WordPress installation. Professional infrastructure assessment identifies vulnerabilities in hosting setup, server configuration, and network security that affect overall protection.
5.1 Hosting Environment Assessment
Server Security Configuration and Hardening Evaluation
Comprehensive hosting security audit includes server configuration review, security hardening assessment, and infrastructure protection evaluation. Professional server assessment examines operating system security, service configuration, and access controls that protect the hosting environment.
Server security evaluation includes patch management assessment, service hardening review, and network security configuration that ensures comprehensive infrastructure protection. Professional hosting assessment identifies configuration weaknesses and provides specific hardening recommendations.
Network Security and firewall Configuration Review
Professional network security assessment examines firewall configuration, network segmentation, and traffic filtering that protects WordPress installations. Network security evaluation includes intrusion detection, DDoS protection, and traffic analysis that identifies potential security threats.
Firewall configuration review includes rule assessment, policy evaluation, and protection effectiveness analysis that ensures comprehensive network security. Professional network assessment identifies configuration gaps and provides optimization recommendations.
SSL/TLS Implementation and Encryption Assessment
Comprehensive SSL/TLS assessment includes certificate validation, encryption strength evaluation, and implementation security review. Professional encryption assessment examines certificate management, protocol configuration, and security header implementation that ensures secure communications.
Encryption evaluation includes cipher suite assessment, protocol version review, and certificate chain validation that ensures optimal encryption security. Professional SSL/TLS assessment identifies configuration weaknesses and provides improvement recommendations.
5.2 File and Database Security Analysis
File Permission and Access Control Review
Professional file security assessment examines file permissions, directory access controls, and file system security that protects WordPress files and data. File permission review includes ownership verification, access restriction evaluation, and permission optimization that prevents unauthorized access.
Access control evaluation includes directory protection, file access monitoring, and permission inheritance assessment that ensures appropriate security boundaries. Professional file security assessment identifies permission weaknesses and provides optimization guidance.
WordPress file security requires systematic permission management, regular access review, and comprehensive monitoring that protects against file-based attacks. File security assessment ensures optimal protection and access control implementation.
Database Security Configuration and Encryption Assessment
Comprehensive database security assessment includes access control review, encryption evaluation, and configuration security analysis. Professional database assessment examines user permissions, connection security, and data protection that ensures database security.
Database encryption assessment includes data-at-rest encryption, connection encryption, and backup encryption that protects sensitive information. Professional database security evaluation identifies configuration weaknesses and provides improvement recommendations.
Sensitive Data Protection and Privacy Compliance
Professional sensitive data assessment examines data handling procedures, privacy protection implementation, and compliance requirement adherence. Data protection evaluation includes personal information handling, data retention policies, and privacy control implementation.
Privacy compliance assessment includes GDPR compliance evaluation, data processing assessment, and consent management review that ensures regulatory adherence. Professional privacy assessment identifies compliance gaps and provides improvement guidance.
WordPress privacy protection requires comprehensive data handling procedures, privacy control implementation, and ongoing compliance monitoring. Privacy assessment ensures optimal data protection and regulatory compliance.
5.3 Security Ninja Infrastructure Assessment
WP Security Ninja provides comprehensive infrastructure security assessment that examines hosting environment, server configuration, and network security. Our professional infrastructure services identify vulnerabilities and provide optimization recommendations for comprehensive protection.
Hosting Security Evaluation and Optimization Recommendations
Security Ninja’s hosting security evaluation includes comprehensive assessment of server configuration, hosting provider security, and infrastructure protection. Professional hosting assessment provides detailed analysis and optimization recommendations tailored to your hosting environment.
Hosting optimization includes security configuration improvement, performance enhancement, and protection strengthening that ensures optimal hosting security. Professional hosting services provide ongoing monitoring and management support for sustained protection.
Server Configuration Analysis and Hardening Guidance
Comprehensive server configuration analysis includes security setting review, hardening assessment, and optimization guidance. Professional server analysis examines operating system security, service configuration, and access controls that protect the hosting environment.
Server hardening guidance includes specific configuration recommendations, security implementation procedures, and ongoing maintenance requirements. Professional hardening services ensure optimal server security while maintaining operational functionality.
Professional Infrastructure Security Consultation
Professional infrastructure consultation includes security architecture review, optimization planning, and implementation guidance. Security Ninja’s infrastructure experts provide specialized knowledge and recommendations for complex hosting environments and enterprise requirements.
Infrastructure consultation includes security strategy development, technology selection guidance, and implementation planning that ensures optimal protection. Professional consultation services provide ongoing support and expert guidance for infrastructure security management.
WordPress infrastructure security requires expert consultation and professional guidance that addresses complex security requirements and business constraints. Security Ninja’s consultation services provide comprehensive support and specialized expertise.
6 Security Audit Tools and Automation
WordPress security audit tools and automation capabilities enhance assessment efficiency while ensuring comprehensive coverage and consistent results. Professional audit tools combine automated scanning with manual testing capabilities that provide thorough security evaluation and expert analysis.
6.1 Automated Security Scanning Tools
Vulnerability Scanners and Security Assessment Tools
Comprehensive WordPress security audit requires professional vulnerability scanners that identify security weaknesses across WordPress core, plugins, themes, and hosting infrastructure. Professional scanning tools include database integration, threat intelligence, and expert analysis that provides actionable security insights.
Automated vulnerability assessment includes comprehensive scanning capabilities, false positive reduction, and prioritized reporting that optimizes remediation efforts. Professional scanning tools provide detailed vulnerability analysis and remediation guidance for efficient security improvement.
Configuration Analysis and Compliance Checking Tools
Professional configuration analysis tools examine WordPress security settings, hosting configuration, and compliance requirements. Configuration assessment includes security hardening evaluation, best practice validation, and compliance verification that ensures comprehensive protection.
Compliance checking tools include regulatory requirement assessment, policy validation, and documentation generation that supports audit requirements and regulatory reporting. Professional compliance tools provide systematic evaluation and detailed reporting for compliance management.
WordPress configuration security requires systematic analysis and expert evaluation that ensures optimal security settings and compliance adherence. Professional configuration tools provide comprehensive assessment and optimization guidance.
Penetration Testing Tools and Security Validation
Comprehensive penetration testing includes manual testing tools, automated exploitation frameworks, and security validation capabilities. Professional penetration testing tools provide controlled security testing that identifies exploitable vulnerabilities and validates security controls.
Security validation includes authentication testing, authorization bypass evaluation, and data protection assessment that ensures comprehensive security verification. Professional testing tools provide detailed analysis and remediation guidance for security improvement.
6.2 Manual Security Testing Procedures
Manual Penetration Testing and Security Validation
Professional manual penetration testing includes systematic security evaluation, vulnerability exploitation, and security control validation. Manual testing procedures examine authentication mechanisms, authorization controls, and data protection that automated tools may miss.
Security validation includes business logic testing, workflow security assessment, and user interaction security that requires human analysis and expert evaluation. Professional manual testing provides comprehensive security assessment and detailed vulnerability analysis.
WordPress manual testing requires expert knowledge and systematic procedures that identify complex security vulnerabilities and configuration weaknesses. Manual testing provides comprehensive evaluation and professional security analysis.
Code Review and Security Analysis Procedures
Comprehensive code review includes manual analysis, security flaw identification, and best practice validation. Professional code analysis examines security implementations, input validation, and output encoding that affects security posture.
WordPress code security requires expert analysis and systematic review that ensures secure implementations and protection against common vulnerabilities. Professional code review provides comprehensive evaluation and optimization guidance.
Social Engineering and Human Factor Assessment
Professional social engineering assessment examines human factors, security awareness, and procedural security that affects overall protection. Human factor evaluation includes security training assessment, policy compliance, and security culture evaluation.
Social engineering testing includes phishing simulation, security awareness evaluation, and procedural security assessment that identifies human-related security risks. Professional human factor assessment provides comprehensive evaluation and improvement recommendations.
WordPress security requires comprehensive protection that addresses both technical vulnerabilities and human factors. Professional social engineering assessment ensures complete security evaluation and awareness improvement.
6.3 Security Ninja Audit Tool Integration
WP Security Ninja provides comprehensive audit tool integration that combines automated scanning with professional analysis and expert consultation. Our integrated audit platform provides complete security assessment capabilities with professional-grade tools and expert guidance.
Comprehensive Automated Security Scanning and Assessment
Security Ninja’s integrated scanning platform includes comprehensive vulnerability assessment, configuration analysis, and compliance evaluation. Automated scanning provides immediate risk identification and prioritization that guides remediation efforts with professional accuracy.
WordPress security scanning requires comprehensive coverage and professional analysis that identifies all potential security risks. Security Ninja’s integrated platform provides professional-grade assessment with expert consultation and ongoing support.
Professional-Grade Security Testing and Validation Tools
Comprehensive security testing includes automated tools, manual testing capabilities, and expert validation that provides thorough security assessment. Professional testing tools include penetration testing frameworks, vulnerability exploitation tools, and security validation capabilities.
Security validation tools include authentication testing, authorization assessment, and data protection evaluation that ensures comprehensive security verification. Professional testing provides detailed analysis and expert guidance for security optimization.
WordPress security testing requires professional tools and expert analysis that safely evaluate security controls while providing actionable results. Security Ninja’s testing platform provides comprehensive capabilities with professional support.
Custom Audit Tool Configuration and Optimization
Professional audit tool configuration includes customized scanning parameters, specialized testing procedures, and optimized assessment workflows. Custom configuration ensures audit tools align with specific requirements and provide relevant results.
WordPress audit tool optimization requires expert knowledge and systematic configuration that balances comprehensive coverage with operational efficiency. Security Ninja’s optimization services provide professional configuration and ongoing management support.
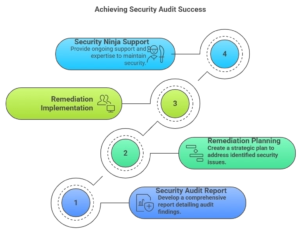
7 Audit Reporting and Remediation
WordPress security audit reporting and remediation provide actionable insights and systematic improvement guidance that transforms audit findings into enhanced security protection. Professional audit reporting includes executive summaries, technical details, and prioritized remediation plans that support effective security improvement.
7.1 Security Audit Report Development
Executive Summary and Business Impact Assessment
Comprehensive security audit reports include executive summaries that communicate security findings, business impact, and remediation priorities to stakeholders and decision-makers. Professional executive reporting translates technical findings into business language that supports informed security investment decisions.
Business impact assessment includes risk quantification, potential loss calculation, and protection value analysis that justifies security improvements and resource allocation. Professional impact analysis provides clear business case for security enhancement and ongoing protection investment.
Technical Findings and Vulnerability Documentation
Professional technical documentation includes detailed vulnerability descriptions, exploitation procedures, and technical analysis that supports remediation planning and implementation. Technical findings provide comprehensive information for security teams and technical implementers.
Vulnerability documentation includes severity assessment, exploitation likelihood, and remediation complexity that guides priority setting and resource allocation. Professional documentation ensures technical teams have complete information for effective remediation implementation.
WordPress vulnerability documentation requires comprehensive technical detail and expert analysis that supports effective remediation and ongoing protection. Professional documentation provides complete information for security improvement and maintenance.
Risk Prioritization and Remediation Recommendations
Comprehensive risk prioritization includes vulnerability severity assessment, business impact analysis, and remediation complexity evaluation that guides improvement efforts. Professional prioritization ensures optimal resource allocation and maximum security improvement.
Remediation recommendations include specific implementation guidance, timeline estimates, and resource requirements that support effective security improvement planning. Professional recommendations provide actionable guidance for systematic security enhancement.
7.2 Remediation Planning and Implementation
Remediation Priority Matrix and Timeline Development
Professional remediation planning includes priority matrix development, timeline creation, and resource allocation that ensures systematic security improvement. Remediation planning considers vulnerability severity, business impact, and implementation complexity for optimal improvement sequencing.
Timeline development includes milestone planning, dependency management, and progress tracking that ensures effective remediation implementation. Professional planning provides realistic timelines and achievable milestones that support successful security improvement.
WordPress remediation planning requires systematic approach and expert guidance that balances security improvement with operational requirements. Professional planning ensures effective implementation and sustained security enhancement.
Resource Allocation and Implementation Planning
Comprehensive implementation planning includes resource identification, skill assessment, and capacity planning that supports effective remediation execution. Professional planning ensures adequate resources and capabilities for successful security improvement implementation.
Implementation planning includes task assignment, progress monitoring, and quality assurance that ensures effective remediation completion. Professional planning provides systematic approach and expert guidance for successful security enhancement.
Validation Testing and Verification Procedures
Professional validation testing includes remediation verification, security testing, and effectiveness assessment that ensures successful security improvement implementation. Validation procedures confirm remediation effectiveness and identify any remaining security concerns.
Verification procedures include testing protocols, acceptance criteria, and documentation requirements that ensure comprehensive validation and quality assurance. Professional verification provides systematic approach and expert analysis for remediation confirmation.
WordPress remediation validation requires comprehensive testing and expert verification that ensures effective security improvement and ongoing protection. Professional validation provides complete assurance and continued security monitoring.
7.3 Security Ninja Audit Reporting and Support
WP Security Ninja provides comprehensive audit reporting and remediation support that transforms security findings into actionable improvements. Our professional reporting services include detailed analysis, prioritized recommendations, and ongoing implementation support.
Professional Audit Reports with Executive Summaries
Security Ninja’s professional audit reports include comprehensive executive summaries, detailed technical findings, and prioritized remediation plans. Professional reporting provides clear communication for both technical teams and business stakeholders with actionable insights and improvement guidance.
Executive reporting includes business impact analysis, risk quantification, and investment justification that supports informed decision-making and resource allocation. Professional summaries translate technical findings into business language that enables effective security planning.
WordPress audit reporting requires professional presentation and expert analysis that communicates security findings effectively to all stakeholders. Security Ninja’s reporting services provide comprehensive documentation and clear communication for successful security improvement.
Detailed Remediation Guidance and Implementation Support
Comprehensive remediation guidance includes specific implementation procedures, configuration instructions, and best practice recommendations. Professional implementation support provides expert assistance and ongoing guidance throughout the remediation process.
Implementation support includes technical consultation, troubleshooting assistance, and progress monitoring that ensures successful security improvement completion. Professional support provides expert knowledge and systematic guidance for effective remediation.
Ongoing Security Monitoring and Compliance Tracking
Professional ongoing monitoring includes continuous security assessment, compliance tracking, and improvement monitoring that ensures sustained security enhancement. Ongoing monitoring provides early threat detection and continuous improvement guidance.
Compliance tracking includes regulatory requirement monitoring, policy adherence assessment, and documentation maintenance that supports ongoing compliance management. Professional tracking ensures sustained compliance and continuous improvement.
WordPress security monitoring requires professional tools and expert analysis that provides continuous protection and ongoing improvement. Security Ninja’s monitoring services provide comprehensive coverage and expert support for sustained security excellence.
8 Conclusion: Professional WordPress Security Audit Excellence
WordPress security audits represent essential investments in digital asset protection, business continuity, and regulatory compliance that safeguard your organization’s most valuable resources. Professional security audit implementation provides systematic vulnerability identification, risk assessment, and remediation guidance that transforms security posture and reduces business risk.
The comprehensive WordPress security audit methodology outlined in this guide provides framework for thorough security assessment that addresses all potential vulnerabilities and attack vectors. From WordPress core security evaluation to infrastructure assessment and compliance validation, systematic audit procedures ensure complete coverage and actionable results.
Key WordPress Security Audit Benefits:
- Comprehensive Vulnerability Identification: Systematic assessment identifies all potential security risks and attack vectors
- Risk-Based Prioritization: Professional analysis provides prioritized remediation guidance for optimal resource allocation
- Compliance Validation: Regulatory requirement assessment ensures adherence to industry standards and legal requirements
- Business Impact Analysis: Professional evaluation quantifies security risks and justifies protection investments
- Expert Remediation Guidance: Detailed implementation procedures and ongoing support ensure effective security improvement
Professional Audit Implementation Success Factors:
- Certified Security Professionals: Expert knowledge and industry certifications ensure comprehensive assessment quality
- Advanced Assessment Tools: Professional-grade scanning and testing tools provide thorough coverage and accurate results
- Systematic Methodology: Structured audit procedures ensure consistent results and complete coverage
- Ongoing Support: Continuous monitoring and improvement guidance ensure sustained security enhancement
Related Professional Security Resources:
- WordPress Security Best Practices Implementation
- Comprehensive WordPress Security Checklist
- Professional WordPress Security Hardening
- WordPress Security Scanner Comparison
- WordPress Login Security Complete Guide
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.