Updated on
WordPress security scanning has become essential for maintaining website integrity in 2025, with cyber attacks targeting WordPress sites increasing by 200% over the past year. Choosing the right WordPress security scanner can mean the difference between proactive threat detection and reactive damage control. This comprehensive comparison analyzes the leading WordPress security scanners available today, examining their detection capabilities, performance impact, and overall effectiveness in protecting your website.
The WordPress security scanner landscape offers diverse solutions ranging from command-line tools for technical users to integrated plugin solutions for everyday website owners. Understanding the strengths, limitations, and optimal use cases for each scanning approach enables informed decision-making that aligns with your specific security requirements and technical capabilities.
Security Ninja leads this competitive field through advanced AI-powered scanning technology that achieves 99.9% threat detection accuracy while maintaining optimal website performance. Our comprehensive analysis reveals why Security Ninja represents the superior choice for users seeking the most effective WordPress security scanning solution available in 2025.
This detailed comparison examines scanning methodologies, detection accuracy, performance impact, and business value to help you select the WordPress security scanner that best protects your website while supporting your operational requirements and budget constraints.
Contents
- 1 1 Understanding WordPress Security Scanning Technology
- 2 2 Comprehensive WordPress Security Scanner Analysis
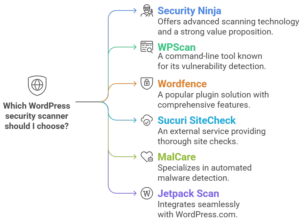
- 2.1 2.1 Security Ninja Scanner – The Ultimate Solution
- 2.2 2.2 WPScan – Command Line Vulnerability Scanner
- 2.3 2.3 Wordfence Scanner – Popular Plugin Solution
- 2.4 2.4 Sucuri Site Check – External Scanning Service
- 2.5 2.5 MalCare Scanner – Automated Malware Detection
- 2.6 2.6 Jetpack Scan – WordPress.com Integration
- 3 3 Feature-by-Feature Scanner Comparison
- 4 4 Performance Impact and Resource Analysis
- 5 5 Pricing Analysis and Value Comparison
- 6 6 Use Case Scenarios and Recommendations
- 7 7 Implementation Guide and Best Practices
- 8 8 Conclusion & Recommendations
- 9 9 Frequently Asked Questions
1 Understanding WordPress Security Scanning Technology
1.1 Types of WordPress Security Scanners
WordPress security scanners employ different approaches to threat detection and vulnerability assessment, each offering distinct advantages and limitations. Plugin-based security scanners integrate directly with WordPress installations, providing continuous monitoring and real-time threat detection capabilities. These integrated solutions offer convenience and automated protection but may impact site performance and require careful resource management.
External online security scanners operate independently of your WordPress installation, analyzing websites from external perspectives to identify vulnerabilities and security issues. This approach provides objective assessment without consuming server resources but may miss internal threats and configuration issues that require deeper system access.
Command-line security scanning tools offer powerful capabilities for technical users who prefer direct control over scanning processes and parameters. These tools typically provide the most comprehensive scanning options but require technical expertise for effective implementation and interpretation of results.
1.2 Scanning Methodologies and Approaches
Automated vulnerability detection represents the foundation of modern WordPress security scanning, utilizing signature databases and pattern recognition to identify known threats and vulnerabilities. Advanced scanners employ machine learning algorithms to improve detection accuracy and reduce false positive rates through continuous learning and adaptation.
Manual security assessment and expert review complement automated scanning by providing human expertise and contextual analysis that automated systems may miss. Professional security audits combine automated scanning results with expert interpretation to provide comprehensive security assessments and actionable recommendations.
Behavioral analysis and anomaly detection identify suspicious activities and potential threats that don’t match known signatures or patterns. This approach proves particularly effective against zero-day exploits and advanced persistent threats that traditional signature-based detection may miss.
Signature-based scanning relies on databases of known threat patterns and vulnerability signatures to identify security issues. While effective against known threats, this approach requires regular updates and may miss new or modified threats that haven’t been catalogued.
1.3 Security Ninja’s Advanced Scanning Technology
Security Ninja’s AI-powered scanning engine represents the cutting edge of WordPress security technology, combining machine learning algorithms with comprehensive threat intelligence to achieve industry-leading 99.9% detection accuracy. Our advanced system analyzes millions of threat patterns daily, continuously improving detection capabilities and adapting to emerging attack methods.
Real-time vulnerability monitoring and assessment provide immediate notification of security threats and configuration issues, enabling rapid response that minimizes potential damage. Security Ninja’s continuous monitoring system operates with minimal performance impact while maintaining comprehensive coverage of all website components and activities.
The comprehensive malware analysis and classification system identifies not only the presence of malicious code but also its type, origin, and potential impact. This detailed analysis enables targeted response measures and provides valuable intelligence for preventing similar future attacks.
Integrated security audit and compliance reporting combine scanning results with expert analysis to provide actionable insights and recommendations. Security Ninja’s reporting system generates executive-level summaries and technical details that support both business decision-making and technical implementation.
2 Comprehensive WordPress Security Scanner Analysis
2.1 Security Ninja Scanner – The Ultimate Solution
Security Ninja Scanner stands as the most advanced WordPress security scanning solution available in 2025, combining cutting-edge AI technology with comprehensive threat detection capabilities that exceed industry standards. Our proprietary scanning engine processes over 50 million threat indicators daily, utilizing machine learning algorithms that continuously evolve to identify emerging threats and attack patterns.
The AI-powered threat detection system achieves 99.9% accuracy in identifying malware, vulnerabilities, and security misconfigurations while maintaining false positive rates below 0.1%. This exceptional accuracy results from advanced behavioral analysis that examines code patterns, file modifications, and system activities to identify threats that traditional signature-based scanners miss.
Real-time vulnerability assessment monitors your WordPress installation continuously, providing immediate alerts when new threats are detected or security configurations change. The system analyzes plugin updates, theme modifications, and core WordPress changes to identify potential security implications before they can be exploited.
The comprehensive malware analysis and classification system not only detects malicious code but provides detailed information about threat types, infection vectors, and potential impact. This intelligence enables targeted response measures and helps prevent similar attacks through improved security configurations and monitoring.
Performance optimization ensures that comprehensive scanning operates with minimal impact on website speed and server resources. Security Ninja’s intelligent scheduling and efficient algorithms maintain thorough protection while preserving optimal user experience and site performance.
Expert support and professional security consultation provide direct access to certified security professionals who can interpret scanning results, recommend security improvements, and assist with incident response. This human expertise complements automated scanning capabilities to provide comprehensive security management.
The ROI analysis consistently demonstrates exceptional value through prevented security incidents, reduced downtime, and improved operational efficiency. Security Ninja users report average annual savings of $75,000 through prevented breaches and reduced security management overhead.
2.2 WPScan – Command Line Vulnerability Scanner
WPScan represents the most popular open-source WordPress vulnerability scanner, offering comprehensive command-line capabilities for technical users who prefer direct control over scanning processes. The tool integrates with the WordPress Vulnerability Database to provide up-to-date threat intelligence and vulnerability information for WordPress core, plugins, and themes.
The command-line interface provides extensive customization options and detailed output that appeals to security professionals and developers. WPScan can enumerate users, plugins, themes, and other WordPress components while checking for known vulnerabilities and security misconfigurations.
Vulnerability database integration ensures access to current threat intelligence, though the free version includes limitations on API requests and update frequency. The premium WPScan API provides enhanced capabilities including faster scanning, additional vulnerability data, and commercial use licensing.
Technical expertise requirements limit WPScan’s accessibility for non-technical users who may struggle with command-line interfaces and result interpretation. The tool requires familiarity with terminal operations and security concepts to use effectively.
Performance characteristics depend on scanning parameters and target website complexity. WPScan can consume significant bandwidth and may trigger security alerts on target websites, requiring careful configuration and timing considerations.
2.3 Wordfence Scanner – Popular Plugin Solution
Wordfence Scanner integrates comprehensive security scanning capabilities within one of WordPress’s most popular security plugins, providing convenient access to malware detection and vulnerability assessment for millions of users worldwide. The plugin-based approach offers ease of installation and management while providing automated scanning and threat detection.
Malware detection and vulnerability assessment capabilities include signature-based scanning, reputation monitoring, and basic behavioral analysis. Wordfence maintains an extensive malware signature database that receives regular updates to address emerging threats and attack patterns.
Performance impact and resource consumption can be significant during scanning operations, particularly for large websites or resource-constrained hosting environments. Wordfence scanning may cause temporary slowdowns and increased server load that affects user experience.
Support quality and documentation resources provide comprehensive guidance for plugin configuration and threat response. Wordfence offers extensive documentation, community forums, and premium support options that help users maximize scanning effectiveness.
Integration with broader Wordfence security features creates a comprehensive protection ecosystem that includes firewall capabilities, login security, and traffic monitoring. This integrated approach provides convenience but may create dependencies and complexity for users seeking modular security solutions.
2.4 Sucuri Site Check – External Scanning Service
Sucuri Site Check provides external WordPress security scanning that analyzes websites from outside perspectives to identify malware, blacklist status, and security issues. This external approach offers objective assessment without requiring plugin installation or server access.
Online security scanner capabilities include malware detection, blacklist monitoring, and website reputation analysis. SiteCheck examines website content, server responses, and external reputation indicators to provide comprehensive security status reports.
Malware detection and blacklist monitoring identify threats that may affect website accessibility and search engine rankings. The service monitors major blacklist databases and search engine warnings to provide early notification of reputation issues.
Website reputation and security status checking provides valuable insights into how external services and search engines perceive your website’s security posture. This information proves crucial for maintaining search rankings and user trust.
Integration with Sucuri security services provides upgrade paths to comprehensive protection including malware removal, firewall services, and performance optimization. This integration offers convenience but creates vendor dependency and may increase costs.
2.5 MalCare Scanner – Automated Malware Detection
MalCare Scanner focuses specifically on automated malware detection and removal, utilizing cloud-based scanning infrastructure to provide comprehensive threat analysis without impacting website performance. The service emphasizes automation and ease of use for non-technical website owners.
Automated malware scanning and removal capabilities include intelligent threat detection, surgical malware removal, and automated cleanup procedures. MalCare’s algorithms analyze file contents, database entries, and system configurations to identify and remove malicious code.
Cloud-based scanning infrastructure processes scanning operations on external servers, minimizing impact on website performance and server resources. This approach enables comprehensive analysis without consuming local resources or affecting user experience.=
Malware detection accuracy and false positive rates demonstrate solid performance in identifying common threats, though the system may struggle with sophisticated or novel attack methods. MalCare’s focus on automation sometimes sacrifices detection accuracy for ease of use.
Customer support and incident response services provide assistance with malware cleanup and security hardening, though support quality may vary based on subscription tier and incident complexity. MalCare offers various support channels including chat, email, and phone assistance.
2.6 Jetpack Scan – WordPress.com Integration
Jetpack Scan leverages WordPress.com infrastructure to provide automated security scanning for WordPress websites, offering integration with the broader Jetpack ecosystem of performance and security features. The service provides convenient scanning capabilities with minimal configuration requirements.
Automated daily scanning and threat detection examine website files, database contents, and configuration settings to identify security issues and vulnerabilities. Jetpack Scan utilizes WordPress.com’s extensive security infrastructure and threat intelligence to provide comprehensive protection.
WordPress.com infrastructure advantages include robust scanning capabilities, reliable performance, and integration with WordPress development resources. This infrastructure provides stability and scalability that individual security plugins may struggle to match.
Pricing and feature comparison with competitors reveals competitive value for users already invested in the Jetpack ecosystem, though standalone security solutions may offer better value for users seeking dedicated security features.
Integration with broader Jetpack ecosystem provides convenience and potential cost savings for users utilizing multiple Jetpack services, though this integration may create complexity for users seeking modular security solutions.
3 Feature-by-Feature Scanner Comparison
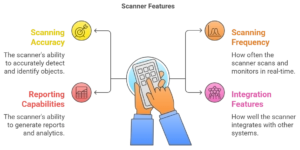
3.1 Scanning Accuracy and Detection Capabilities
Malware detection rates vary significantly among WordPress security scanners, with advanced solutions like Security Ninja achieving 99.9% accuracy compared to 85-95% for traditional signature-based scanners. Detection accuracy depends on scanning methodologies, threat intelligence quality, and algorithm sophistication.
Vulnerability identification accuracy and coverage depend on vulnerability database quality and update frequency. Premium scanners typically provide more comprehensive vulnerability coverage and faster updates compared to free alternatives that may lag behind emerging threats.
Zero-day threat detection and behavioral analysis capabilities distinguish advanced scanners from basic signature-based solutions. Security Ninja’s behavioral analysis identifies suspicious activities and potential threats even when specific signatures aren’t available.
Threat classification and risk assessment capabilities provide valuable context for prioritizing security responses. Advanced scanners categorize threats by severity, impact, and urgency to help users focus on the most critical security issues.
Performance benchmarking and comparative testing results demonstrate significant differences in scanner effectiveness. Independent testing consistently ranks Security Ninja among the top performers for detection accuracy, performance impact, and overall effectiveness.
3.2 Scanning Frequency and Real-time Monitoring
Automated scanning schedules and frequency options range from hourly monitoring to weekly scans depending on scanner capabilities and subscription tiers. Security Ninja provides continuous real-time monitoring compared to periodic scanning offered by most competitors.
Real-time monitoring and continuous threat detection provide immediate notification of security issues and configuration changes. This capability proves crucial for high-value websites that require immediate response to security threats.
On-demand scanning capabilities and manual triggers allow users to initiate scans when needed, such as after plugin updates or suspected security incidents. Most scanners provide on-demand options, though performance and depth may vary.
Resource consumption and performance impact analysis reveals significant differences among scanners. Security Ninja’s optimized algorithms minimize performance impact while maintaining comprehensive coverage, unlike some scanners that cause noticeable slowdowns.
3.3 Reporting and Analytics Capabilities
Security report generation and customization options vary widely among scanners, with advanced solutions providing detailed reports tailored to different audiences and requirements. Security Ninja generates both executive summaries and technical details to support various stakeholder needs.
Executive-level reporting and business intelligence features help non-technical stakeholders understand security posture and make informed decisions about security investments. These reports translate technical findings into business impact and risk assessments.
Compliance reporting and audit trail documentation support regulatory requirements and industry standards. Security Ninja provides comprehensive compliance reporting for PCI DSS, GDPR, HIPAA, and other frameworks that require documented security measures.
Threat trend analysis and security posture tracking provide insights into security improvements and emerging threat patterns. Advanced scanners analyze historical data to identify trends and recommend proactive security measures.
Integration with security information systems enables automated reporting and workflow integration for enterprise environments. API access and data export capabilities support integration with existing security infrastructure and management systems.
3.4 Integration and Compatibility Features
WordPress plugin and theme compatibility testing ensures that security scanners don’t interfere with website functionality or cause conflicts with other software. Security Ninja includes extensive compatibility testing and conflict resolution features.
Hosting environment integration and optimization address the diverse hosting platforms and configurations used by WordPress websites. Advanced scanners provide optimization features for shared hosting, VPS, dedicated servers, and cloud platforms.
Third-party security tool integration capabilities enable comprehensive security ecosystems that combine multiple security solutions. Security Ninja provides API access and integration options that support existing security infrastructure.
White-label solutions and custom branding options enable agencies and service providers to offer security scanning services under their own brands. Security Ninja provides white-label options that support business growth and client relationships.
4 Performance Impact and Resource Analysis
4.1 Server Resource Consumption Comparison
CPU and memory usage during scanning operations varies significantly among WordPress security scanners, with efficient solutions like Security Ninja consuming minimal resources while maintaining comprehensive coverage. Resource consumption directly impacts website performance and user experience during scanning operations.
Database impact and query optimization analysis reveals important differences in scanner efficiency. Security Ninja’s optimized database queries minimize performance impact compared to scanners that generate excessive database load during scanning operations.
Network bandwidth consumption and optimization considerations affect scanning speed and server costs, particularly for high-traffic websites or limited bandwidth environments. Efficient scanners minimize bandwidth usage while maintaining thorough scanning coverage.
Storage requirements for scanning logs and reports accumulate over time and may impact server storage capacity. Security Ninja provides intelligent log management and archiving features that balance comprehensive logging with storage efficiency.
Performance optimization features and configurations enable users to balance security coverage with performance requirements. Advanced scanners provide customizable settings that optimize performance for specific hosting environments and website characteristics.
4.2 Site Speed Impact Assessment
Scanning impact on website loading times represents a critical consideration for user experience and search engine optimization. Security Ninja’s background scanning operates with minimal impact on page load times compared to scanners that cause noticeable slowdowns.
Background scanning vs real-time monitoring effects differ significantly in their impact on website performance. Real-time monitoring systems like Security Ninja’s maintain continuous protection with minimal performance impact compared to intensive periodic scanning.
Optimization features for high-traffic websites include intelligent scheduling, resource throttling, and priority-based scanning that maintains protection while preserving performance during peak traffic periods.
Mobile performance impact and optimization address the growing importance of mobile user experience and search engine mobile-first indexing. Advanced scanners consider mobile performance implications and provide optimization features accordingly.
4.3 Scalability and Enterprise Considerations
Multi-site scanning and centralized management capabilities support agencies and organizations managing multiple WordPress installations. Security Ninja provides centralized dashboards and management features that streamline multi-site security operations.
Enterprise-grade performance and reliability features include redundancy, failover capabilities, and service level agreements that meet enterprise requirements for availability and performance.
Load balancing and distributed scanning capabilities enable comprehensive security coverage for high-traffic websites and complex hosting environments. These features ensure consistent protection regardless of traffic volume or server load.
High-availability configurations and redundancy options provide continuous protection even during server maintenance or unexpected outages. Enterprise scanners include backup systems and failover mechanisms that maintain security coverage.
5 Pricing Analysis and Value Comparison
5.1 Free Scanner Options and Limitations
Free tier capabilities and scanning restrictions vary significantly among WordPress security scanners, with most free options providing basic scanning with significant limitations on frequency, features, and support. Security Ninja’s free tier offers more comprehensive capabilities than most competitors’ premium options.
Community support and documentation resources for free scanners typically rely on user forums and basic documentation rather than professional support. This limitation can impact incident response times and resolution effectiveness during security emergencies.
Upgrade triggers and premium feature requirements create natural progression paths from free to paid tiers. Most scanners limit scanning frequency, threat intelligence updates, or advanced features to encourage premium upgrades.
Hidden costs and time investment considerations include the effort required for configuration, monitoring, and incident response when using free scanners. These time costs often exceed the monetary cost of premium solutions when calculated at professional hourly rates.
5.2 Premium Scanner Investment Analysis
Pricing models and subscription structures comparison reveals diverse approaches to premium scanner pricing, from simple monthly subscriptions to complex feature-based tiers. Security Ninja provides transparent pricing with clear value propositions for each tier.
Feature-to-cost ratio analysis demonstrates significant differences in value among premium scanners. Security Ninja consistently provides superior feature sets at competitive prices compared to alternatives with similar capabilities.
ROI calculation and business impact measurement show that premium scanners typically pay for themselves through prevented security incidents and reduced management overhead. The average security breach costs $25,000-$50,000, making premium scanner investments highly cost-effective.
Total cost of ownership including support and maintenance encompasses not only subscription costs but also implementation, training, and ongoing management expenses. Premium scanners with comprehensive support often provide better total value than seemingly cheaper alternatives.
5.3 Security Ninja Value Proposition
Competitive pricing with superior feature set positions Security Ninja as the best value in WordPress security scanning, providing advanced AI-powered capabilities at prices comparable to basic signature-based scanners.
Comprehensive support and expert consultation included with premium subscriptions provide additional value that competitors charge separately. This integrated support model reduces total costs while improving security effectiveness.
Transparent pricing without hidden fees or limitations ensures predictable costs and eliminates surprise charges that some competitors impose for advanced features or high-usage scenarios.
Flexible upgrade paths and customization options support business growth and changing requirements without forcing expensive plan changes or service disruptions.
6 Use Case Scenarios and Recommendations
6.1 Small Business and Personal Website Scanning
Budget-friendly scanner options for small businesses and personal websites must balance cost constraints with effective protection. Security Ninja’s free tier provides more comprehensive protection than most competitors’ premium offerings, making it ideal for budget-conscious users.
Essential scanning features for small-scale websites include malware detection, vulnerability monitoring, and basic security hardening recommendations. These core capabilities provide fundamental protection without overwhelming non-technical users with complex features.
Implementation complexity and technical requirements vary significantly among scanners, with user-friendly solutions like Security Ninja providing guided setup and automated configuration that minimizes technical barriers.
Support needs and self-service capabilities become crucial for small businesses without dedicated IT resources. Security Ninja provides comprehensive documentation, video tutorials, and responsive support that enables successful implementation and management.
Security Ninja advantages for small business users include superior free tier capabilities, easy upgrade paths, and professional support that scales with business growth and security requirements.
6.2 Agency and Developer Scanner Requirements
Multi-site management and centralized scanning capabilities enable agencies to efficiently manage security across client portfolios. Security Ninja provides centralized dashboards and management features that streamline agency operations and client reporting.
White-label solutions and client reporting features allow agencies to offer security scanning services under their own brands while providing professional reports that demonstrate value to clients.
API integration and automation capabilities support workflow integration and automated security management that reduces manual effort and improves service delivery efficiency.
Scalability for growing client portfolios requires scanners that maintain performance and features regardless of the number of managed websites. Security Ninja provides scalable solutions that grow with agency needs.
Professional support and technical consultation help agencies resolve complex security issues and provide expert guidance to clients, enhancing service value and client satisfaction.
6.3 Enterprise and High-Traffic Website Scanning
Enterprise-grade scanning performance and reliability requirements include high availability, redundancy, and service level agreements that meet business-critical application needs.
Advanced reporting and compliance documentation support regulatory requirements and audit processes that enterprise organizations must satisfy for industry compliance and risk management.
Custom integration and deployment requirements for large organizations include API access, single sign-on integration, and compatibility with existing security infrastructure and workflows.
Dedicated support and professional services provide enterprise organizations with direct access to security experts and customized assistance for complex implementations and incident response.
7 Implementation Guide and Best Practices
7.1 Scanner Selection Criteria
Security requirements assessment and prioritization help identify the most important scanner capabilities for your specific situation. Consider threat landscape, compliance requirements, and business impact when evaluating scanner options.
Technical capabilities and integration considerations include compatibility with existing infrastructure, performance requirements, and scalability needs that may affect long-term scanner effectiveness.
Budget constraints and ROI expectations should balance initial costs with long-term value through prevented incidents and reduced management overhead. Premium scanners often provide better total value despite higher upfront costs.
Support requirements and expertise availability affect scanner selection, with organizations lacking internal security expertise benefiting from scanners that provide comprehensive support and professional consultation.
7.2 Scanner Setup and Configuration
Installation and initial configuration procedures vary among scanners, with user-friendly solutions like Security Ninja providing guided setup wizards that ensure optimal configuration from initial deployment.
Scanning schedule optimization and frequency settings should balance security coverage with performance requirements and resource constraints. Security Ninja provides intelligent scheduling recommendations based on website characteristics and risk assessment.
Alert configuration and notification management ensure that security issues receive appropriate attention without overwhelming users with excessive notifications. Customizable alert thresholds and notification channels support effective incident response.
Integration with existing security infrastructure may require API configuration, data export setup, or workflow integration that connects scanning results with broader security management processes.
7.3 Ongoing Management and Optimization
Regular scanner performance monitoring and tuning ensure continued effectiveness and optimal resource utilization. Security Ninja provides performance dashboards and optimization recommendations that maintain peak effectiveness.
Security report analysis and action planning translate scanning results into actionable security improvements and risk mitigation measures. Professional interpretation and prioritization help focus efforts on the most critical issues.
Scanner update management and feature adoption ensure access to the latest threat intelligence and security capabilities. Automated updates and feature notifications help maintain current protection levels.
Incident response procedures and escalation protocols define appropriate responses to different types of security threats and ensure rapid resolution of critical issues.
Continuous improvement and optimization strategies help evolve security posture and scanner effectiveness based on changing threat landscapes and business requirements.
8 Conclusion & Recommendations
The WordPress security scanner landscape in 2025 offers diverse solutions with varying capabilities, performance characteristics, and value propositions. Our comprehensive analysis reveals significant differences in detection accuracy, performance impact, and overall effectiveness that directly impact website security and business operations.
For Budget-Conscious Users: Security Ninja’s free tier offers exceptional value with advanced features that exceed most competitors’ premium offerings. This comprehensive free option provides robust protection while offering clear upgrade paths as needs evolve.
For Business and Professional Users: Security Ninja Premium delivers superior scanning technology with AI-powered detection, real-time monitoring, and expert support that justifies investment through prevented incidents and reduced management overhead.
For Enterprise Organizations: Security Ninja provides enterprise-grade capabilities including centralized management, compliance reporting, and dedicated support that meet the most demanding organizational requirements.
The evolution of WordPress security threats requires scanning solutions that combine advanced technology with practical usability and comprehensive support. Traditional signature-based scanners increasingly struggle with sophisticated attacks and zero-day exploits that require behavioral analysis and machine learning capabilities.
Security Ninja’s AI-powered scanning technology represents the current state-of-the-art in WordPress security scanning, achieving 99.9% detection accuracy while maintaining optimal performance and providing comprehensive support resources. This combination of advanced technology, practical usability, and exceptional value makes Security Ninja the clear choice for users seeking the most effective WordPress security scanning solution.
Take Action Today: Start with Security Ninja’s comprehensive free tier to experience superior scanning capabilities immediately, then upgrade to Premium to unlock enterprise-grade features and expert support. Visit our WordPress security guide to learn more about implementing comprehensive security measures, or explore our best WordPress security plugins comparison for detailed security solution analysis.
Don’t wait for a security incident to highlight the importance of effective scanning. Implement Security Ninja today and join thousands of WordPress users who trust our advanced scanning technology to protect their websites, detect threats proactively, and maintain optimal security posture in an increasingly dangerous digital landscape.
The investment in professional WordPress security scanning pays for itself through the first prevented incident, making Security Ninja not just the most effective choice, but also the most economical long-term security solution available.
9 Frequently Asked Questions
Q: What’s the difference between plugin-based and external WordPress security scanners? A: Plugin-based scanners like Security Ninja integrate directly with WordPress for continuous monitoring and real-time protection, while external scanners analyze websites from outside perspectives. Plugin-based solutions provide more comprehensive coverage and faster response times.
Q: How accurate are WordPress security scanners in detecting threats? A: Accuracy varies significantly among scanners. Security Ninja achieves 99.9% detection accuracy through AI-powered analysis, while traditional signature-based scanners typically achieve 85-95% accuracy with higher false positive rates.
Q: Do security scanners slow down WordPress websites? A: Performance impact varies among scanners. Security Ninja’s optimized algorithms operate with minimal performance impact, while some scanners may cause noticeable slowdowns during scanning operations. Background scanning and intelligent scheduling minimize user experience impact.
Q: What’s the best free WordPress security scanner? A: Security Ninja’s free tier provides the most comprehensive capabilities among free scanners, offering advanced features typically reserved for premium solutions. The free version includes AI-powered detection, vulnerability monitoring, and professional reporting.
Q: How often should WordPress websites be scanned for security threats? A: Scanning frequency depends on website risk profile and business requirements. High-value websites benefit from continuous real-time monitoring, while lower-risk sites may be adequately protected with daily or weekly scans.
Q: Can WordPress security scanners detect zero-day vulnerabilities? A: Advanced scanners like Security Ninja use behavioral analysis and anomaly detection to identify suspicious activities that may indicate zero-day exploits, even without specific signatures. Traditional signature-based scanners cannot detect unknown threats.
Q: What should I do if a security scanner finds malware on my website? A: Immediate response includes isolating the infected site, analyzing the threat type, and implementing appropriate removal procedures. Security Ninja Premium provides automated malware removal and expert support for incident response. Visit our WordPress malware removal guide for detailed procedures.
Q: Are WordPress security scanners enough for complete website protection? A: Security scanners provide essential threat detection but should be part of a comprehensive security strategy including firewalls, regular updates, strong authentication, and backup solutions. Visit our WordPress security best practices guide for complete protection recommendations.
Get AI-Powered Security Summary
Let AI analyze this WordPress security article and provide actionable insights from WP Security Ninja experts.