Updated on
In 2024 alone, 7,966 new vulnerabilities were discovered in the WordPress ecosystem, a staggering 34% increase from the previous year. Every day, millions of bots scan WordPress sites looking for outdated plugins, weak passwords, and that one forgotten admin account. When they find something, the consequences are rarely pretty: sites go down, data leaks, customers disappear, and reputations crumble.
The numbers paint a sobering picture. WordPress powers over 40% of all websites on the internet, making it an irresistible target for cybercriminals. Currently, more than 100,000 WordPress sites are at risk from critical vulnerabilities, with 43% of these security flaws exploitable without any authentication required. When a security breach occurs, the average cost reaches $4.45 million, a figure that can devastate businesses of any size.
But here’s the reality that most WordPress site owners don’t grasp: these disasters are almost entirely preventable. The difference between a secure WordPress site and a compromised one isn’t luck, it’s strategy, implementation, and ongoing vigilance.
WordPress security isn’t just about installing a plugin and hoping for the best. It’s about understanding the threat landscape, implementing layered defenses, and maintaining those protections over time. The security challenges facing WordPress sites in 2026 are more sophisticated than ever, with AI-generated malware, zero-day exploits, and supply chain attacks becoming increasingly common.
This comprehensive guide represents years of experience protecting WordPress sites, analyzing security incidents, and developing the Security Ninja plugin that has safeguarded thousands of websites. We’ve distilled everything we’ve learned into a complete roadmap that takes you from basic security awareness to advanced protection strategies.
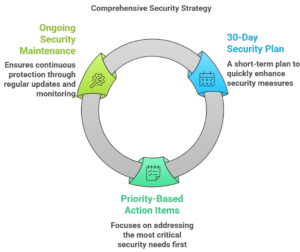
You’ll discover the current threat landscape that’s targeting WordPress sites, learn how to implement a multi-layered security strategy, and get a practical 30-day implementation plan that transforms your site from vulnerable to fortress-strong. Whether you’re managing a personal blog, a business website, or an e-commerce store, this guide provides the knowledge and tools you need to protect what matters most.
The cost of implementing comprehensive WordPress security is measured in hours and modest investment. The cost of ignoring it is measured in lost revenue, damaged reputation, legal liability, and sleepless nights. Let’s ensure you never have to experience the latter.
Contents
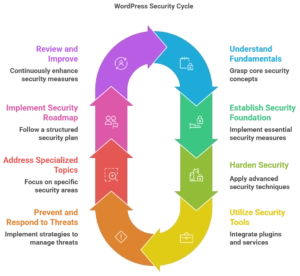
1. WordPress Security Fundamentals
1.1 Why WordPress Security Matters in 2026
The WordPress security landscape has evolved dramatically, and the stakes have never been higher. Understanding why security matters requires looking beyond technical vulnerabilities to the real-world impact on businesses, users, and the broader internet ecosystem.
The Current Threat Landscape:
The statistics surrounding WordPress security in 2026 are both alarming and enlightening. The 7,966 new vulnerabilities discovered in 2024 represent more than just numbers, they represent attack opportunities that cybercriminals actively exploit. These vulnerabilities span across the WordPress ecosystem, with the vast majority found in third-party plugins and themes rather than WordPress core itself.
What makes this particularly concerning is the speed at which these vulnerabilities are weaponized. Security researchers have observed that many vulnerabilities are exploited within hours of public disclosure, sometimes even before patches are available. This creates a narrow window where sites remain vulnerable, emphasizing the critical importance of proactive security measures.
Business Consequences of Security Breaches:
The financial impact of a WordPress security breach extends far beyond the immediate technical costs. When a site goes down due to a security incident, the revenue loss begins immediately. E-commerce sites can lose thousands of dollars per hour of downtime, while service-based businesses face appointment cancellations and customer frustration.
Reputation damage often proves more costly than the immediate financial impact. Customers who encounter a compromised website, whether through malware warnings, defaced pages, or stolen personal information, lose trust that can take years to rebuild. Studies show that 65% of consumers will avoid doing business with a company that has experienced a data breach.
Legal liability represents another significant concern, particularly with regulations like GDPR, CCPA, and industry-specific compliance requirements. A security breach that exposes customer data can result in regulatory fines, legal action, and mandatory breach notifications that further damage reputation.
The recovery costs compound these immediate impacts. Professional malware removal services typically charge between $500-$5,000 depending on the severity of the infection. Lost productivity, emergency hosting changes, and the time required to rebuild trust with customers add additional costs that many businesses underestimate.
The Security Return on Investment:
Implementing comprehensive WordPress security requires investment in time, tools, and potentially professional services. However, this investment pales in comparison to the cost of a security incident. A robust security strategy typically costs a few hundred dollars annually, while recovering from a major breach can cost tens of thousands.
Insurance benefits represent another often-overlooked advantage. Many cyber liability insurance policies offer reduced premiums for businesses that implement comprehensive security measures. Some policies even require specific security controls, making proactive security implementation a necessity rather than an option.
1.2 Understanding WordPress Security Architecture
WordPress security operates across multiple layers, each with its own vulnerabilities and protection mechanisms. Understanding this architecture helps identify where security measures should be implemented and why certain protections are more critical than others.
WordPress Core Security:
WordPress core, the fundamental software that powers WordPress sites, has a strong security track record. The WordPress security team actively monitors for vulnerabilities, releases regular security updates, and maintains a responsible disclosure process for security researchers. Automatic security updates for minor releases help ensure that critical patches are applied quickly.
However, WordPress core security has inherent limitations. The software must balance security with usability, functionality, and backward compatibility. Features like the plugin system, theme customization, and user management create potential attack surfaces that must be managed through proper configuration and additional security measures.
The WordPress user management system provides role-based access control, but many site owners don’t properly configure user permissions. Default installations often grant excessive privileges, and user accounts frequently remain active long after they’re needed. Understanding and properly configuring WordPress user roles forms a critical foundation for site security.
File structure security represents another core consideration. WordPress creates specific directories and files with predetermined purposes, but improper file permissions or unnecessary files can create security vulnerabilities. The wp-config.php file, for example, contains database credentials and security keys that must be protected from unauthorized access.
Plugin and Theme Ecosystem Security:
Third-party plugins and themes represent the primary source of WordPress vulnerabilities. Unlike WordPress core, which benefits from extensive security review and testing, plugins may be developed by individuals or small teams with varying security expertise. Some plugins haven’t been updated in years, while others may contain fundamental security flaws.
The plugin review process for the WordPress repository includes basic security checks, but it cannot catch all potential vulnerabilities. Commercial plugins and themes often receive less scrutiny, and nulled or pirated versions frequently contain malicious code. This creates a complex security landscape where site owners must evaluate not just functionality but also security implications.
Code quality varies significantly across the ecosystem. Well-developed plugins follow WordPress security best practices, sanitize user input, and validate data properly. Others may contain SQL injection vulnerabilities, cross-site scripting flaws, or insecure file handling. Regular updates help address discovered vulnerabilities, but only if site owners apply them promptly.
Hosting Environment Security:
The hosting environment provides the foundation for WordPress security, yet many site owners overlook its importance. Shared hosting environments can create security risks when other sites on the same server are compromised, while dedicated hosting provides more control but requires greater security expertise.
Server security encompasses multiple layers, from the operating system and web server configuration to database security and network protection. PHP version and configuration significantly impact security, with older versions containing known vulnerabilities and insecure default settings. Many hosting providers still run outdated PHP versions, creating unnecessary security risks.
Database security often receives insufficient attention despite storing all site content and user information. Weak database passwords, excessive user privileges, and unencrypted connections can provide attackers with direct access to sensitive information. Regular database backups are essential, but they must be stored securely to prevent unauthorized access.
1.3 Common Security Myths Debunked
WordPress security discussions are often clouded by misconceptions that can lead to poor security decisions. Understanding and debunking these myths helps create a more accurate foundation for security planning.
Myth 1: “WordPress is inherently insecure”
This persistent myth stems from WordPress’s popularity and the resulting attention from security researchers and attackers. The reality is that WordPress core has a strong security record, with most vulnerabilities found in third-party plugins and themes rather than the core software itself.
Security researchers regularly audit WordPress core, and the WordPress security team responds quickly to discovered vulnerabilities. The automatic update system ensures that critical security patches are applied rapidly across millions of sites. When properly configured and maintained, WordPress core provides a secure foundation for website operations.
Myth 2: “Security plugins provide complete protection”
Security plugins are valuable tools, but they’re not magic bullets that provide complete protection. This myth leads to a false sense of security where site owners install a plugin and assume they’re fully protected without implementing other necessary security measures.
Effective WordPress security requires a layered approach that includes proper configuration, regular updates, strong authentication, secure hosting, and ongoing monitoring. Security plugins can automate many of these tasks and provide additional protection layers, but they cannot compensate for fundamental security oversights.
Myth 3: “Small sites aren’t attractive targets”
Many small business owners and personal bloggers believe their sites are too insignificant to attract attackers. This myth is dangerous because it leads to inadequate security measures based on the false assumption that attackers only target high-profile sites.
The reality is that most WordPress attacks are automated and indiscriminate. Bots scan millions of sites looking for vulnerabilities, regardless of the site’s size, content, or perceived value. A small personal blog with an outdated plugin is just as likely to be compromised as a large corporate website with the same vulnerability.
Myth 4: “Updates break websites”
Fear of updates breaking website functionality leads many site owners to postpone or avoid updates entirely. While updates can occasionally cause compatibility issues, the security risks of running outdated software far outweigh the potential for temporary functionality problems.
Modern WordPress, plugin, and theme development practices have significantly reduced update-related issues. Semantic versioning, better testing practices, and staged rollout procedures help minimize the risk of updates causing problems. Most updates, particularly security updates, can be applied safely without any noticeable changes to site functionality.
1.4 Risk Assessment Framework
Effective WordPress security begins with understanding your specific risk profile. Different types of sites face different threats and require different levels of protection. A systematic risk assessment helps prioritize security investments and ensure that protection measures align with actual risks.
Site Classification and Risk Levels:
Personal blogs and informational websites typically face lower risks but still require basic security measures. These sites may not store sensitive user data or process financial transactions, but they can still be compromised and used for malicious purposes. The primary risks include defacement, malware hosting, and use in botnet operations.
Business websites face elevated risks due to their importance to operations and reputation. Downtime directly impacts revenue, and security incidents can damage customer trust and brand reputation. These sites often collect customer information through contact forms or newsletters, creating data protection responsibilities.
E-commerce sites face the highest risk levels due to the sensitive financial and personal information they process. Payment card industry (PCI) compliance requirements mandate specific security measures, and data breaches can result in significant financial and legal consequences. These sites require the most comprehensive security implementations.
Enterprise and high-traffic sites face sophisticated threats including targeted attacks, advanced persistent threats, and nation-state actors. These sites require enterprise-grade security measures, professional security services, and comprehensive incident response capabilities.
Threat Modeling Process:
Effective threat modeling begins with asset identification. What information, functionality, or resources does your site contain that attackers might want to access, steal, or damage? This includes customer data, financial information, proprietary content, administrative access, and server resources.
Threat identification involves understanding who might want to attack your site and why. Common threat actors include automated bots seeking vulnerable sites, cybercriminals looking for financial gain, competitors seeking to damage your business, and disgruntled employees or customers seeking revenge.
Vulnerability assessment examines your current security posture to identify potential weaknesses. This includes technical vulnerabilities like outdated software or weak passwords, as well as procedural vulnerabilities like inadequate backup procedures or poor incident response planning.
Risk prioritization combines threat likelihood with potential impact to determine which risks deserve the most attention and resources. A high-impact, high-likelihood risk like an outdated plugin with known vulnerabilities should receive immediate attention, while a low-impact, low-likelihood risk might be addressed through routine security maintenance.
Security Baseline Establishment:
Every WordPress site should implement minimum security requirements regardless of size or purpose. These baseline measures provide fundamental protection against the most common attacks and create a foundation for additional security measures.
Recommended practices build upon the baseline with additional security layers. These include two-factor authentication, security hardening measures, regular security scans, log monitoring, and user access reviews. These practices provide enhanced protection and help detect security incidents more quickly.
Advanced hardening measures are appropriate for high-risk sites or those with specific compliance requirements. These include server-level security configurations, advanced monitoring systems, incident response procedures, and professional security services. The complexity and cost of these measures should align with the site’s risk profile and business requirements.
2. Essential Security Foundation
Building a secure WordPress site requires establishing a solid foundation of essential security practices. These fundamental measures address the most common attack vectors and provide the baseline protection that every WordPress site needs, regardless of size or purpose.
2.1 WordPress Core, Theme, and Plugin Updates
Software updates represent the single most important security measure for WordPress sites. The vast majority of successful WordPress attacks exploit known vulnerabilities in outdated software, making update management a critical security priority.
WordPress Core Update Strategy:
WordPress core updates fall into two categories: minor updates that include security fixes and bug patches, and major updates that introduce new features and functionality. Minor updates install automatically by default, ensuring that critical security patches are applied quickly across the WordPress ecosystem.
Major updates require manual approval, allowing site owners to test compatibility and prepare for potential changes. However, delaying major updates indefinitely creates security risks as older versions eventually stop receiving security patches. A balanced approach involves testing major updates in a staging environment and applying them within a reasonable timeframe.
The WordPress development team maintains an excellent security track record, with security updates typically released within days of vulnerability discovery. The automatic update system ensures that most sites receive these patches quickly, but site owners should monitor update notifications and verify that automatic updates are functioning properly.
Emergency security updates occasionally require immediate attention, particularly when vulnerabilities are being actively exploited. These updates should be applied as quickly as possible, even if it means bypassing normal testing procedures. The risk of exploitation typically outweighs the risk of update-related issues for critical security patches.
Plugin Update Management:
Plugin updates require more careful management than WordPress core updates due to the varying quality and compatibility of third-party code. However, security updates for plugins should be treated with the same urgency as WordPress core security updates.
Compatibility testing becomes more complex with plugins, as updates may introduce changes that conflict with other plugins or themes. A staging environment allows for safe testing of plugin updates before applying them to production sites. However, security updates should be applied to production sites as quickly as possible after testing confirms compatibility.
Selective update strategies may be appropriate for sites with complex plugin configurations or custom modifications. Critical security updates should always be applied promptly, while feature updates can be evaluated more carefully for compatibility and necessity. However, postponing updates indefinitely creates accumulating security risks.
Theme Update Considerations:
Theme updates present unique challenges because themes often contain custom modifications that can be lost during updates. Child themes provide the best solution for preserving customizations while allowing parent theme updates to be applied safely.
Security vulnerabilities in themes are less common than in plugins, but they do occur and can be just as serious. Themes that include custom functionality, contact forms, or dynamic content generation are more likely to contain security vulnerabilities than simple presentation themes.
Custom theme modifications should be documented and backed up before applying updates. If child themes aren’t used, custom modifications may need to be reapplied after theme updates. This process can be time-consuming, but it’s essential for maintaining both functionality and security.
Update Automation and Management Tools:
Update automation can significantly improve security by ensuring that updates are applied promptly without requiring constant manual attention. However, automation must be balanced with the need for testing and compatibility verification.
WordPress core minor updates install automatically by default, and this setting should generally be left enabled. Major updates can be automated for experienced users with proper backup and staging procedures, but manual approval provides an additional safety check for most sites.
Plugin and theme update automation requires more careful consideration. Security-focused plugins may be good candidates for automatic updates, while complex plugins with frequent updates might be better managed manually. The decision should be based on the plugin’s track record, update frequency, and criticality to site operations.
Third-party update management services can provide additional automation and monitoring capabilities. These services can monitor for updates, test them in staging environments, and apply them according to predefined rules. For sites with multiple installations or complex update requirements, these services can provide significant value.
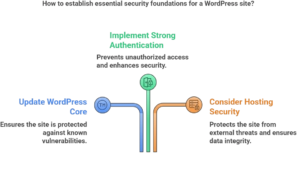
2.2 Strong Authentication and User Management
User authentication represents a critical security boundary that attackers constantly attempt to breach. Strong authentication practices and proper user management significantly reduce the risk of unauthorized access and account compromise.
Password Security Implementation:
Password strength requirements form the foundation of authentication security, but many WordPress sites still rely on weak or default passwords. Implementing and enforcing strong password policies helps prevent brute force attacks and credential stuffing attempts.
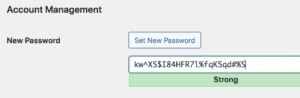
Strong passwords should be long, complex, and unique for each account. The current best practice recommends passwords of at least 12 characters containing a mix of uppercase and lowercase letters, numbers, and special characters. However, length is generally more important than complexity, with longer passwords providing exponentially better protection.
Password generation tools can create truly random passwords that are much stronger than human-generated passwords. WordPress includes a built-in password generator that creates secure passwords, and password managers can generate and store unique passwords for each account. These tools eliminate the temptation to reuse passwords or create predictable variations.
Two-Factor Authentication Implementation:
Two-factor authentication (2FA) provides an additional security layer that significantly reduces the risk of account compromise, even when passwords are stolen or guessed. 2FA requires users to provide two different types of authentication factors: something they know (password) and something they have (phone, app, or hardware token).
Authentication apps like Google Authenticator, Authy, or Microsoft Authenticator provide time-based one-time passwords (TOTP) that change every 30 seconds. These apps work offline and don’t require SMS, making them more secure and reliable than text message-based 2FA. Most WordPress security plugins support TOTP-based 2FA.
Hardware security keys provide the highest level of 2FA security by using cryptographic authentication that’s resistant to phishing and man-in-the-middle attacks. While more expensive and complex to deploy, hardware keys are appropriate for high-value accounts or organizations with strict security requirements.
Backup codes are essential for 2FA implementations, providing a way to regain access if the primary 2FA device is lost or unavailable. These codes should be generated during 2FA setup, stored securely offline, and used only when necessary. Each backup code should be used only once and new codes generated periodically.
User Role Management and Access Control:
WordPress includes a built-in role system that provides different levels of access and capabilities. Proper role assignment ensures that users have the minimum access necessary to perform their functions, reducing the risk of accidental or malicious damage.
The Administrator role provides complete access to all WordPress functions and should be limited to users who truly need full site control. Many sites have too many Administrator accounts, creating unnecessary security risks. Regular audits should identify and downgrade unnecessary Administrator accounts.
Editor, Author, Contributor, and Subscriber roles provide progressively limited access appropriate for different user types. Content creators typically need Editor or Author access, while customers or newsletter subscribers need only Subscriber access. Custom roles can be created for specific needs that don’t fit the default role structure.
User access reviews should be conducted regularly to identify accounts that are no longer needed or have inappropriate access levels. Employees who change roles, contractors who complete projects, and customers who no longer need access should have their accounts deactivated or deleted promptly.
Session Management and Security:
User session security helps prevent unauthorized access even when authentication credentials are compromised. Proper session management includes secure session storage, appropriate timeout settings, and monitoring for suspicious session activity.
Session timeout settings balance security with user convenience. Shorter timeouts provide better security by limiting the window for session hijacking, while longer timeouts reduce the frequency of required logins. The appropriate balance depends on the site’s security requirements and user expectations.
Concurrent session management controls how many simultaneous sessions a user can maintain. Limiting concurrent sessions helps prevent account sharing and reduces the impact of compromised credentials. However, legitimate users may need multiple sessions for different devices or locations.
Forced logout capabilities allow administrators to terminate all sessions for a specific user or all users simultaneously. This feature is valuable when responding to security incidents or when users report potential account compromise. Some security plugins provide automated forced logout based on suspicious activity patterns.
2.3 Hosting Security Considerations
The hosting environment provides the foundation for WordPress security, yet many site owners pay insufficient attention to hosting security features and configurations. Understanding and optimizing hosting security can significantly improve overall site protection.
Hosting Provider Security Evaluation:
Hosting provider security capabilities vary dramatically, from basic shared hosting with minimal security features to enterprise hosting with comprehensive security suites. Evaluating potential hosting providers should include detailed examination of their security offerings and track record.
Infrastructure security includes server hardening, network protection, and physical security measures. Quality hosting providers implement multiple layers of protection including firewalls, intrusion detection systems, and DDoS protection. They should also maintain current server software and apply security patches promptly.
Backup and disaster recovery capabilities are essential hosting security features. Automated backups should be performed regularly and stored in geographically separate locations. Recovery procedures should be tested and documented, with clear recovery time objectives and point objectives.
Support quality becomes critical during security incidents when rapid response can minimize damage. Hosting providers should offer 24/7 support with security expertise and established incident response procedures. Response times and escalation procedures should be clearly defined in service level agreements.
Server Configuration and Hardening:
Server configuration significantly impacts WordPress security, with many security vulnerabilities stemming from insecure server settings rather than WordPress itself. Understanding key server security configurations helps identify potential risks and necessary improvements.
PHP version and configuration directly affect WordPress security and performance. Older PHP versions contain known security vulnerabilities and lack modern security features. The minimum supported PHP version should be used, with regular updates to maintain security. PHP configuration should disable dangerous functions and enable security features.
Web server configuration includes security headers, access controls, and error handling. Security headers like Content Security Policy, X-Frame-Options, and X-XSS-Protection provide additional protection against common attacks. Access controls should restrict access to sensitive files and directories.
Database configuration affects both security and performance. Database servers should be configured with strong authentication, encrypted connections, and minimal privileges for application accounts. Regular database maintenance including optimization and cleanup helps maintain both security and performance.
File system permissions control access to WordPress files and directories. Incorrect permissions can allow unauthorized access to sensitive files or prevent WordPress from functioning properly. The principle of least privilege should guide permission settings, with regular audits to identify and correct permission issues.
SSL/HTTPS Implementation and Management:
SSL/HTTPS encryption has become essential for all websites, not just those handling sensitive information. Search engines favor HTTPS sites, browsers warn users about non-HTTPS sites, and many modern web features require HTTPS to function.
Certificate installation and configuration must be performed correctly to provide security benefits. Common configuration errors include mixed content warnings, incomplete certificate chains, and weak cipher suites. SSL testing tools can identify configuration issues and provide recommendations for improvement.
Certificate management includes monitoring expiration dates, renewing certificates before they expire, and maintaining certificate security. Automated certificate management tools like Let’s Encrypt can simplify this process and reduce the risk of expired certificates causing site outages.
HTTPS enforcement ensures that all site traffic uses encrypted connections. This includes redirecting HTTP requests to HTTPS, updating internal links, and configuring security headers. WordPress settings should be updated to use HTTPS URLs throughout the site.
Database Security and Optimization:
Database security often receives insufficient attention despite the database containing all site content and user information. Proper database security configuration and maintenance are essential for overall site security.
Database authentication should use strong, unique passwords and limit access to necessary accounts only. Default database accounts should be removed or disabled, and application accounts should have minimal privileges necessary for WordPress operation. Regular password updates help maintain authentication security.
Connection security includes encrypting database connections and restricting network access to database servers. Database servers should not be accessible from the public internet, and connections should use SSL/TLS encryption when possible. Firewall rules should limit database access to authorized servers only.
Database maintenance includes regular backups, optimization, and cleanup procedures. Backups should be tested regularly to ensure they can be restored successfully. Database optimization helps maintain performance and can identify potential security issues like unauthorized data modifications.
Database monitoring can detect suspicious activity like unusual query patterns, failed authentication attempts, or unauthorized access attempts. While WordPress doesn’t generate extensive database logs by default, hosting providers or database administrators can implement monitoring to detect potential security incidents.
3. Advanced Security Hardening
Advanced security hardening goes beyond basic security measures to implement sophisticated protection mechanisms that defend against determined attackers and advanced threats. These measures require more technical expertise but provide significantly enhanced security for sites that need maximum protection.
3.1 WordPress Configuration Hardening
WordPress configuration hardening involves modifying default settings and implementing additional security controls that make WordPress installations more resistant to attack. These modifications often involve editing configuration files and implementing server-level controls.
wp-config.php Security Enhancements:
The wp-config.php file contains critical WordPress configuration information including database credentials and security keys. Hardening this file and its contents significantly improves overall site security.
Security keys and salts provide cryptographic randomness for WordPress authentication and should be unique for each installation. Default or weak keys compromise session security and make sites vulnerable to authentication attacks. WordPress provides a service for generating secure keys, and these should be updated periodically.
Debug mode settings should be disabled in production environments to prevent information disclosure. Debug information can reveal sensitive details about the site structure, installed plugins, and potential vulnerabilities. Debug logs should also be disabled or stored in secure locations inaccessible from the web.
File permission settings in wp-config.php should restrict access to the file itself and control WordPress file operations. The configuration file should be readable only by the web server and WordPress, with no public access. Additional constants can control file editing and automatic updates.
Admin Area Protection and Access Control:
The WordPress admin area represents a high-value target for attackers, making additional protection measures essential for security-conscious installations. Multiple layers of protection can significantly reduce the risk of unauthorized admin access.
Custom admin usernames replace the default “admin” username that attackers commonly target in brute force attacks. Unique, non-obvious usernames make brute force attacks more difficult and time-consuming. Existing admin accounts should be renamed rather than creating new accounts to preserve content ownership.
Login URL customization moves the WordPress login page from its default location to a custom URL that’s harder for attackers to find. While this provides security through obscurity rather than true security, it significantly reduces automated attack attempts and can be combined with other protection measures.
IP address restrictions limit admin access to specific IP addresses or ranges, providing strong protection against remote attacks. This approach works well for sites with administrators who access the site from fixed locations, but it can be problematic for users with dynamic IP addresses or those who need access from multiple locations.
Password protection for the admin directory adds an additional authentication layer that must be bypassed before reaching the WordPress login page. This server-level protection is independent of WordPress and can prevent many automated attacks from reaching the WordPress authentication system.
File System Security and Access Controls:
WordPress file system security involves controlling access to files and directories, preventing unauthorized modifications, and protecting sensitive information from disclosure. Proper file system security requires both WordPress configuration changes and server-level controls.
File editing restrictions prevent users from editing theme and plugin files through the WordPress admin interface. While convenient for quick changes, this feature can be exploited by attackers who gain admin access. Disabling file editing forces changes to be made through secure methods like FTP or SSH.
Directory browsing prevention stops web servers from displaying directory contents when no index file is present. This prevents attackers from discovering backup files, configuration files, or other sensitive information that might be stored in web-accessible directories. Server configuration or .htaccess rules can implement this protection.
Sensitive file protection ensures that configuration files, backups, and other sensitive files cannot be accessed directly through web requests. Files like wp-config.php, .htaccess, and backup files should be protected through server configuration or moved outside the web root entirely.
File upload restrictions limit the types of files that can be uploaded through WordPress, preventing attackers from uploading malicious scripts or executables. WordPress includes basic file type restrictions, but additional server-level controls can provide more comprehensive protection.
Database Security Hardening:
Database hardening involves securing the WordPress database through configuration changes, access controls, and monitoring. Since the database contains all site content and user information, database security is critical for overall site protection.
Custom database prefixes obscure the WordPress table structure from attackers who gain database access. While not a strong security measure by itself, custom prefixes make automated attacks more difficult and can slow down manual attacks. Existing sites can change prefixes, but this requires careful planning and testing.
Database user privileges should follow the principle of least privilege, granting only the minimum permissions necessary for WordPress operation. Separate database users can be created for different functions, with read-only users for backup operations and limited-privilege users for specific applications.
Database connection security includes using encrypted connections when possible and restricting network access to database servers. Database servers should not be accessible from the public internet, and connections should use SSL/TLS encryption to prevent eavesdropping and man-in-the-middle attacks.
Regular database maintenance includes optimization, cleanup, and security audits. Unused tables and data should be removed, database performance should be monitored, and access logs should be reviewed for suspicious activity. Automated maintenance scripts can perform routine tasks while alerting administrators to potential issues.
3.2 Server-Level Security Measures
Server-level security measures provide protection at the infrastructure level, defending against attacks before they reach WordPress. These measures require server administration access and technical expertise but provide comprehensive protection against a wide range of threats.
.htaccess Security Rules and Configuration:
Access control rules can restrict access to sensitive files and directories based on IP addresses, user agents, or other criteria. These rules can prevent access to configuration files, backup files, and administrative directories from unauthorized sources. Regular expression patterns allow for flexible and powerful access controls.
File type restrictions prevent execution of potentially dangerous files and block access to sensitive file types. These rules can prevent PHP execution in upload directories, block access to backup files, and restrict access to configuration files. Comprehensive file type rules provide defense against various attack vectors.
Hotlink protection prevents other sites from directly linking to images and other resources, reducing bandwidth usage and preventing content theft. While primarily a resource protection measure, hotlink protection can also prevent some types of attacks that rely on loading resources from compromised sites.
Security header configuration through .htaccess can implement various security controls including Content Security Policy, X-Frame-Options, and X-XSS-Protection. These headers provide browser-level protection against common attacks and can significantly improve site security with minimal performance impact.
PHP Security Configuration and Hardening:
PHP configuration significantly affects WordPress security, with many vulnerabilities stemming from insecure PHP settings rather than WordPress code. Proper PHP hardening can prevent entire classes of attacks and improve overall security posture.
PHP version management involves maintaining current PHP versions and promptly applying security updates. Older PHP versions contain known vulnerabilities and lack modern security features. The PHP release cycle includes regular security updates that should be applied promptly to maintain security.
Dangerous function restrictions disable PHP functions that can be exploited for malicious purposes. Functions like exec(), system(), and eval() can be used to execute arbitrary code and should be disabled unless specifically required. A comprehensive list of dangerous functions should be disabled in production environments.
Error reporting configuration prevents disclosure of sensitive information through PHP error messages. Detailed error messages can reveal file paths, database information, and other sensitive details that assist attackers. Production sites should log errors securely without displaying them to users.
Network Security and Firewall Configuration:
Network security provides the first line of defense against attacks, filtering malicious traffic before it reaches WordPress. Comprehensive network security includes multiple layers of protection and monitoring.
Web Application Firewall (WAF) implementation provides application-layer protection specifically designed for web applications. WAFs can detect and block common attacks including SQL injection, cross-site scripting, and malicious file uploads. Cloud-based WAFs provide protection without requiring server-level configuration.
Network firewall configuration controls traffic at the network level, blocking malicious IP addresses and restricting access to specific ports and services. Firewalls can implement geographic blocking, rate limiting, and reputation-based filtering to reduce attack traffic.
DDoS protection defends against distributed denial of service attacks that attempt to overwhelm sites with traffic. DDoS protection can include traffic filtering, rate limiting, and traffic distribution across multiple servers. Cloud-based DDoS protection services provide comprehensive protection without requiring local infrastructure.
Advanced Authentication and Access Control:
Advanced authentication mechanisms provide stronger security than traditional username and password authentication. These systems are appropriate for high-security environments and sites that handle sensitive information.
Multi-factor authentication (MFA) extends beyond simple two-factor authentication to include multiple authentication factors and methods. Hardware security keys, biometric authentication, and certificate-based authentication provide strong security for high-value accounts.
Single Sign-On (SSO) integration allows WordPress to authenticate users through external identity providers, centralizing authentication management and enabling advanced security features. SSO can integrate with corporate directory services and provide comprehensive audit trails.
Certificate-based authentication uses digital certificates to authenticate users and devices, providing strong cryptographic authentication that’s resistant to many common attacks. While complex to implement, certificate authentication provides excellent security for high-value applications.
3.3 Network Security Implementation
Network security implementation involves deploying and configuring security controls at the network level to protect WordPress installations from various types of attacks. These measures provide broad protection and can prevent attacks from reaching WordPress entirely.
Firewall Configuration and Management:
Firewall configuration forms the foundation of network security, controlling which traffic can reach WordPress installations and from where. Proper firewall configuration can prevent many attacks and reduce the attack surface significantly.
Application-layer firewalls examine HTTP traffic for malicious patterns and can block specific types of attacks including SQL injection, cross-site scripting, and malicious file uploads. These firewalls understand web application protocols and can provide more sophisticated protection than network-layer firewalls.
Network-layer firewalls control traffic based on IP addresses, ports, and protocols. These firewalls can block traffic from known malicious IP addresses, restrict access to administrative ports, and implement geographic blocking. Network firewalls provide broad protection but lack application-specific intelligence.
Firewall rule management involves creating, maintaining, and updating firewall rules to address evolving threats. Rules should be regularly reviewed and updated based on threat intelligence, attack patterns, and site requirements. Automated rule updates can help maintain protection against new threats.
Logging and monitoring capabilities allow administrators to track firewall activity, identify attack patterns, and tune firewall rules for optimal protection. Comprehensive logs should be maintained and regularly analyzed to identify trends and potential security issues.
DDoS Protection and Traffic Management:
Distributed Denial of Service (DDoS) attacks attempt to overwhelm websites with traffic, making them unavailable to legitimate users. DDoS protection involves multiple strategies for detecting and mitigating these attacks.
Traffic analysis and monitoring help identify DDoS attacks by detecting unusual traffic patterns, volume spikes, and suspicious source addresses. Early detection allows for faster response and can minimize the impact of attacks on site availability.
Rate limiting controls how much traffic individual IP addresses or users can generate, preventing single sources from overwhelming the site. Rate limiting can be implemented at various levels including network, web server, and application levels.
Geographic blocking restricts access from specific countries or regions where legitimate traffic is unlikely. While not appropriate for all sites, geographic blocking can significantly reduce attack traffic for sites that serve specific geographic markets.
Content delivery networks (CDNs) can absorb and filter DDoS traffic before it reaches origin servers. CDNs have large-scale infrastructure that can handle massive traffic volumes and sophisticated filtering capabilities to distinguish legitimate traffic from attack traffic.
Intrusion Detection and Prevention:
Intrusion detection and prevention systems monitor for malicious activity and can automatically respond to detected threats. These systems provide real-time protection and can adapt to new attack patterns.
Signature-based detection identifies known attack patterns using predefined signatures or rules. This approach is effective against known attacks but may miss new or modified attack techniques. Signature databases must be regularly updated to maintain effectiveness.
Anomaly-based detection identifies unusual behavior that might indicate attacks, even if the specific attack pattern isn’t known. This approach can detect new attacks but may generate false positives from legitimate but unusual activity.
Behavioral analysis examines user and system behavior over time to identify patterns that might indicate compromise or malicious activity. This approach can detect sophisticated attacks that avoid triggering other detection methods.
Automated response capabilities allow intrusion prevention systems to automatically block detected threats, reducing response time and minimizing damage. Response actions can include blocking IP addresses, terminating connections, or alerting administrators.
4. Security Plugins and Tools
WordPress security plugins provide automated protection, monitoring, and response capabilities that would be difficult or impossible to implement manually. However, not all security plugins are created equal, and choosing the right tools requires understanding their capabilities, limitations, and how they fit into a comprehensive security strategy.
4.1 Security Plugin Evaluation Criteria
Selecting the right security plugin requires careful evaluation of features, performance impact, compatibility, and vendor reliability. The wrong choice can provide a false sense of security while potentially creating new vulnerabilities or performance problems.
Core Security Feature Assessment:
Malware detection capabilities vary significantly between security plugins, with some providing basic signature-based scanning while others implement advanced behavioral analysis and machine learning detection. The most effective plugins combine multiple detection methods to identify both known and unknown threats.
Firewall functionality ranges from basic IP blocking to sophisticated application-layer filtering that can detect and prevent complex attacks. Web Application Firewalls (WAF) examine HTTP requests for malicious patterns and can block attacks before they reach WordPress code. The quality and comprehensiveness of firewall rules significantly impact protection effectiveness.
Vulnerability scanning identifies known security issues in WordPress core, plugins, and themes. The best security plugins maintain current vulnerability databases and can detect issues quickly after disclosure. Some plugins also provide guidance on remediation steps and can automatically apply certain fixes.
Login protection features include brute force protection, two-factor authentication, and login monitoring. These features help prevent unauthorized access and can detect suspicious login activity. The sophistication of these protections varies significantly between plugins.
Performance Impact Analysis:
Security plugins inevitably impact site performance, but the extent varies dramatically based on implementation quality and feature set. Understanding performance implications helps balance security benefits with user experience requirements.
Resource usage includes CPU consumption, memory usage, and database queries generated by security plugins. Poorly optimized plugins can significantly slow site loading times and increase server resource requirements. Performance testing should be conducted before and after plugin installation to measure impact.
Caching compatibility affects how security plugins interact with caching systems that improve site performance. Some security plugins conflict with caching plugins or CDN services, while others are designed to work seamlessly with performance optimization tools. Compatibility testing is essential for sites that rely on caching for performance.
Database impact includes the number and complexity of database queries generated by security plugins. Plugins that perform extensive logging or real-time scanning can create significant database load. Regular database maintenance may be required to manage the data generated by security plugins.
Background processing for tasks like malware scanning and log analysis can impact server performance if not properly managed. The best security plugins perform intensive tasks during low-traffic periods or provide options to control when resource-intensive operations occur.
Vendor Evaluation and Support Quality:
The security plugin vendor’s reputation, track record, and support quality are crucial factors that affect both security effectiveness and long-term viability. A plugin is only as good as the team maintaining it.
Company reputation includes the vendor’s history in WordPress security, their response to security issues in their own products, and their standing in the WordPress community. Established vendors with strong reputations are more likely to provide reliable, long-term support.
Update frequency and responsiveness to new threats indicate how actively the plugin is maintained. Security plugins must be updated regularly to address new threats and vulnerabilities. Vendors should respond quickly to critical security issues and provide clear communication about updates.
Support quality becomes critical when security incidents occur or when configuration assistance is needed. Premium plugins typically offer better support than free alternatives, but support quality varies significantly even among paid products. Response times, expertise level, and availability should all be evaluated.
Documentation quality affects how effectively the plugin can be configured and used. Comprehensive documentation should cover installation, configuration, troubleshooting, and best practices. Poor documentation can lead to misconfigurations that reduce security effectiveness.
4.2 Security Ninja Plugin Deep Dive
Security Ninja represents a comprehensive approach to WordPress security, combining multiple protection layers with user-friendly management and professional-grade features. Understanding its capabilities helps illustrate what to look for in a security plugin and how to maximize protection effectiveness.
Core Security Features and Capabilities:
Vulnerability scanning in Security Ninja goes beyond basic checks to provide comprehensive analysis of WordPress installations. The plugin examines WordPress core, all installed plugins and themes, and server configuration to identify potential security issues. Scans include checks for known vulnerabilities, configuration weaknesses, and security best practices.
The scanning engine uses multiple detection methods including signature-based detection for known issues, heuristic analysis for suspicious patterns, and configuration analysis for security weaknesses. This multi-layered approach provides comprehensive coverage that can identify both obvious and subtle security problems.
Firewall protection includes both network-level and application-level filtering to block malicious traffic before it reaches WordPress. The firewall can block known malicious IP addresses, detect and prevent common attacks, and provide rate limiting to prevent brute force attacks.
Advanced Protection Mechanisms:
Real-time monitoring provides continuous surveillance of site activity, detecting suspicious behavior as it occurs. This includes monitoring for unauthorized file changes, unusual database activity, and suspicious user behavior. Real-time alerts allow for immediate response to potential security incidents.
Automated response capabilities can take immediate action when threats are detected, including blocking malicious IP addresses, quarantining infected files, and alerting administrators. These automated responses help minimize damage from attacks and reduce the time between detection and response.
Security hardening features can automatically implement many of the advanced security measures discussed in this guide. This includes file permission corrections, security header implementation, and configuration hardening. Automated hardening reduces the technical expertise required to implement advanced security measures.
Detailed reporting provides comprehensive information about security status, detected threats, and recommended actions. Reports can be customized for different audiences, from technical details for administrators to executive summaries for management. Regular reporting helps maintain security awareness and demonstrates security program effectiveness.
Integration and Compatibility:
WordPress ecosystem integration ensures that Security Ninja works seamlessly with other WordPress plugins and themes. Compatibility testing covers popular plugins, themes, and hosting environments to minimize conflicts and ensure reliable operation.
Performance optimization ensures that comprehensive security monitoring doesn’t significantly impact site performance. Efficient code, optimized database queries, and intelligent caching help maintain fast loading times while providing thorough protection.
Hosting platform compatibility covers various hosting environments from shared hosting to enterprise-grade dedicated servers. The plugin adapts to different server configurations and hosting limitations while providing maximum protection within available resources.
Developer-friendly features include hooks, filters, and APIs that allow customization and integration with other tools. This flexibility enables advanced users to tailor security configurations to specific requirements and integrate with existing security workflows.
4.3 Complementary Security Tools and Services
While comprehensive security plugins provide broad protection, additional tools and services can enhance security further and provide specialized capabilities that general-purpose plugins may not offer.
Backup and Recovery Solutions:
Automated backup systems provide essential protection against data loss from security incidents, hardware failures, or human error. Regular, reliable backups enable quick recovery from various types of disasters and should be considered a critical security component.
Backup frequency should balance data protection with storage requirements and performance impact. Daily backups are appropriate for most sites, while high-activity sites may require more frequent backups. Critical sites may need real-time or near-real-time backup solutions.
Storage location security is crucial for backup effectiveness. Backups stored on the same server as the website provide no protection against server compromise or hardware failure. Off-site backup storage, preferably in multiple geographic locations, provides better protection against various disaster scenarios.
Recovery testing ensures that backups can actually be restored when needed. Regular recovery tests should be performed to verify backup integrity and practice recovery procedures. Many backup failures are discovered only when recovery is attempted during an actual emergency.
Monitoring and Alerting Services:
Uptime monitoring detects when sites become unavailable and can distinguish between security incidents and other types of outages. Early detection of availability issues enables faster response and can minimize the impact of security incidents on business operations.
Performance monitoring tracks site speed and responsiveness, which can be affected by security incidents like DDoS attacks or malware infections. Performance degradation may be the first sign of security problems and can help identify issues before they become critical.
Security monitoring services provide specialized threat detection and analysis that goes beyond what individual security plugins can offer. These services may include threat intelligence, behavioral analysis, and expert analysis of security events.
Alert configuration should balance timely notification with alert fatigue. Critical security events require immediate notification, while less urgent issues can be batched into regular reports. Alert thresholds should be tuned to minimize false positives while ensuring that real issues are detected promptly.
SSL Certificate Management and Monitoring:
SSL certificate monitoring ensures that certificates remain valid and properly configured. Certificate expiration can cause site outages and security warnings, while configuration problems can reduce security effectiveness.
Automated certificate renewal services like Let’s Encrypt can eliminate the risk of certificate expiration by automatically renewing certificates before they expire. These services require proper configuration and monitoring to ensure they function correctly.
Certificate security monitoring checks for weak encryption, improper configuration, and security vulnerabilities in SSL implementations. Regular SSL testing helps identify configuration problems that could compromise security.
4.4 Tool Integration and Security Architecture
Effective WordPress security requires integrating multiple tools and services into a cohesive security architecture. Proper integration maximizes protection while minimizing conflicts and performance impact.
Layered Security Implementation:
Defense in depth involves implementing multiple security layers that provide overlapping protection. If one layer fails or is bypassed, other layers continue to provide protection. This approach significantly improves overall security resilience.
Tool coordination ensures that multiple security tools work together effectively without conflicts or gaps in coverage. Some security functions may be duplicated across tools, while others may have gaps that need to be addressed through additional measures.
Performance optimization becomes more challenging with multiple security tools, as each tool adds overhead. Careful selection and configuration of security tools can minimize performance impact while maximizing protection effectiveness.
Cost management involves balancing security tool costs with protection benefits. Premium security tools may provide better protection but at higher cost. The security budget should be allocated based on risk assessment and protection requirements.
Workflow Integration and Automation:
Development workflow integration ensures that security measures don’t interfere with site development and maintenance activities. Security tools should accommodate development workflows while maintaining protection during updates and changes.
Deployment pipeline security includes automated security checks during the deployment process. This can include vulnerability scanning, malware detection, and configuration validation before changes go live.
Maintenance automation can reduce the ongoing effort required to maintain security tools and configurations. Automated updates, scanning, and reporting help ensure that security measures remain effective without constant manual attention.
Emergency response procedures should be integrated with security tools to enable rapid response to security incidents. This includes automated alerting, incident escalation, and response coordination across multiple tools and team members.
5. Threat Prevention and Response
Effective WordPress security requires both preventing threats from succeeding and responding appropriately when prevention measures are bypassed. A comprehensive threat prevention and response strategy addresses the full spectrum of potential security incidents.
5.1 Malware Prevention Strategies
Malware prevention involves implementing multiple layers of protection to prevent malicious code from being installed, executed, or spread through WordPress installations. Prevention is always preferable to cleanup, as malware can cause significant damage before it’s detected and removed.
Input Validation and Sanitization:
Input validation represents the first line of defense against many types of malware and attacks. All data entering WordPress through forms, URLs, cookies, and other sources should be validated and sanitized to prevent malicious code injection.
Data sanitization removes or neutralizes potentially dangerous content from user input. This includes stripping HTML tags, escaping special characters, and validating data formats. WordPress provides built-in sanitization functions that should be used consistently throughout themes and plugins.
Output encoding prevents malicious content from being executed when displayed to users. Even if malicious content bypasses input validation, proper output encoding can prevent it from causing harm. Context-appropriate encoding should be used based on where data is being displayed.
File upload security requires special attention as uploaded files can contain malware or malicious scripts. File type restrictions, content validation, and execution prevention in upload directories help prevent malware distribution through file uploads.
Code Review and Security Testing:
Regular code review helps identify security vulnerabilities before they can be exploited. This includes reviewing custom theme and plugin code, as well as evaluating third-party code before installation.
Static code analysis tools can automatically identify common security vulnerabilities in PHP code. These tools can detect issues like SQL injection vulnerabilities, cross-site scripting flaws, and insecure file handling. While not perfect, static analysis provides valuable security insights.
Dynamic security testing involves testing running WordPress installations for vulnerabilities. This includes penetration testing, vulnerability scanning, and security assessments that identify real-world security issues.
Dependency management involves tracking and updating all software dependencies including WordPress core, plugins, themes, and server software. Vulnerable dependencies are a common source of security issues and should be updated promptly when security patches are available.
Behavioral Analysis and Anomaly Detection:
Behavioral analysis monitors system and user behavior to identify patterns that might indicate malware infection or malicious activity. This approach can detect threats that bypass signature-based detection methods.
File system monitoring tracks changes to WordPress files and can detect unauthorized modifications that might indicate malware installation. Real-time monitoring provides immediate alerts when critical files are changed unexpectedly.
Database activity monitoring can detect unusual database queries or modifications that might indicate malware activity or data theft attempts. Monitoring should focus on sensitive tables and unusual query patterns.
Network traffic analysis can identify malicious communication between infected sites and command and control servers. This includes monitoring for unusual outbound connections, data exfiltration attempts, and botnet communication.
User behavior analysis can detect compromised user accounts by identifying unusual login patterns, activity from unexpected locations, or actions that don’t match normal user behavior patterns.
5.2 Vulnerability Management
Vulnerability management involves identifying, assessing, and addressing security vulnerabilities before they can be exploited by attackers. A systematic approach to vulnerability management significantly reduces security risk.
Vulnerability Identification and Assessment
Automated vulnerability scanning should be performed regularly to identify known security issues in WordPress installations. Scanners should check WordPress core, all plugins and themes, and server configuration for known vulnerabilities.
Manual security assessments provide deeper analysis than automated scanning and can identify complex vulnerabilities that automated tools might miss. Professional security assessments should be conducted periodically, especially for high-value sites.
Threat intelligence feeds provide information about new vulnerabilities and active threats. Subscribing to security advisories and threat intelligence services helps ensure awareness of new risks as they emerge.
Risk Assessment and Prioritization:
CVSS scoring provides a standardized method for assessing vulnerability severity based on factors like exploitability, impact, and complexity. CVSS scores help prioritize remediation efforts and resource allocation.
Exploitability assessment considers how easily vulnerabilities can be exploited in real-world conditions. Some high-severity vulnerabilities may be difficult to exploit, while others with lower CVSS scores might be easily exploitable.
Business impact analysis evaluates how vulnerability exploitation would affect business operations. Vulnerabilities that could impact revenue, customer data, or regulatory compliance should receive higher priority regardless of technical severity.
Environmental factors affect vulnerability risk and should be considered in prioritization decisions. Vulnerabilities in internet-facing systems pose higher risk than those in internal systems, and vulnerabilities in critical systems require faster remediation.
Patch Management and Remediation:
Emergency patch procedures should be established for critical vulnerabilities that are being actively exploited. These procedures may bypass normal testing requirements to apply patches quickly when immediate protection is needed.
Scheduled maintenance windows provide opportunities to apply non-critical patches and updates in a controlled manner. Regular maintenance schedules help ensure that patches are applied consistently without disrupting business operations.
Testing procedures should validate that patches don’t introduce new problems or break existing functionality. Staging environments allow for safe testing of patches before they’re applied to production systems.
Rollback procedures provide a way to quickly reverse patches that cause problems. Having tested rollback procedures reduces the risk of applying patches and enables faster recovery if issues occur.
5.3 Incident Response Planning
Incident response planning prepares organizations to respond effectively when security incidents occur. A well-designed incident response plan minimizes damage, reduces recovery time, and helps prevent similar incidents in the future.
Incident Response Team and Roles:
Response team structure should clearly define roles and responsibilities for different types of security incidents. Team members should understand their specific duties and have the authority to take necessary actions during incidents.
Incident commander role involves coordinating the overall response effort, making critical decisions, and communicating with stakeholders. The incident commander should have sufficient authority and experience to manage complex security incidents effectively.
Technical response team members handle the technical aspects of incident response including analysis, containment, and recovery. These team members should have deep technical knowledge of WordPress, server administration, and security tools.
Communication coordinator manages internal and external communication during incidents. This includes notifying stakeholders, coordinating with law enforcement if necessary, and managing public relations aspects of security incidents.
Incident Detection and Classification:
Detection mechanisms should provide early warning of security incidents through automated monitoring, user reports, and external notifications. Multiple detection methods help ensure that incidents are identified quickly regardless of their nature.
Classification systems help determine the appropriate response level and resources for different types of incidents. Classification should consider factors like affected systems, data involved, and potential business impact.
Escalation procedures ensure that serious incidents receive appropriate attention and resources. Clear escalation criteria and procedures help avoid delays in responding to critical incidents.
Documentation requirements should be established for all security incidents to support analysis, legal requirements, and future prevention efforts. Consistent documentation helps identify trends and improve response procedures.
Response Procedures and Recovery:
Containment strategies focus on preventing incident spread and minimizing damage. This may include isolating affected systems, blocking malicious traffic, or disabling compromised accounts. Containment should be implemented quickly while preserving evidence for analysis.
Evidence preservation is important for incident analysis, legal proceedings, and insurance claims. Digital forensics procedures should be followed to ensure that evidence remains admissible and useful for investigation purposes.
Recovery procedures restore normal operations while ensuring that the underlying security issues have been addressed. Recovery should include verification that systems are clean and secure before returning them to production use.
Post-incident analysis examines what happened, why it happened, and how similar incidents can be prevented in the future. Lessons learned should be incorporated into security procedures and incident response plans.
5.4 Security Monitoring and Alerting
Continuous security monitoring provides early warning of security incidents and helps maintain awareness of the overall security posture. Effective monitoring balances comprehensive coverage with manageable alert volumes.
Real-Time Monitoring Systems:
Log analysis involves examining server logs, application logs, and security tool logs for signs of malicious activity. Automated log analysis can identify patterns and anomalies that might indicate security incidents.
Network monitoring tracks traffic patterns and can detect unusual activity that might indicate attacks or compromised systems. This includes monitoring for data exfiltration, command and control communication, and attack traffic.
File integrity monitoring detects unauthorized changes to critical files and can provide early warning of malware installation or system compromise. Real-time monitoring provides immediate alerts when important files are modified.
User activity monitoring tracks user behavior and can detect compromised accounts or insider threats. This includes monitoring login patterns, access to sensitive data, and unusual user activities.
Alert Configuration and Management:
Alert thresholds should be configured to balance timely notification with alert fatigue. Thresholds that are too sensitive generate excessive false positives, while thresholds that are too high may miss important incidents.
Alert prioritization helps ensure that critical incidents receive immediate attention while less urgent issues are handled appropriately. Priority levels should be based on potential impact and urgency of response required.
Notification methods should ensure that alerts reach the appropriate people quickly and reliably. Multiple notification methods may be necessary to ensure that critical alerts are received even if primary methods fail.
Alert correlation combines related alerts to provide a clearer picture of security incidents and reduce alert volume. Correlation rules should be designed to identify attack patterns and reduce false positives.
6. Specialized Security Topics
WordPress security requirements vary significantly based on the specific use case, regulatory environment, and business context. Understanding specialized security considerations helps implement appropriate protection measures for different scenarios.
6.1 WooCommerce and E-commerce Security
E-commerce sites face unique security challenges due to the sensitive financial and personal information they process. Payment card industry (PCI) compliance requirements, fraud prevention, and customer data protection create additional security obligations beyond basic WordPress security.
Payment Security and PCI Compliance
PCI DSS compliance is mandatory for any organization that processes, stores, or transmits payment card information. Compliance requirements include network security, data protection, vulnerability management, access controls, monitoring, and information security policies.
Payment processing security involves protecting cardholder data throughout the transaction process. This includes encrypting data transmission, securing data storage, and implementing proper access controls. Many e-commerce sites use payment processors to reduce PCI compliance scope.
Tokenization replaces sensitive payment data with non-sensitive tokens that can be safely stored and processed. This approach significantly reduces PCI compliance scope and security risks by eliminating the need to store actual payment card data.
Customer Data Protection:
Data encryption should protect customer information both in transit and at rest. This includes personal information, payment data, and order history. Encryption keys must be properly managed and protected to maintain data security.
Access controls limit who can view and modify customer data based on job responsibilities and business needs. Role-based access control ensures that employees only have access to the customer data they need to perform their duties.
Data retention policies define how long customer data is stored and when it should be securely deleted. Retaining data longer than necessary increases security risks and may violate privacy regulations.
Privacy compliance includes regulations like GDPR, CCPA, and other regional privacy laws. These regulations impose requirements for data collection consent, data portability, deletion rights, and breach notification.
E-commerce Specific Threats:
Card skimming attacks inject malicious code into payment forms to steal credit card information as customers enter it. These attacks can be difficult to detect and may persist for long periods before discovery.
Account takeover attacks target customer accounts to make fraudulent purchases or steal stored payment information. Strong authentication and account monitoring help prevent these attacks.
Inventory manipulation attacks attempt to modify product prices, quantities, or other information to enable fraudulent purchases. Proper access controls and transaction validation help prevent these attacks.
6.2 Multi-site Security Management
WordPress multi-site installations present unique security challenges and opportunities. Centralized management can improve security consistency, but network-wide vulnerabilities can affect multiple sites simultaneously.
Network Security Architecture:
Centralized security management allows security policies and tools to be deployed across all sites in the network. This consistency helps ensure that security standards are maintained and reduces the administrative overhead of managing multiple sites.
Site isolation prevents security incidents on one site from affecting other sites in the network. Proper isolation includes separate databases, file systems, and user accounts where possible.
Shared resource security includes plugins, themes, and other resources that are used across multiple sites. These shared resources require careful security management as vulnerabilities can affect the entire network.
Network monitoring provides visibility into security events across all sites in the network. Centralized monitoring helps identify attack patterns and security trends that might not be visible when examining individual sites.
Scalability and Performance Considerations:
Security tool performance becomes more critical in multi-site environments where the impact is multiplied across multiple sites. Efficient security tools and proper resource allocation help maintain performance while providing comprehensive protection.
Update coordination across multiple sites requires careful planning to ensure that updates are applied consistently without causing widespread issues. Staged rollouts and testing procedures help manage update risks in large networks.
Resource sharing for security tools and services can provide cost efficiencies and improved management. However, shared resources must be properly configured to provide appropriate protection for all sites in the network.
Incident response procedures must account for the potential impact of security incidents across multiple sites. Response plans should include procedures for isolating affected sites and coordinating response efforts across the network.
6.3 Compliance Requirements and Standards
Many WordPress sites must comply with industry-specific regulations or security standards. Understanding compliance requirements helps ensure that security implementations meet legal and regulatory obligations.
GDPR and Privacy Compliance:
Data protection requirements under GDPR include lawful basis for processing, data minimization, accuracy, storage limitation, and security. WordPress sites must implement technical and organizational measures to protect personal data.
Consent management systems help ensure that data collection and processing comply with GDPR consent requirements. These systems must provide clear information about data use and allow users to withdraw consent easily.
Data portability rights require organizations to provide personal data in a structured, commonly used format when requested. WordPress sites should have procedures for extracting and providing user data.
Breach notification requirements mandate that data breaches be reported to supervisory authorities within 72 hours and to affected individuals without undue delay. Incident response procedures should include breach notification processes.
Industry-Specific Standards:
HIPAA compliance is required for healthcare organizations and their business associates. HIPAA security requirements include access controls, audit controls, integrity controls, transmission security, and assigned security responsibility.
SOX compliance affects publicly traded companies and requires controls over financial reporting systems. WordPress sites that support financial reporting may need to implement SOX-compliant security controls.
ISO 27001 provides a framework for information security management systems. Organizations seeking ISO 27001 certification must implement comprehensive security controls and undergo regular audits.
NIST Cybersecurity Framework provides guidelines for managing cybersecurity risk. The framework includes functions for identify, protect, detect, respond, and recover that can guide WordPress security implementations.
6.4 Performance vs Security Balance
Security measures inevitably impact site performance, but the extent of this impact depends on implementation choices and optimization strategies. Balancing security and performance requires understanding the trade-offs and implementing efficient solutions.
Optimization Strategies:
Caching security involves implementing caching systems that don’t compromise security controls. Security headers, authentication systems, and dynamic content must be properly handled in cached environments.
CDN configuration can improve both performance and security by distributing content globally and providing DDoS protection. However, CDN security configurations must be properly managed to maintain protection effectiveness.
Database optimization helps maintain performance when security tools generate additional database activity. Regular database maintenance, query optimization, and proper indexing help manage security tool impact.
Resource management involves allocating server resources appropriately between security tools and application performance. Monitoring resource usage helps identify optimization opportunities and capacity requirements.
Trade-off Analysis:
Security impact assessment evaluates how security measures affect site performance and user experience. This analysis helps prioritize security measures based on their protection value relative to their performance cost.
Risk tolerance decisions involve accepting some security risks to maintain acceptable performance levels. These decisions should be based on thorough risk analysis and business requirements.
Business requirements may dictate performance standards that limit security implementation options. Understanding these requirements helps identify security solutions that meet both performance and protection needs.
Monitoring and measurement provide ongoing visibility into the performance impact of security measures. Regular performance testing helps identify when security configurations need adjustment to maintain acceptable performance levels.
7. Implementation Roadmap
Implementing comprehensive WordPress security can seem overwhelming, but a systematic approach makes it manageable and ensures that the most critical protections are implemented first. This 30-day roadmap prioritizes security measures based on their impact and ease of implementation.
7.1 30-Day Security Implementation Plan
This implementation plan is designed to transform a basic WordPress installation into a comprehensively secured site within 30 days. The plan prioritizes high-impact, low-complexity measures first, building toward more advanced protections.
Week 1: Foundation and Critical Security (Days 1-7)
Day 1-2 focuses on security assessment and establishing baselines. Begin with a comprehensive security scan using Security Ninja or similar tools to identify current vulnerabilities and security gaps. Document all installed plugins, themes, and current WordPress version. Create an inventory of user accounts and their roles. This assessment provides the foundation for all subsequent security improvements.
Day 3-4 addresses the most critical security updates. Update WordPress core to the latest version, ensuring that all security patches are applied. Update all plugins and themes, paying special attention to any that have security updates available. Remove any plugins or themes that are no longer needed or haven’t been updated recently. These updates address the majority of known vulnerabilities and provide immediate security improvements.
Day 5-6 implements strong authentication measures. Change all user passwords to strong, unique passwords using a password manager. Enable two-factor authentication for all administrator accounts and encourage other users to adopt 2FA. Review user accounts and remove any that are no longer needed. Create new administrator accounts with unique usernames if the default “admin” account exists.
Day 7 configures SSL/HTTPS encryption. Install an SSL certificate if one isn’t already present, or verify that the existing certificate is properly configured. Update WordPress settings to use HTTPS URLs throughout the site. Implement HTTPS redirects to ensure all traffic uses encrypted connections. Test the SSL configuration using online SSL testing tools to verify proper implementation.
Week 2: Protection and Monitoring (Days 8-14)
Day 8-9 involves security plugin installation and configuration. Install Security Ninja or another comprehensive security plugin and perform initial configuration. Enable firewall protection, malware scanning, and login protection features. Configure email notifications for security events and ensure that alerts are being received properly.
Day 10-11 establishes backup systems. Install and configure a reliable backup plugin or service that provides automated, off-site backups. Test the backup system by performing a restore to a staging environment. Establish a backup schedule that balances data protection with storage costs and performance impact. Document backup and restore procedures for emergency use.
Day 12-13 implements basic security hardening measures. Change the WordPress database prefix if still using the default “wp_” prefix. Disable file editing through the WordPress admin interface. Configure proper file permissions for WordPress files and directories. Implement basic .htaccess security rules to protect sensitive files and directories.
Day 14 conducts user access review and cleanup. Audit all user accounts to ensure appropriate role assignments. Remove inactive accounts and downgrade accounts with excessive privileges. Implement user session management controls and configure appropriate session timeout settings. Document user access procedures for ongoing management.
Week 3: Advanced Hardening (Days 15-21)
Day 15-16 focuses on advanced WordPress configuration hardening. Update security keys and salts in wp-config.php with new random values. Configure debug settings appropriately for production use. Implement additional wp-config.php security measures like disabling file modifications and controlling automatic updates.
Day 17-18 implements server-level security measures. Configure .htaccess rules for enhanced security including access controls, file type restrictions, and security headers. Implement PHP security configurations if server access is available. Configure web server security headers like Content Security Policy and X-Frame-Options.
Day 19-20 establishes monitoring and alerting systems. Configure comprehensive logging for security events, login attempts, and file changes. Set up monitoring for website uptime, performance, and security status. Implement alerting systems that provide timely notification of security events without creating alert fatigue.
Day 21 performs security testing and validation. Conduct penetration testing or vulnerability scanning to verify that security measures are working correctly. Test backup and restore procedures to ensure they function properly. Verify that all security configurations are working as expected and make adjustments as needed.
Week 4: Optimization and Documentation (Days 22-30)
Day 22-24 optimizes performance while maintaining security. Review the performance impact of security measures and optimize configurations to minimize slowdowns. Implement caching strategies that work with security tools. Configure CDN services if appropriate, ensuring that security protections remain effective.
Day 25-27 creates documentation and procedures. Document all security configurations, procedures, and contact information for emergency use. Create incident response procedures tailored to the specific site and organization. Develop maintenance schedules for ongoing security tasks like updates, backups, and monitoring.
Day 28-29 provides team training and knowledge transfer. Train team members on security procedures, incident response, and ongoing maintenance tasks. Ensure that multiple people understand critical security systems and procedures. Create training materials and reference guides for future use.
Day 30 conducts final security audit and certification. Perform a comprehensive security review to verify that all planned security measures have been implemented correctly. Document the current security posture and create a baseline for future security assessments. Celebrate the achievement of comprehensive WordPress security implementation.
7.2 Priority-Based Action Items
Not all security measures are equally important, and resource constraints may require prioritizing the most critical protections first. This priority framework helps focus efforts on the measures that provide the greatest security improvement.
Critical Priority (Immediate Implementation):
WordPress core and plugin updates represent the highest priority security measures because they address known vulnerabilities that attackers actively exploit. These updates should be applied immediately upon availability, with security updates taking precedence over feature updates.
Strong password implementation across all user accounts provides fundamental protection against the most common attack vector. Weak passwords enable brute force attacks, credential stuffing, and account takeover attempts that can compromise entire sites.
SSL certificate installation and HTTPS enforcement protect data in transit and are required for modern web security. Search engines penalize non-HTTPS sites, and browsers display security warnings for unencrypted sites.
Basic security plugin setup provides automated protection against common attacks and ongoing monitoring for security threats. A properly configured security plugin can prevent many attacks and provide early warning of security incidents.
High Priority (Week 1-2 Implementation)
Two-factor authentication significantly improves authentication security and should be implemented for all administrative accounts as soon as possible. 2FA prevents account compromise even when passwords are stolen or guessed.
User role optimization ensures that users have appropriate access levels and reduces the risk of accidental or malicious damage. Regular user access reviews help maintain proper access controls over time.
Backup system configuration provides essential protection against data loss from security incidents, hardware failures, or human error. Reliable backups enable quick recovery from various types of disasters.
Basic hardening measures like changing database prefixes, disabling file editing, and implementing proper file permissions provide additional protection layers with minimal complexity or performance impact.
Medium Priority (Week 3-4 Implementation)
Advanced hardening measures provide enhanced protection but require more technical expertise and may have greater performance impact. These measures are appropriate once basic security foundations are established.
Monitoring and alerting systems provide ongoing visibility into security status and early warning of potential incidents. While not immediately protective, monitoring enables faster response to security events.
Performance optimization ensures that security measures don’t negatively impact user experience or business operations. Balancing security and performance requires ongoing attention and adjustment.
Documentation and training ensure that security measures can be maintained effectively over time. While not immediately protective, proper documentation and training are essential for long-term security success.
7.3 Ongoing Security Maintenance
WordPress security is not a one-time implementation but an ongoing process that requires regular attention and maintenance. Establishing sustainable maintenance procedures ensures that security protections remain effective over time.
Daily Security Tasks:
Security alert monitoring should be performed daily to ensure that critical security events receive prompt attention. This includes reviewing alerts from security plugins, monitoring services, and server logs for signs of malicious activity.
Backup verification ensures that automated backup systems are functioning correctly and that recent backups are available for recovery if needed. Daily backup checks help identify and resolve backup issues before they become critical.
Performance monitoring tracks site speed and availability, which can be affected by security incidents or security tool configurations. Daily performance checks help identify issues that might indicate security problems or need for optimization.
Threat intelligence review keeps security teams informed about new threats, vulnerabilities, and attack techniques that might affect WordPress sites. Daily threat intelligence helps maintain awareness of the evolving security landscape.
Weekly Security Tasks
Update checking and installation should be performed weekly to ensure that security patches are applied promptly. While critical security updates should be applied immediately, weekly update reviews help ensure that no updates are overlooked.
Security scan execution provides regular assessment of site security status and can identify new vulnerabilities or configuration issues. Weekly scans help maintain awareness of the current security posture and identify areas needing attention.
Log analysis involves reviewing security logs, access logs, and error logs for patterns that might indicate security issues or needed configuration changes. Weekly log reviews help identify trends and potential problems.
User access review ensures that user accounts remain appropriate and that inactive accounts are identified and removed. Weekly user reviews help maintain proper access controls and reduce security risks from unused accounts.
Monthly Security Tasks
Comprehensive security audits provide thorough assessment of all security measures and can identify issues that daily and weekly checks might miss. Monthly audits should include vulnerability scanning, configuration review, and security procedure evaluation.
Backup testing involves actually restoring backups to verify that they work correctly and contain the expected data. Monthly backup tests help ensure that recovery procedures will work when needed during actual emergencies.
Security training updates keep team members informed about new threats, security procedures, and best practices. Monthly training sessions help maintain security awareness and ensure that procedures are followed correctly.
Procedure review and updates ensure that security procedures remain current and effective as threats evolve and systems change. Monthly procedure reviews help identify needed updates and improvements to security processes.
8. Conclusion and Next Steps
WordPress security in 2026 requires a comprehensive, multi-layered approach that addresses the evolving threat landscape while maintaining site performance and usability. The strategies and techniques outlined in this guide provide a complete framework for protecting WordPress sites against the full spectrum of security threats.
Key Takeaways and Security Principles
The foundation of effective WordPress security rests on understanding that security is an ongoing process, not a one-time implementation. The 7,966 new vulnerabilities discovered in the WordPress ecosystem in 2024 demonstrate that threats continue to evolve, requiring constant vigilance and adaptation of security measures.
Layered security provides the most effective protection by implementing multiple overlapping security controls. When one layer fails or is bypassed, other layers continue to provide protection. This defense-in-depth approach significantly improves overall security resilience and reduces the likelihood of successful attacks.
Proactive security measures are always more effective and less costly than reactive responses to security incidents. Implementing comprehensive security before problems occur prevents the significant costs associated with malware cleanup, data recovery, reputation damage, and business disruption.
Business alignment ensures that security measures support rather than hinder business objectives. Security implementations should consider user experience, performance requirements, and operational constraints while providing appropriate protection for the site’s risk profile and business requirements.
Implementation Priorities and Action Steps
The 30-day implementation roadmap provides a structured approach to achieving comprehensive WordPress security, but the specific priorities may vary based on individual site requirements and risk profiles. High-traffic e-commerce sites require more aggressive security measures than personal blogs, while sites handling sensitive data need additional compliance considerations.
Critical security foundations should be implemented immediately regardless of site type or size. These include WordPress core and plugin updates, strong authentication, SSL/HTTPS encryption, and basic security plugin configuration. These measures address the most common attack vectors and provide essential protection against automated threats.
Advanced security hardening becomes increasingly important as site value and risk exposure increase. Server-level security configurations, advanced monitoring systems, and professional security services provide enhanced protection for sites that justify the additional complexity and cost.
Professional security services may be appropriate for sites with high security requirements, limited internal expertise, or complex compliance obligations. Security consultants, managed security services, and specialized WordPress security providers can supplement internal capabilities and provide expert guidance.
Security Ninja Plugin Recommendation
Throughout this guide, we’ve referenced Security Ninja as an example of comprehensive WordPress security implementation. This plugin represents the culmination of years of WordPress security experience and provides many of the advanced features discussed in this guide through an integrated, user-friendly interface.
Security Ninja’s comprehensive approach includes vulnerability scanning, malware detection, security hardening, and real-time monitoring in a single solution. This integration eliminates the complexity of managing multiple security tools while providing enterprise-grade protection for WordPress sites of all sizes.
The plugin’s automated security features can implement many of the advanced hardening measures discussed in this guide without requiring deep technical expertise. This automation makes comprehensive security accessible to site owners who lack the time or knowledge to implement complex security configurations manually.
Regular updates and threat intelligence ensure that Security Ninja remains effective against evolving threats. The development team actively monitors the WordPress security landscape and updates the plugin to address new vulnerabilities and attack techniques as they emerge.
Professional support and documentation provide assistance with implementation, configuration, and incident response. This support can be invaluable during security incidents when expert guidance can minimize damage and reduce recovery time.
Additional Resources and Professional Services
WordPress security extends beyond what any single guide or tool can provide. Staying informed about evolving threats, new security techniques, and best practices requires ongoing education and engagement with the WordPress security community.
Security communities and forums provide valuable resources for staying current with WordPress security developments. The WordPress Security Team, security-focused WordPress meetups, and professional security organizations offer opportunities to learn from experts and share experiences with other security practitioners.
Professional development through security training, certifications, and conferences helps build the expertise needed for advanced WordPress security implementations. Investing in security education pays dividends through improved security decision-making and more effective incident response.
Vendor relationships with security tool providers, hosting companies, and professional services firms provide access to expertise and resources that may not be available internally. Building relationships with trusted security partners before they’re needed ensures rapid response when security incidents occur.
Industry resources including threat intelligence feeds, vulnerability databases, and security research publications help maintain awareness of the evolving threat landscape. Staying informed about new threats and attack techniques enables proactive security measures and better protection strategies.
The Path Forward
WordPress security in 2026 and beyond will continue to evolve as threats become more sophisticated and the WordPress ecosystem grows more complex. Artificial intelligence and machine learning will play increasingly important roles in both attack and defense, requiring security practitioners to adapt their strategies and tools.
Automation will become increasingly important for managing security at scale as the number of WordPress sites continues to grow. Security tools that can automatically detect, respond to, and recover from security incidents will become essential for maintaining effective protection with limited human resources.
Compliance requirements will likely become more stringent as governments and industries recognize the importance of cybersecurity. WordPress site owners should prepare for additional regulatory requirements and consider compliance implications in their security planning.
Integration between security tools and WordPress development workflows will improve, making security a more natural part of the site development and maintenance process. DevSecOps practices will become more common in WordPress development, embedding security throughout the development lifecycle.
The investment in comprehensive WordPress security today provides protection not just against current threats, but also creates a foundation for adapting to future security challenges. Sites with strong security foundations can more easily adopt new security technologies and respond to emerging threats.
WordPress powers over 40% of the internet, making its security critical not just for individual site owners but for the broader internet ecosystem. By implementing comprehensive security measures, WordPress site owners contribute to a more secure internet for everyone.
The choice is clear: invest in comprehensive security now, or risk the significant costs and consequences of security incidents later. The strategies, tools, and techniques outlined in this guide provide everything needed to make WordPress sites secure, resilient, and ready for the challenges ahead.
Frequently Asked Questions
Q: How often should I update my WordPress security measures?
A: WordPress core and plugin updates should be applied immediately when they contain security fixes. Security configurations should be reviewed monthly, and comprehensive security audits should be performed quarterly. However, security monitoring should be continuous to detect and respond to threats in real-time.
Q: Is it safe to automatically update WordPress plugins?
A: Automatic updates can be safe for security-focused plugins with good track records, but they require proper backup systems and monitoring. Critical security updates should be applied quickly, but testing in a staging environment is recommended when possible. The risk of delayed security updates usually outweighs the risk of automatic update issues.
Q: What’s the most important security measure for WordPress sites?
A: Keeping WordPress core, plugins, and themes updated is the single most important security measure, as it addresses the majority of known vulnerabilities. However, comprehensive security requires multiple layers including strong authentication, SSL encryption, security plugins, and regular backups.
Q: How do I know if my WordPress site has been compromised?
A: Signs of compromise include unexpected changes to site content, new admin users, unfamiliar files, slow performance, search engine warnings, and unusual traffic patterns. Security plugins can detect many signs of compromise automatically and provide alerts when suspicious activity is detected.
Q: Should I use a security plugin or implement security measures manually?
A: Most sites benefit from using a comprehensive security plugin like Security Ninja combined with manual security hardening measures. Security plugins provide automation, monitoring, and expertise that would be difficult to implement manually, while manual measures provide additional customization and control.
Q: How much should I expect to spend on WordPress security? A: Basic security can be implemented with free tools and minimal cost, while comprehensive security including premium plugins, professional services, and advanced tools may cost several hundred dollars annually. However, this investment is minimal compared to the potential costs of security incidents, which can reach thousands or tens of thousands of dollars.
Q: What should I do if my WordPress site gets hacked? A: Immediately change all passwords, scan for malware, restore from clean backups if available, update all software, and consider professional malware removal services for complex infections. Document the incident, notify relevant parties if required, and implement additional security measures to prevent recurrence.
About Security Ninja: Security Ninja is a comprehensive WordPress security plugin developed by security experts with years of experience protecting WordPress sites. The plugin provides automated vulnerability scanning, malware detection, security hardening, and real-time monitoring to keep WordPress sites secure against evolving threats.
Get Security Ninja: Download Security Ninja and start protecting your WordPress site today with professional-grade security tools and expert support.
[/box]Need Professional Help?: Our security experts are available for consultation, security audits, malware removal, and custom security implementations. Contact us for professional WordPress security services.[/box]
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.