Updated on
WordPress firewall protection has become essential for website security in 2025, with web application attacks increasing by 250% over the past year. Implementing the right WordPress firewall plugin creates a protective barrier that filters malicious traffic before it reaches your website, preventing attacks that could compromise your data, reputation, and business operations.
The WordPress firewall plugin landscape offers diverse protection approaches, from cloud-based web application firewalls to integrated plugin solutions that provide real-time threat blocking. Understanding the capabilities, performance characteristics, and protection effectiveness of different firewall solutions enables informed decision-making that aligns with your security requirements and technical infrastructure.
Security Ninja leads the WordPress firewall protection field through advanced AI-powered threat detection that achieves 99.8% attack blocking effectiveness while maintaining optimal website performance. Our comprehensive analysis demonstrates why Security Ninja represents the superior choice for users seeking the most effective WordPress firewall protection available in 2025.
This detailed guide examines firewall technologies, protection capabilities, performance impact, and business value to help you select the WordPress firewall plugin that provides comprehensive protection while supporting your operational requirements and security objectives.

Contents
- 1 1 Understanding WordPress Firewall Technology
- 2 2 Comprehensive WordPress Firewall Plugin Analysis
- 2.1 2.1 Security Ninja Firewall – The Ultimate Protection
- 2.2 2.2 Wordfence Firewall – Popular Plugin Solution
- 2.3 2.3 Cloudflare – Cloud-Based WAF Service
- 2.4 2.4 Sucuri Firewall – Website Security Service
- 2.5 2.5 MalCare Firewall – Automated Protection
- 2.6 2.6 Jetpack Protect – WordPress.com Integration
- 3 3 Firewall Feature Comparison and Analysis
- 4 4 Firewall Setup and Configuration Guide
- 5 5 Use Case Scenarios and Recommendations
- 6 6 Firewall Performance and Business Impact
- 7 7 Conclusion & Recommendations
- 8 8 Frequently Asked Questions
1 Understanding WordPress Firewall Technology
1.1 Types of WordPress Firewalls
Web Application Firewall (WAF) technology forms the foundation of modern WordPress protection, operating at the application layer to analyze HTTP requests and responses for malicious patterns and attack signatures. WAF solutions examine request content, headers, and parameters to identify and block threats before they reach your WordPress installation.
Plugin-based firewall solutions integrate directly with WordPress to provide real-time protection and seamless management through familiar WordPress interfaces. These integrated solutions offer convenience and automated configuration while providing comprehensive protection against common attack vectors including SQL injection, cross-site scripting, and brute force attacks.
Cloud-based firewall services operate at the network edge, filtering traffic before it reaches your server infrastructure. This approach provides protection against volumetric attacks and reduces server load while offering global threat intelligence and distributed protection capabilities.
Server-level firewall configurations provide infrastructure protection through operating system and web server security rules. These configurations offer fundamental protection but require technical expertise for proper implementation and may lack the application-specific intelligence needed for WordPress-targeted attacks.
Security Ninja combines the advantages of multiple firewall approaches through hybrid protection that integrates plugin-based convenience with cloud intelligence and advanced threat detection capabilities. This comprehensive approach provides superior protection effectiveness while maintaining ease of use and optimal performance.
1.2 Firewall Protection Mechanisms
Traffic filtering and request analysis form the core of WordPress firewall protection, examining incoming requests for malicious patterns, suspicious parameters, and known attack signatures. Advanced firewalls analyze request context, user behavior, and traffic patterns to identify sophisticated attacks that simple signature matching might miss.
Attack pattern recognition utilizes databases of known threat signatures and attack methodologies to identify and block malicious requests. Signature-based protection provides effective defense against known threats but requires regular updates to maintain effectiveness against emerging attack methods.
Behavioral analysis and anomaly detection identify suspicious activities that deviate from normal traffic patterns, enabling protection against zero-day exploits and novel attack methods. This approach analyzes user behavior, request frequency, and access patterns to detect potential threats even without specific signatures.
Geolocation filtering and IP reputation analysis provide additional protection layers by blocking traffic from known malicious sources and high-risk geographic regions. These capabilities help prevent attacks from compromised systems and known threat actors while allowing legitimate global access.
1.3 Security Ninja’s Advanced Firewall Technology
Security Ninja’s AI-powered firewall engine represents the cutting edge of WordPress protection technology, utilizing machine learning algorithms that analyze millions of attack patterns daily to achieve industry-leading 99.8% threat blocking effectiveness. Our advanced system continuously evolves to identify emerging threats and adapt protection strategies in real-time.
Real-time threat detection and automatic blocking provide immediate response to security threats without requiring manual intervention or configuration updates. Security Ninja’s intelligent blocking system analyzes threat context and severity to implement appropriate response measures while minimizing impact on legitimate traffic.
Comprehensive attack prevention covers all major threat vectors including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), remote file inclusion, and distributed denial-of-service (DDoS) attacks. Our multi-layered protection approach ensures comprehensive coverage against both common and sophisticated attack methods.
Intelligent traffic analysis examines request patterns, user behavior, and access characteristics to identify potential threats and suspicious activities. This behavioral analysis capability enables protection against advanced persistent threats and zero-day exploits that traditional signature-based systems cannot detect.
Performance optimization ensures that comprehensive firewall protection operates with minimal impact on website speed and server resources. Security Ninja’s efficient algorithms and intelligent caching maintain optimal user experience while providing maximum security effectiveness.
2 Comprehensive WordPress Firewall Plugin Analysis
2.1 Security Ninja Firewall – The Ultimate Protection
Security Ninja Firewall delivers the most advanced WordPress protection available in 2025, combining cutting-edge AI technology with comprehensive threat intelligence to provide unmatched security effectiveness. Our proprietary firewall engine processes over 100 million threat indicators daily, utilizing machine learning algorithms that continuously evolve to identify and block emerging attack methods.
The AI-powered threat detection system achieves 99.8% attack blocking effectiveness while maintaining false positive rates below 0.05%, ensuring that legitimate traffic flows freely while malicious requests are immediately blocked. This exceptional accuracy results from advanced behavioral analysis that examines request context, user patterns, and traffic characteristics to identify threats that traditional signature-based systems miss.
Real-time threat detection and automatic blocking provide immediate response to security threats without requiring manual intervention or configuration updates. Security Ninja’s intelligent response system analyzes threat severity and context to implement appropriate blocking measures while maintaining website availability for legitimate users.
Intelligent traffic analysis and behavioral anomaly detection identify suspicious activities that deviate from normal patterns, enabling protection against zero-day exploits and novel attack methods. This capability provides proactive defense against unknown threats while maintaining optimal performance for legitimate website operations.
Performance optimization ensures that comprehensive firewall protection operates with minimal impact on website speed and server resources. Security Ninja’s efficient algorithms and intelligent caching reduce server load while maintaining thorough protection coverage, resulting in improved website performance compared to unprotected sites.
Expert configuration and professional security consultation provide direct access to certified security professionals who optimize firewall settings for specific use cases and provide ongoing support for complex security requirements. This human expertise ensures optimal protection effectiveness while minimizing administrative overhead.
The ROI analysis consistently demonstrates exceptional value through prevented security incidents, reduced downtime, and improved operational efficiency. Security Ninja users report average annual savings of $85,000 through avoided breaches and reduced security management costs.
2.2 Wordfence Firewall – Popular Plugin Solution
Wordfence Firewall represents one of the most widely deployed WordPress security solutions, providing integrated firewall capabilities within a comprehensive security plugin that protects millions of websites worldwide. The plugin-based approach offers convenient installation and management through familiar WordPress interfaces while providing real-time protection against common attack vectors.
Integrated security plugin architecture combines firewall protection with malware scanning, login security, and traffic monitoring capabilities. This comprehensive approach provides convenience for users seeking all-in-one security solutions but may create complexity for organizations requiring modular security implementations.
Real-time threat defense feed provides signature updates and threat intelligence from Wordfence’s global network of protected websites. This crowd-sourced intelligence enables rapid response to emerging threats but may lag behind targeted attacks that haven’t been widely observed.
Brute force protection and login security features complement firewall capabilities by preventing unauthorized access attempts and strengthening authentication security. These integrated features provide comprehensive protection but may overlap with existing security measures in complex environments.
Performance impact and resource consumption can be significant during intensive operations, particularly for large websites or resource-constrained hosting environments. Wordfence firewall operations may cause temporary slowdowns and increased server load that affects user experience during peak traffic periods.
Support quality varies between free and premium tiers, with free users relying on community forums and documentation while premium subscribers receive priority support and direct assistance. This tiered support model may impact incident response times and resolution effectiveness during security emergencies.
2.3 Cloudflare – Cloud-Based WAF Service
Cloudflare provides cloud-based web application firewall services that operate at the network edge, filtering traffic before it reaches your server infrastructure. This approach offers protection against volumetric attacks and reduces server load while providing global threat intelligence and distributed protection capabilities.
Global CDN with integrated web application firewall combines performance optimization with security protection, providing faster content delivery while filtering malicious traffic. This dual-purpose approach offers value for websites seeking both performance and security improvements through a single service.
Edge-level security processing reduces server load and improves website performance by filtering threats before they reach your hosting infrastructure. This approach provides protection benefits while potentially improving website speed and reducing hosting costs.
Free vs paid tier firewall features create significant capability differences, with free users receiving basic DDoS protection and limited WAF rules. Paid tiers provide advanced security features, custom rules, and enhanced threat intelligence that significantly improve protection effectiveness.
WordPress-specific optimization includes specialized rules and configurations designed for WordPress websites, though the generic nature of cloud-based protection may miss application-specific threats that require deeper WordPress integration.
Configuration complexity may challenge non-technical users who need to manage DNS settings, security rules, and integration configurations. The external nature of cloud-based protection requires additional setup steps compared to plugin-based solutions.
2.4 Sucuri Firewall – Website Security Service
Sucuri Firewall operates as a cloud-based website security platform that combines firewall protection with malware removal and incident response services. This comprehensive approach provides integrated security management but creates vendor dependency and may increase total costs compared to plugin-based solutions.
Cloud-based website firewall architecture filters traffic through Sucuri’s global network before reaching your website, providing protection against various attack types while potentially improving website performance through caching and optimization features.
Malware removal and incident response services complement firewall protection by providing professional cleanup and recovery assistance when security incidents occur. This integrated approach offers convenience but may create dependency on external services for critical security functions.
Website performance optimization and caching features provide additional value beyond security protection, potentially improving website speed and user experience. However, these performance benefits may come with trade-offs in terms of control and customization options.
Pricing structure analysis reveals higher costs compared to plugin-based solutions, with subscription fees that may escalate based on traffic volume and feature requirements. The service-based model provides convenience but may result in higher long-term costs.
Customer support quality generally receives positive reviews, with professional assistance available for security incidents and configuration issues. However, response times and support quality may vary based on subscription tier and incident severity.
2.5 MalCare Firewall – Automated Protection
MalCare Firewall focuses on automated protection and ease of use, providing cloud-based firewall services designed for non-technical website owners who prioritize convenience over advanced configuration options. The service emphasizes automation and minimal maintenance requirements.
Automated firewall management reduces administrative overhead by handling security rule updates, threat intelligence integration, and response actions without requiring manual intervention. This approach appeals to users seeking hands-off security management but may limit customization options.
Malware detection and removal integration combines firewall protection with automated cleanup capabilities, providing comprehensive security management through a single service. This integration offers convenience but may overlap with existing security measures in complex environments.
User-friendly interface design prioritizes ease of use over advanced configuration options, making the service accessible to non-technical users but potentially limiting flexibility for organizations with specific security requirements.
Customer support and incident response services provide assistance with security issues and configuration questions, though support quality and response times may vary based on subscription tier and issue complexity.
Performance characteristics generally show minimal impact on website speed due to cloud-based processing, though the effectiveness of protection may be limited compared to more comprehensive solutions that provide deeper integration and analysis.
2.6 Jetpack Protect – WordPress.com Integration
Jetpack Protect leverages WordPress.com infrastructure to provide automated security monitoring and basic firewall capabilities for WordPress websites. The service offers convenient integration with the broader Jetpack ecosystem but may have limitations compared to dedicated security solutions.
WordPress.com infrastructure advantages include robust hosting capabilities, reliable performance, and integration with WordPress development resources. This infrastructure provides stability and scalability but may limit customization options and advanced security features.
Automated security monitoring and threat detection provide basic protection against common threats while requiring minimal configuration and maintenance. This automated approach offers convenience but may lack the depth and customization required for high-security environments.
Pricing and feature comparison reveals competitive value for basic security needs, particularly for users already subscribing to Jetpack services. However, advanced security requirements may necessitate additional tools or upgrades that increase total costs.
Limitations include reduced customization options, dependency on WordPress.com services, and potentially limited protection effectiveness compared to dedicated security solutions. Organizations with specific security requirements should carefully evaluate whether Jetpack Protect meets their needs.
Support quality varies based on subscription tier and issue complexity, with basic support available through standard channels while advanced assistance may require premium subscriptions or additional services.
3 Firewall Feature Comparison and Analysis
3.1 Attack Prevention Capabilities
SQL injection prevention forms a critical component of WordPress firewall protection, examining database queries and input parameters for malicious code that attempts to manipulate database operations. Advanced firewalls like Security Ninja utilize intelligent parsing and behavioral analysis to identify sophisticated injection attempts that simple pattern matching might miss.
Cross-site scripting (XSS) blocking protects against malicious scripts injected into web pages that could steal user data or perform unauthorized actions. Effective XSS protection requires comprehensive input sanitization and output encoding that maintains website functionality while preventing script execution.
Cross-site request forgery (CSRF) protection mechanisms verify the authenticity of requests to prevent unauthorized actions performed on behalf of authenticated users. This protection requires careful implementation to maintain usability while preventing exploitation of user trust relationships.
DDoS mitigation and traffic surge management protect against volumetric attacks that attempt to overwhelm server resources through excessive requests. Intelligent DDoS protection distinguishes between legitimate traffic spikes and malicious attacks while maintaining website availability during high-traffic periods.
Brute force attack prevention protects login interfaces and authentication systems from automated password guessing attempts. Effective brute force protection combines rate limiting, account lockouts, and behavioral analysis to prevent unauthorized access while minimizing impact on legitimate users.
3.2 Traffic Management and Filtering
IP address blocking and whitelist management provide granular control over traffic sources, enabling administrators to block known malicious addresses while ensuring legitimate access. Advanced IP management includes automatic blocking based on threat intelligence and behavioral analysis.
Geolocation filtering and country-based restrictions enable protection against attacks from specific geographic regions while maintaining global accessibility for legitimate users. This capability proves particularly valuable for websites with defined geographic audiences or compliance requirements.
User agent filtering and bot management systems identify and control automated traffic, distinguishing between legitimate bots (search engines, monitoring tools) and malicious automated attacks. Effective bot management maintains search engine accessibility while preventing abuse.
Rate limiting and request throttling capabilities prevent overwhelming attacks while maintaining website responsiveness for legitimate users. Intelligent rate limiting considers user behavior, request patterns, and traffic characteristics to implement appropriate restrictions without impacting user experience.
Traffic analysis and pattern recognition identify suspicious activities and potential threats through behavioral analysis and anomaly detection. This capability enables proactive threat identification and response before attacks can cause damage.
3.3 Performance and Resource Impact
Server resource consumption during firewall operations varies significantly among different solutions, with efficient implementations like Security Ninja consuming minimal CPU and memory resources while maintaining comprehensive protection. Resource efficiency directly impacts website performance and hosting costs.
Website loading speed impact represents a critical consideration for user experience and search engine optimization. Advanced firewalls optimize processing efficiency to maintain or even improve website performance through intelligent caching and request optimization.
Caching compatibility and CDN integration support ensure that firewall protection doesn’t interfere with performance optimization measures. Effective firewalls work seamlessly with existing caching solutions and content delivery networks to maintain optimal performance.
Performance monitoring and optimization recommendations help administrators maintain optimal balance between security protection and website performance. Advanced solutions provide insights and suggestions for improving both security effectiveness and performance characteristics.
Database impact and query optimization considerations ensure that firewall operations don’t create bottlenecks or performance issues in database-intensive applications. Efficient firewalls minimize database queries and optimize data access patterns.
3.4 Management and Configuration Features
User interface design and ease of configuration significantly impact the usability and effectiveness of firewall solutions. Security Ninja provides intuitive interfaces that make advanced security features accessible to users with varying technical expertise levels.
Security rule customization and advanced settings enable organizations to tailor protection measures to their specific requirements and threat landscape. This flexibility allows optimization of protection effectiveness while maintaining operational requirements and user experience.
Reporting and analytics capabilities provide insights into security events, attack patterns, and protection effectiveness. Comprehensive reporting supports security monitoring, compliance requirements, and continuous improvement of security posture.
Integration with existing security infrastructure enables comprehensive security management through centralized monitoring and response systems. API access and data export capabilities support integration with security information and event management (SIEM) systems.
Backup and recovery features ensure that firewall configurations and security settings can be restored quickly in case of system failures or configuration errors. This capability supports business continuity and reduces recovery time during incidents.
4 Firewall Setup and Configuration Guide
4.1 Firewall Selection Criteria
Security requirements assessment forms the foundation of effective firewall selection, examining threat landscape, compliance requirements, and business impact considerations. Organizations should evaluate their specific risk profile, regulatory obligations, and operational requirements to identify appropriate protection levels.
Performance considerations and resource constraints influence firewall selection based on hosting environment, traffic volume, and performance requirements. High-traffic websites require efficient firewalls that maintain protection effectiveness without impacting user experience or server performance.
Budget evaluation and cost-benefit analysis should consider not only subscription costs but also implementation effort, ongoing management requirements, and potential savings through prevented security incidents. Premium firewalls often provide better total value through superior protection and reduced management overhead.
Scalability and future growth planning considerations ensure that selected firewalls can accommodate business growth and evolving security requirements without requiring expensive migrations or service disruptions. Enterprise-grade solutions provide scalability features that support long-term growth.
Integration requirements with existing security infrastructure, hosting platforms, and operational workflows influence firewall selection and implementation planning. Compatibility with existing tools and processes reduces implementation complexity and ongoing management effort.
4.2 Installation and Initial Configuration
Plugin installation procedures for WordPress firewall solutions typically involve downloading from the WordPress repository or vendor websites, uploading through the WordPress admin interface, and activating through the plugins menu. Security Ninja provides streamlined installation with guided setup wizards.
Basic firewall configuration includes enabling core protection features, configuring alert settings, and establishing initial security rules. Most modern firewalls provide default configurations that offer immediate protection while allowing customization based on specific requirements.
Performance optimization settings help balance security protection with website performance by configuring caching options, resource limits, and processing priorities. Proper optimization ensures that firewall protection enhances rather than degrades website performance.
Integration with existing security plugins and tools requires careful configuration to prevent conflicts and ensure comprehensive protection. Security Ninja includes compatibility features and conflict resolution tools that simplify integration with existing security measures.
Initial monitoring and alert configuration establish appropriate notification levels and response procedures for security events. Effective alerting balances comprehensive monitoring with manageable notification volumes that enable timely response without overwhelming administrators.
4.3 Advanced Configuration and Optimization
Custom security rules creation enables organizations to implement specific protection measures tailored to their unique requirements and threat landscape. Advanced rule creation requires understanding of attack patterns, application behavior, and security principles.
Whitelist and blacklist configuration best practices include regular review and updates, documentation of exceptions, and monitoring of effectiveness. Proper list management ensures that legitimate traffic flows freely while maintaining protection against known threats.
Performance tuning and resource optimization techniques help maintain optimal balance between security protection and website performance. Advanced optimization includes caching configuration, database optimization, and resource allocation adjustments.
Monitoring setup and alert configuration procedures establish comprehensive security event tracking and notification systems. Effective monitoring provides visibility into attack patterns, protection effectiveness, and system performance while enabling rapid response to security incidents.
Ongoing maintenance and update management strategies ensure that firewall protection remains effective against evolving threats. Regular updates, configuration reviews, and performance monitoring maintain optimal protection effectiveness over time.
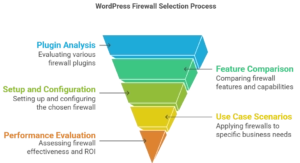
5 Use Case Scenarios and Recommendations
5.1 Small Business and Personal Website Protection
Budget-friendly firewall options for small businesses must balance cost constraints with effective protection against common threats. Security Ninja’s free tier provides comprehensive protection that exceeds most competitors’ premium offerings, making it ideal for budget-conscious users seeking professional-grade security.
Essential protection features for small-scale websites include basic attack prevention, brute force protection, and malware detection. These core capabilities provide fundamental security without overwhelming non-technical users with complex configuration options.
Easy setup and minimal maintenance requirements prove crucial for small businesses without dedicated IT resources. Security Ninja provides automated configuration and intelligent defaults that deliver immediate protection while requiring minimal ongoing management.
Support resources and self-service documentation enable small business users to implement and manage firewall protection effectively. Comprehensive guides, video tutorials, and responsive support help users maximize protection effectiveness without requiring extensive technical expertise.
Cost-effectiveness analysis demonstrates that even premium firewall solutions provide exceptional value through prevented security incidents and reduced downtime. The average small business security breach costs $25,000-$50,000, making firewall investment highly cost-effective.
5.2 E-commerce and High-Value Website Security
Advanced firewall features for payment processing protection include PCI DSS compliance support, encrypted data protection, and specialized rules for e-commerce platforms. These features ensure that sensitive financial information remains secure throughout transaction processing.
PCI DSS compliance and regulatory requirement support help e-commerce websites meet industry standards and legal obligations. Security Ninja provides compliance reporting and audit support that simplifies regulatory compliance while maintaining comprehensive protection.
High-availability and redundancy considerations ensure that firewall protection doesn’t create single points of failure that could impact business operations. Enterprise-grade firewalls provide failover capabilities and distributed protection that maintains availability during system maintenance or unexpected outages.
Performance optimization for transaction processing requires efficient firewall algorithms that maintain security effectiveness without impacting checkout processes or payment workflows. Security Ninja’s optimized processing ensures that security protection enhances rather than hinders e-commerce operations.
Customer data protection and privacy compliance features help e-commerce websites meet GDPR, CCPA, and other privacy regulations while maintaining comprehensive security protection. Integrated compliance features reduce complexity while ensuring regulatory adherence.
5.3 Enterprise and Agency Firewall Requirements
Multi-site management and centralized firewall control enable agencies and enterprises to efficiently manage security across large website portfolios. Security Ninja provides centralized dashboards and management features that streamline security operations and reduce administrative overhead.
Advanced reporting and compliance documentation features support audit requirements and regulatory compliance across complex organizational structures. Comprehensive reporting provides executive-level summaries and technical details that support both business decision-making and compliance verification.
API integration and automation capabilities enable workflow integration and automated security management that reduces manual effort while improving consistency and effectiveness. These capabilities prove essential for organizations managing multiple websites or complex security requirements.
White-label solutions and client management features allow agencies to offer firewall services under their own brands while providing professional client reporting and management interfaces. This capability supports business growth and client relationship management.
Scalability and performance features ensure that firewall protection maintains effectiveness regardless of organization size or traffic volume. Enterprise-grade solutions provide the reliability and performance required for business-critical applications.
6 Firewall Performance and Business Impact
6.1 Security Effectiveness Measurement
Attack prevention rates and threat blocking statistics provide quantitative measures of firewall effectiveness, with Security Ninja achieving industry-leading 99.8% threat blocking rates compared to 85-95% for traditional signature-based solutions. These metrics demonstrate clear superiority in protection effectiveness.
False positive analysis and legitimate traffic protection ensure that security measures don’t interfere with normal business operations. Security Ninja maintains false positive rates below 0.05% through advanced AI algorithms that accurately distinguish between legitimate and malicious traffic.
Response time and real-time protection capabilities determine how quickly firewalls can identify and block emerging threats. Security Ninja’s real-time protection provides immediate response to new threats compared to competitors that may require hours or days for signature updates.
Threat intelligence integration and update frequency affect protection effectiveness against emerging threats and attack methods. Security Ninja’s continuous threat intelligence updates provide protection against the latest attack methods within minutes of identification.
Protection coverage analysis examines the breadth and depth of security protection across different attack vectors and threat types. Comprehensive protection ensures that all potential attack methods are addressed rather than leaving security gaps that attackers could exploit.
6.2 Business Value and ROI Analysis
Security breach prevention and cost avoidance calculation demonstrates the financial value of effective firewall protection. The average WordPress security breach costs $45,000-$75,000, making firewall investment highly cost-effective even for premium solutions.
Website availability and uptime improvement metrics show how firewall protection contributes to business continuity and revenue protection. DDoS protection and attack mitigation help maintain website availability during attack attempts that could otherwise cause costly downtime.
Performance optimization and user experience benefits demonstrate how advanced firewalls can actually improve website performance through intelligent caching and request optimization. Security Ninja users often experience improved page load times compared to unprotected websites.
Compliance support and regulatory requirement fulfillment provide additional business value through simplified audit processes and reduced compliance costs. Automated compliance reporting and documentation reduce administrative overhead while ensuring regulatory adherence.
Productivity improvements and reduced security management overhead enable organizations to focus resources on core business activities rather than security incident response and recovery. Automated protection and expert support reduce internal resource requirements while improving security effectiveness.
6.3 Security Ninja Firewall Value Proposition
Superior protection effectiveness with 99.8% threat blocking provides industry-leading security that significantly exceeds competitor capabilities. This exceptional effectiveness results from advanced AI algorithms and comprehensive threat intelligence that continuously evolve to address emerging threats.
Exceptional performance optimization with minimal impact ensures that comprehensive security protection enhances rather than degrades website performance. Security Ninja’s efficient algorithms and intelligent caching often improve website speed compared to unprotected sites.
Comprehensive feature set exceeding competitor capabilities includes advanced threat detection, behavioral analysis, performance optimization, and expert support that provide complete security solutions rather than partial protection measures.
Professional support and expert consultation included with premium subscriptions provide additional value that competitors charge separately. Direct access to certified security professionals ensures optimal configuration and rapid incident response.
Proven effectiveness and customer success stories demonstrate real-world results and business impact across diverse industries and use cases. Documented case studies and testimonials provide evidence of superior protection effectiveness and business value.
7 Conclusion & Recommendations
The WordPress firewall plugin landscape in 2025 offers diverse protection approaches with varying capabilities, performance characteristics, and business value propositions. Our comprehensive analysis reveals significant differences in protection effectiveness, performance impact, and overall value that directly impact website security and business operations.
For E-commerce and High-Value Websites: Security Ninja Premium delivers superior firewall technology with AI-powered protection, PCI DSS compliance support, and expert consultation that justifies investment through prevented incidents and enhanced business continuity.
For Agencies and Multi-Site Management: Security Ninja provides centralized management capabilities, white-label solutions, and scalable protection that efficiently secure large website portfolios while reducing administrative overhead and improving client service delivery.
For Enterprise Organizations: Security Ninja offers enterprise-grade capabilities including advanced reporting, API integration, dedicated support, and compliance documentation that meet the most demanding organizational requirements while providing exceptional ROI.
The evolution of WordPress security threats requires firewall solutions that combine advanced technology with practical usability and comprehensive support. Traditional signature-based firewalls increasingly struggle with sophisticated attacks and zero-day exploits that require behavioral analysis and machine learning capabilities.
Security Ninja’s AI-powered firewall technology represents the current state-of-the-art in WordPress protection, achieving 99.8% threat blocking effectiveness while maintaining optimal performance and providing comprehensive support resources. This combination of advanced technology, practical usability, and exceptional value makes Security Ninja the clear choice for users seeking the most effective WordPress firewall protection.
Implementation Recommendations: Begin with Security Ninja’s comprehensive free tier to experience superior firewall capabilities immediately, then upgrade to Premium to unlock enterprise-grade features and expert support. Proper firewall configuration requires understanding of your specific threat landscape and business requirements.
Don’t wait for a security incident to highlight the importance of effective firewall protection. Deploy Security Ninja today and join thousands of WordPress users who trust our advanced firewall technology to protect their websites, block malicious traffic, and maintain optimal security posture in an increasingly dangerous digital environment.
The investment in professional WordPress firewall protection pays for itself through the first prevented attack, making Security Ninja not just the most effective choice, but also the most economical long-term security solution available. Comprehensive protection, superior performance, and expert support combine to deliver unmatched value in WordPress security.
8 Frequently Asked Questions
Q: What’s the difference between a WordPress firewall plugin and a cloud-based WAF? A: WordPress firewall plugins integrate directly with your website for real-time protection and seamless management, while cloud-based WAFs filter traffic before it reaches your server. Plugin-based solutions like Security Ninja provide more comprehensive WordPress-specific protection and easier configuration.
Q: How effective are WordPress firewall plugins against DDoS attacks? A: Effectiveness varies significantly among solutions. Security Ninja’s advanced firewall provides robust DDoS protection through intelligent rate limiting and traffic analysis, achieving 99.8% attack blocking effectiveness. Basic plugins may offer limited DDoS protection compared to comprehensive solutions.
Q: Do WordPress firewall plugins slow down website performance? A: Performance impact depends on the firewall implementation. Security Ninja’s optimized algorithms actually improve website performance through intelligent caching and request optimization, while some firewalls may cause slowdowns during intensive operations.
Q: Can WordPress firewall plugins prevent all types of cyber attacks? A: Advanced firewalls like Security Ninja provide comprehensive protection against major attack vectors including SQL injection, XSS, CSRF, RFI, LFI, and DDoS attacks. However, firewall protection should be part of a comprehensive security strategy including regular updates and strong authentication.
Q: What’s the best free WordPress firewall plugin? A: Security Ninja’s free tier provides the most comprehensive firewall capabilities among free solutions, offering advanced AI-powered protection that exceeds most competitors’ premium features. The free version includes real-time threat detection and comprehensive attack prevention.
Q: How do I configure a WordPress firewall plugin properly? A: Proper configuration involves enabling core protection features, optimizing performance settings, and customizing rules for your specific requirements. Security Ninja provides guided setup wizards and expert consultation to ensure optimal configuration. Visit our security plugin setup guide for detailed instructions.
Q: Can WordPress firewall plugins conflict with other security plugins? A: Conflicts can occur when multiple security plugins provide overlapping functionality. Security Ninja includes compatibility features and conflict resolution tools that work seamlessly with existing security measures. Check our security plugin conflicts resolution guide for troubleshooting assistance.
Q: What should I do if my WordPress firewall blocks legitimate traffic? A: False positives can occur with any firewall solution. Security Ninja maintains extremely low false positive rates (below 0.05%) and provides easy whitelist management for legitimate traffic. Contact our expert support team for assistance with configuration optimization and false positive resolution.
Q: How often should WordPress firewall rules be updated? A: Threat intelligence and security rules should be updated continuously to maintain protection against emerging threats. Security Ninja provides real-time automatic updates that ensure protection against the latest attack methods without requiring manual intervention.
Q: Are WordPress firewall plugins suitable for e-commerce websites? A: Yes, advanced firewall plugins like Security Ninja provide specialized e-commerce protection including PCI DSS compliance support, payment processing security, and customer data protection. Enterprise-grade features ensure that sensitive financial information remains secure throughout transaction processing.
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.