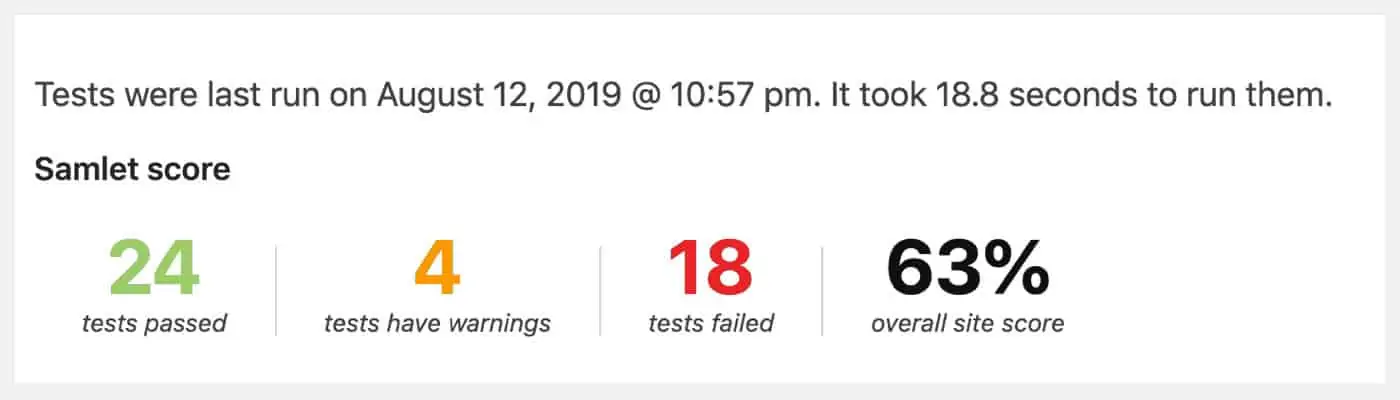
You do not score 100% when running security tests? Do not worry, this is normal.
The tests being done checks for a wide range of potential issues, and it is not always possible to be 100% protected.
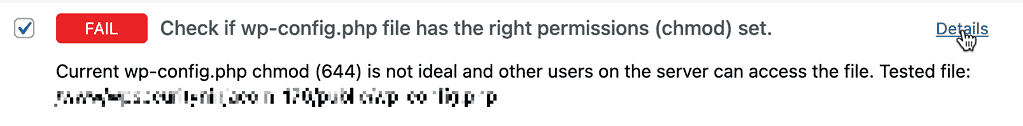
A test has failed!
Next to each test there is a “Details” button, when clicked will open with more details about the issue as well as suggested options.
Warnings are just warnings
For instance, the plugin checks the current version of MySQL – the software that runs your website database. If you are just running the minimum version 5.5.60 (at the time of this writing), it is enough, but it is recommended you run at least v5.6.
Depending on where you are hosted this can be difficult to get changed as the host might have to change this setting for a lot of sites to accommodate you.
This is not really a big issue, but the plugin will still warn you.
A failed test do not mean you will be hacked
Although you might get worried about the tests that save they have failed, but read the individual test results before you get too worried. Every website is different and have different needs for features to be enabled.
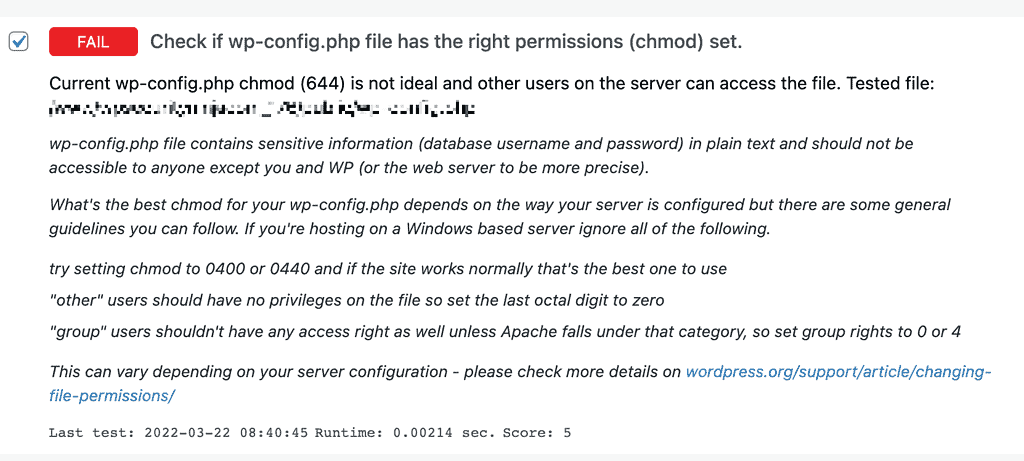
For instance the wp-config.php file. Every file and folder on your webserver can be set to have different rights for different users. So for instance only specific users can view or edit. If the right permissions are not set, some sensitive details could be read by different users.
This is not possible to set on all webhosts, some hosting companies require different permissions to function properly. There are other ways to prevent unwanted access to the file, without modifying the file permissions.
So, read the details and keep in mind some things are not possible to disable due to how your website is set up or the functionality needed.
For instance, the test checking if your response headers contain Content Security Policy can be hard to configure. This would require someone with experience to set up properly as making a mistake with the CSP can break functionality on your website.
https://wpsecurityninja.com/docs/security-fixes/security-headers/#content-security-policy-csp
Serious issues
You should pay attention to the issues that you can do something about.
Example – remove default “admin” account
Issues such as using the default username, “admin” still exist is a more serious issue.
Even if you use a very secure password, you are still open to login attempts which at the minimum put more strain on your server.
The process is simple enough, you create a new administrator account with a new username and then delete the user with “admin” – read the details in the test description for more details.
Example – Do not use the default database prefix
To group your installation database tables together, your WordPress will have a prefix that all tables in your database begin with, the default is “wp_”. You can ensure a lot of standard attacks will have no success just by changing the default prefix.
Many attempts to insert malicious code into your website will be by filling out a form and then trying to inject MySQL code that way. Most scripts will attempt to use the default prefix “wp_” – by having a different prefix you will have thwarted those attempts.