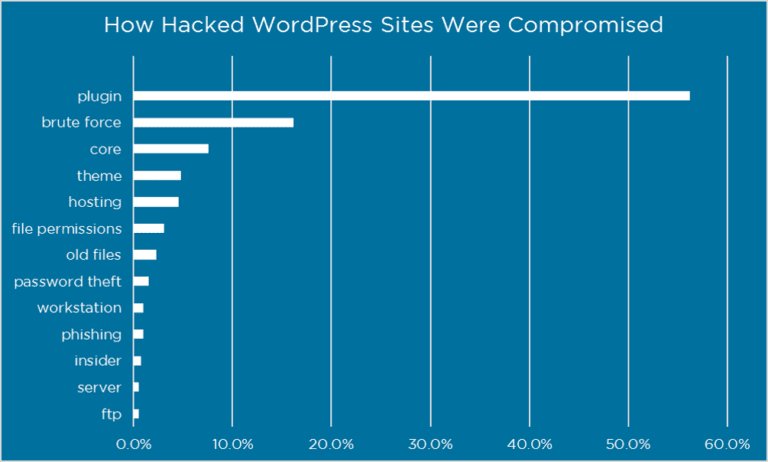
While there are tons of ways to build a website, WordPress remains the most popular option. The ease of use, the broad range of functions and features, the library of powerful plugins, and many other factors contribute to this popularity. Security risks in WordPress plugins are unfortunately far too common.
Any number of security issues can affect your website security, but one that might catch you by surprise is the fact that the very plugins that you depend on for usability can become risks. How does this happen and how can you mitigate any potential fallout?
Contents
How Do WordPress Plugins Pose Security Risks?

Plugins are supposed to be helpful tools that allow WordPress website owners to do more than what is possible with the platform out of the box. They range from SEO tools to backup solutions and everything in between. Admittedly, some plugins are little more than gimmicks, but many do offer outstanding value and performance.
However, there are problems here.
Plugins can become security risks in several ways. One of those is if you do not regularly update your plugins.
Another is if the plugin developer stops releasing updates, leaving you vulnerable to future threats. These so-called “abandoned” plugins may not pose an active risk, but they eventually become outdated and susceptible to threats because they are no longer actively maintained.
Another way that plugins can be security risks is if you are using a “nulled” plugin. These are free versions of paid plugins and they almost always carry significant risks with them.
Finally, WordPress plugins can become security risks for your site when you stop using them. This is very similar to how unused apps on your phone or tablet can eventually become sources of risk.
What can you do to protect your website against these sources of risk? Actually, there are several smart practices that WordPress website owners should be following.
How to prevent Security risks in WordPress plugins
Install a Web Application Firewall
Your website’s security is a critical consideration and not something that can be left to chance. The first thing you should do to protect against potential zero-day exploits is to have a web application firewall, or WAF, installed.
These firewalls help to reduce your risk by filtering website traffic and eliminating malicious threats. Think of it this way – you would never run your PC without a firewall between you and the dangers of the Internet, would you? Then why would you ever operate a website without the same protection?
Vet your plugins thoroughly
Sure, there are tens of thousands of plugins out there that all seem to offer something of value. However, just because they’re listed in the official repository, that doesn’t mean that they’re worth your time. Also, just to be clear, never use plugins that aren’t made available through official channels.

If you do use a third-party repository, make sure that they take the same stringent steps that WordPress does before allowing plugins to be listed. Otherwise, it’s a great way to find your website hacked and your data compromised.
When choosing your plugins, look beyond the functions and features offered. Visit the developer’s website and have a look around.
You’re looking for signs that the plugin might not be worth downloading and installing, such as a low-quality website, an unknown developer name, no terms of service or privacy policy, or a lack of company information on the website.
Check out the number of active installations for the plugin. Check the last time it was updated, and make sure that it’s compatible with the most current version of WordPress’s core system.
Of course, you should always check the ratings for any plugins that you’re considering. Low ratings should be a warning. Higher ratings should make you more confident.
Update your plugins
Another important consideration here is that you keep your plugins up to date. When a security vulnerability is discovered in a plugin, it’s usually announced to the world at large. That means in addition to website owners, potential hackers now have this information and can exploit it. If a plugin has an auto-update feature, turn it on. If it doesn’t, think twice about installing it. If you decide to go ahead, make sure you check the developer’s website regularly and apply any updates. When they’re released.
Limit the Number of Plugins
The fewer plugins you have, the less risk you run. It can be tempting to install multiple plugins to test, but then forget to remove them later. Those apps then sit there, doing nothing more than increasing your level of risk. The simplest rule of thumb here is that if you’re not actually using a plugin, you should remove it. Regularly take inventory of your plugins, note which ones are in use and if any are not, and delete those that you do not use.
Delete unused plugins
As the website owner, chances are good that you’re also responsible for adding plugins and then taking them offline when you no longer use them. We’ve already talked about the danger that unused plugins can cause, so use this opportunity to nip that potential in the bud. When you remove a plugin and you are not going to use it any longer, delete it completely.
In Conclusion
Ultimately, WordPress plugins provide you with utility and functionality that is unavailable with the core platform. They’re valuable additions to any website, whether you’re running a personal blog, an e-commerce website, a corporate website, or something else completely.
However, they are not always benign. They can compromise your security and lead to an increased risk of being victimized by an attacker.
By following the tips we’ve covered above, you can limit your risk. Be proactive and take control of your plugins.
Written by Lars Koudal